WMCTF2023
WMCTF2023(复现)
MISC
Checkin
WMCTF{Welcome_W&MCTF_2023!}Fantastic terminal
cat challenge
#WMCTF{fanta3t1c_term1nal_1n_the_c0nta1ner_1n_the_br0w3er}Fantastic terminal Rev
把程序base64 dump下来分析
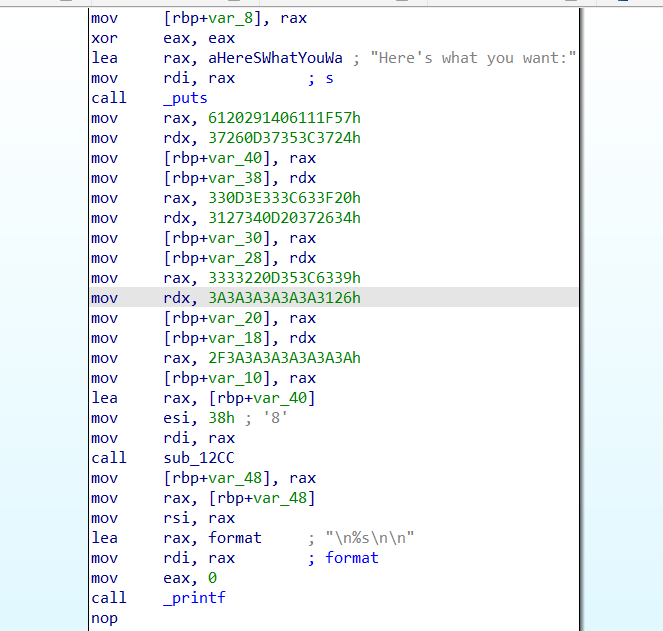
c = '''6120291406111F57
37260D37353C3724
330D3E333C633F20
3127340D20372634
3333220D353C6339
3A3A3A3A3A3A3126
2F3A3A3A3A3A3A3A'''
c = c.split('\\n')
c = [i for i in c]
e = []
flag =''
for i in c:
d = []
for j in range(len(i)//2):
d.append(chr(int(i[j*2:j*2+2],16)^0x52))
d.reverse()
for j in d:
flag+=j
# e.append(d)
print(flag)
#WMCTF{r3venge_term1nal_after_fuck1ng_paatchhhhhhhhhhhhh}Oversharing
