0xGame2023 Re 刷题
0xGame2023 Re
Week1
代码金丹
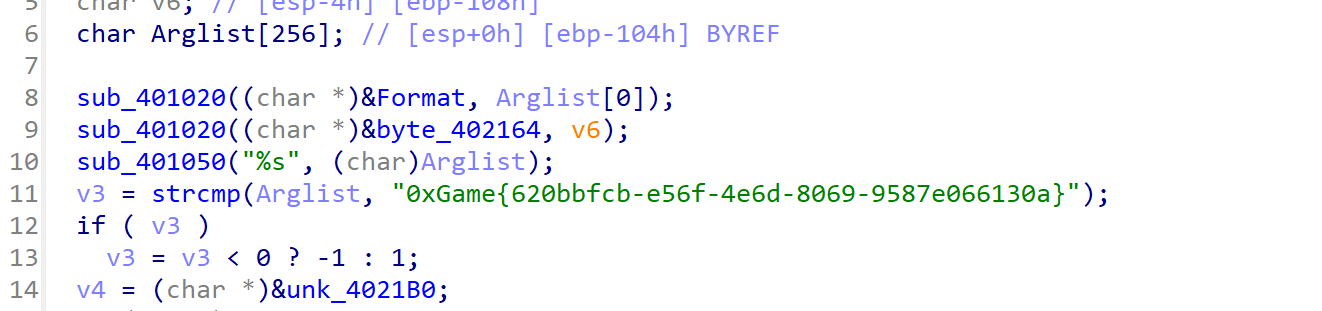
数字筑基
网络元婴
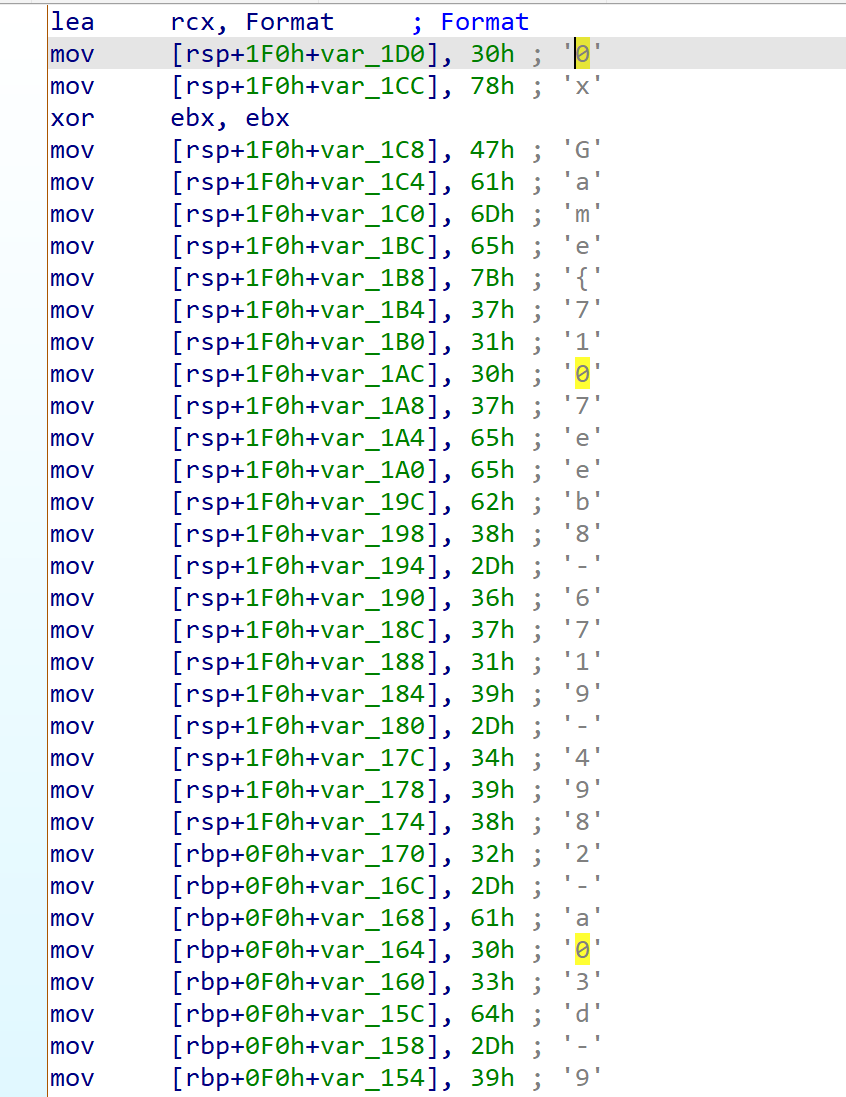
直接看到,或者反编译然后python转ascii
v6 = [0]*43
v6[0]=48
v6[1]=120
v6[2]=71
v6[3]=97
v6[4]=109
v6[5]=101
v6[6]=123
v6[7]=55
v6[8]=49
v6[9]=48
v6[10]=55
v6[11]=101
v6[12]=101
v6[13]=98
v6[14]=56
v6[15]=45
v6[16]=54
v6[17]=55
v6[18]=49
v6[19]=57
v6[20]=45
v6[21]=52
v6[22]=57
v6[23]=56
v6[24]=50
v6[25]=45
v6[26]=97
v6[27]=48
v6[28]=51
v6[29]=100
v6[30]=45
v6[31]=57
v6[32]=56
v6[33]=53
v6[34]=51
v6[35]=48
v6[36]=51
v6[37]=51
v6[38]=53
v6[39]=100
v6[40]=102
v6[41]=57
v6[42]=51
print(v6)
for i in v6:
print(chr(i),end='')
# 0xGame{7107eeb8-6719-4982-a03d-98530335df93虚拟化神