导出SMB对象,保存dmp文件,使用minikatz分析获取ssh连接的密码
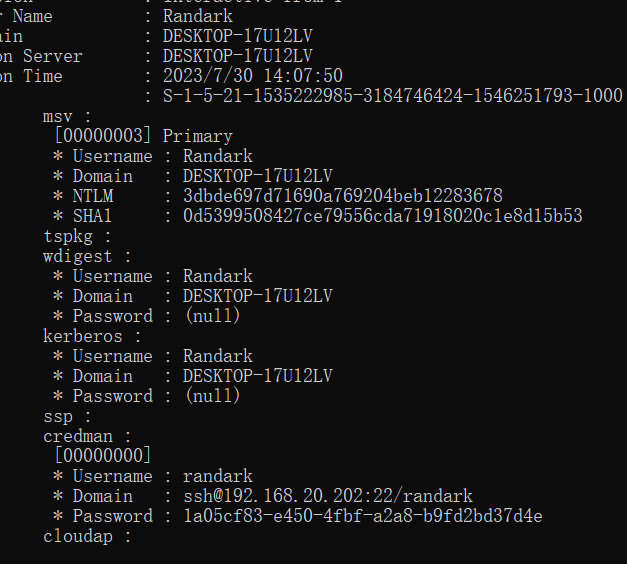
看到ssh的password,ssh randark@题目环境 -p 端口
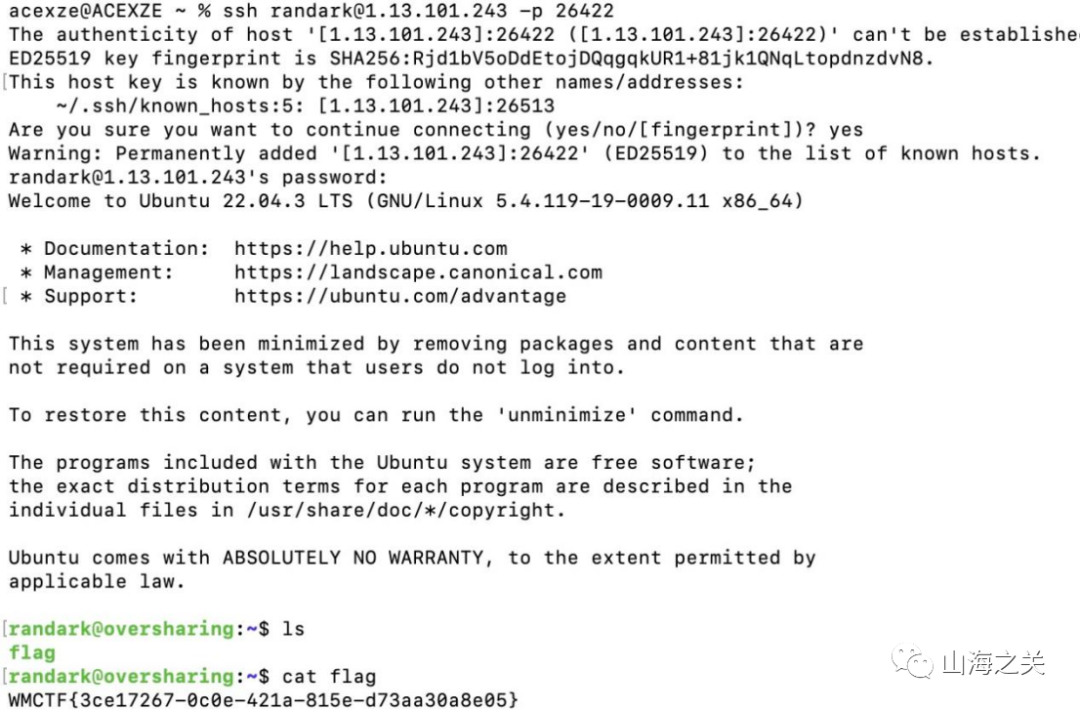
然后获取flag
find me
题目描述前往Reddit寻找WearyMeadow
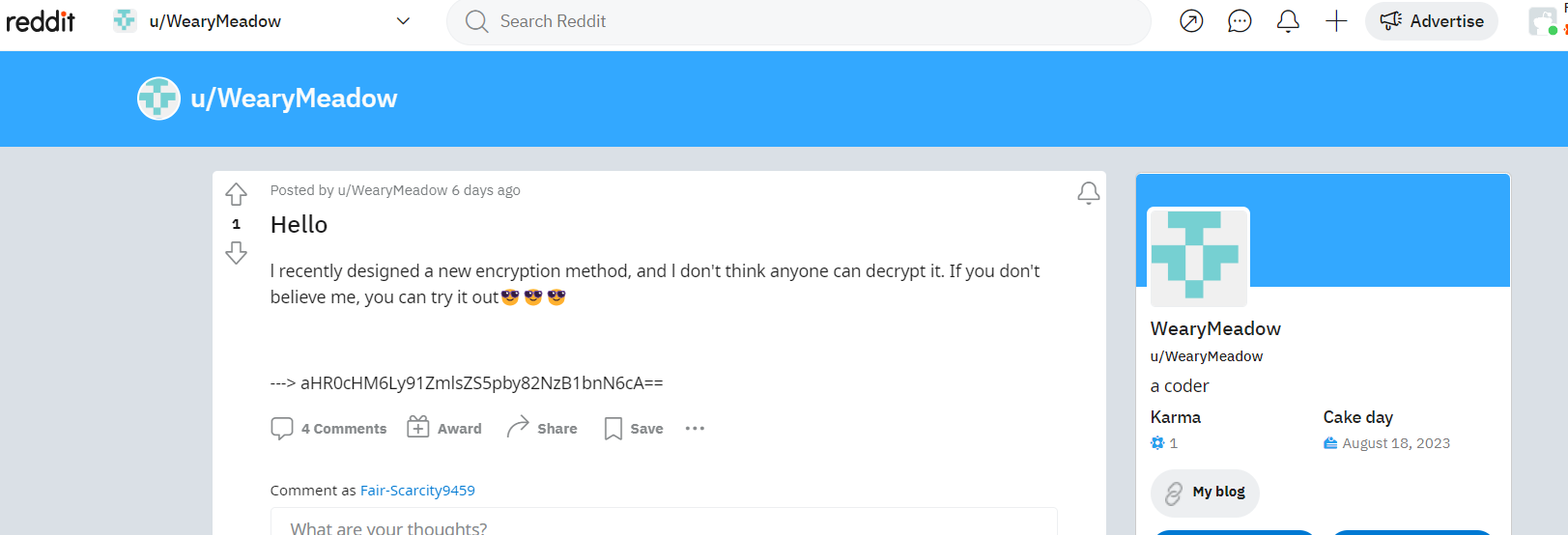
aHR0cHM6Ly91ZmlsZS5pby82NzB1bnN6cA==
#https://ufile.io/670unszp (流量包下载链接)用户有个my blog连接,
文章打开需要密码
WearyMeadow在Rebbit的头像为github的初始头像,于是到github.com上搜索该用户
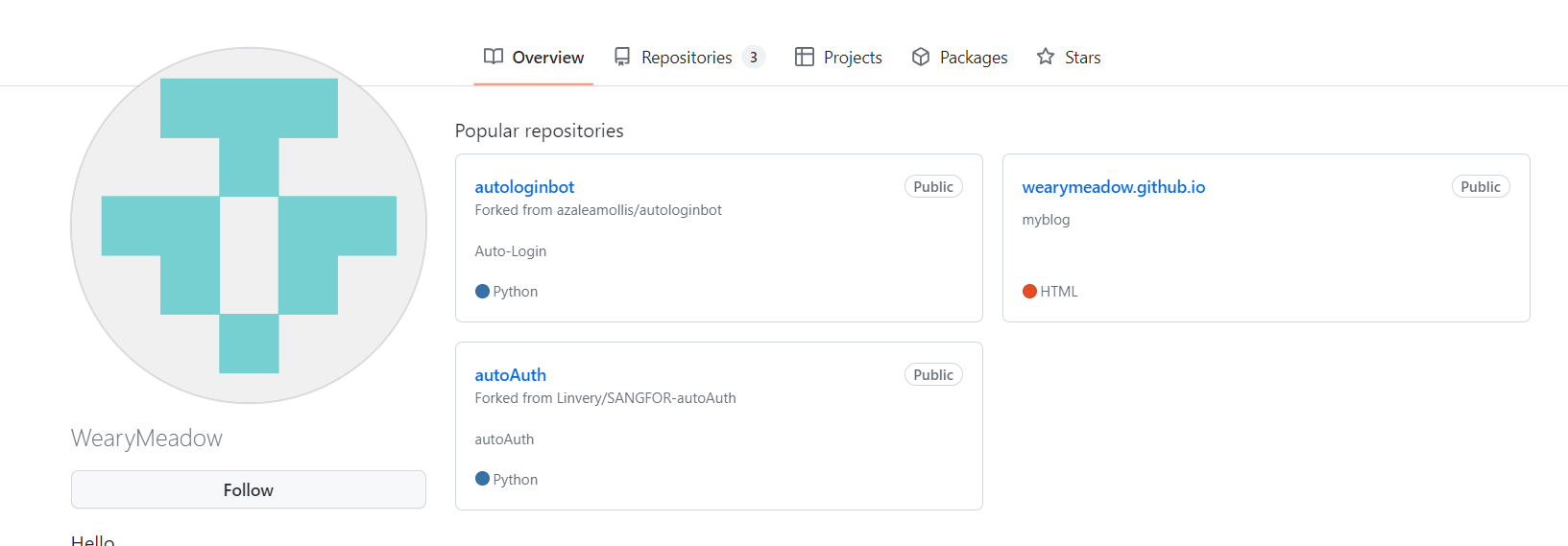
发现两个自动登录脚本,打开后发现密码
usernameStr = 'WearyMeadow'
passwordStr = 'P@sSW0rD123$%^'尝试用密码打开文章,成功解密,得到了server.py与client.py
分析逻辑写出decrypt函数的代码,(缺少key和数据)
wireshark分析流量包
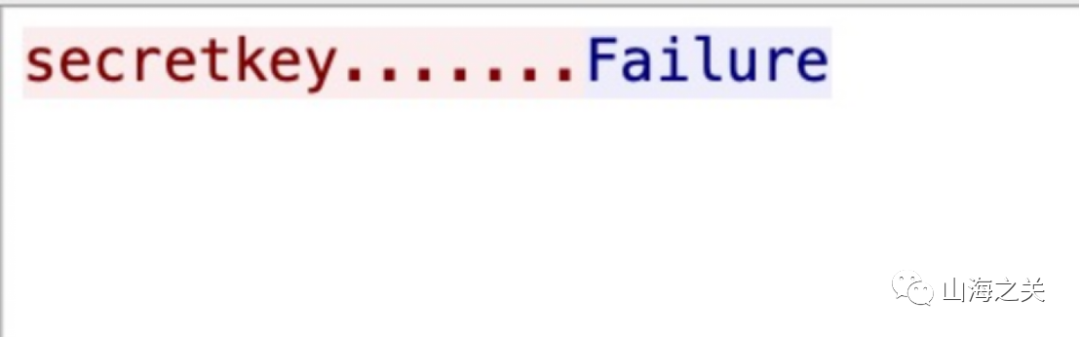

说明key为mysecretkey,然后将该数据转化为原始数据
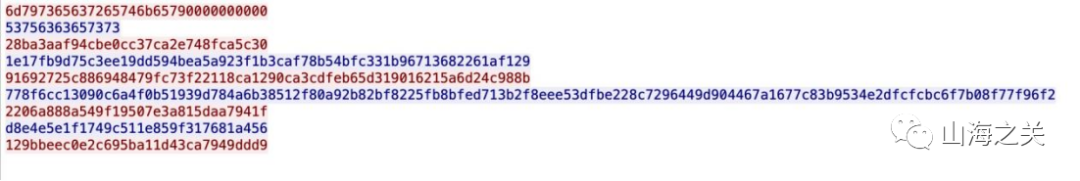
最长的一串应该还有flag信息
import socket
import random
from Crypto.Cipher import AES
from sys import argv
import binascii
def pad(s):
return s + b"\0" * (AES.block_size - len(s) % AES.block_size)
def encrypt(message, key):
seed = random.randint(0, 11451)
random.seed(seed)
encrypted = b''
for i in range(len(message)):
encrypted += bytes([message[i] ^ random.randint(0, 255)])
cipher = AES.new(key, AES.MODE_ECB)
encrypted = cipher.encrypt(pad(encrypted))
return encrypted
key = b'mysecretkey'.ljust(16,b'\x00')
print(key)
hex_ciphertext = "778f6cc13090c6a4f0b51939d784a6b38512f80a92b82bf8225fb8bfed713b2f8eee53dfbe228c7296449d904467a1677c83b9534e2dfcfcbc6f7b08f77f96f2"
ciphertext = binascii.unhexlify(hex_ciphertext)
cipher = AES.new(key, AES.MODE_ECB)
decrypted_data = cipher.decrypt(ciphertext)
print(decrypted_data)
unpadded = decrypted_data.rstrip(b'\x00')
print(unpadded)
print()
for i in range(11451): #爆破种子
seed = i
random.seed(seed)
original_message = b''
for j in range(len(unpadded)):
original_message += bytes([unpadded[j] ^ random.randint(0, 255)])
# print(original_message)
if b'WMCTF' in original_message:
print(original_message)
#b'well, here you are: WMCTF{OH_Y0u_f1nd_Me__(@_@)}'WMCTF2023
https://zer0peach.github.io/2023/08/24/WMCTF2023/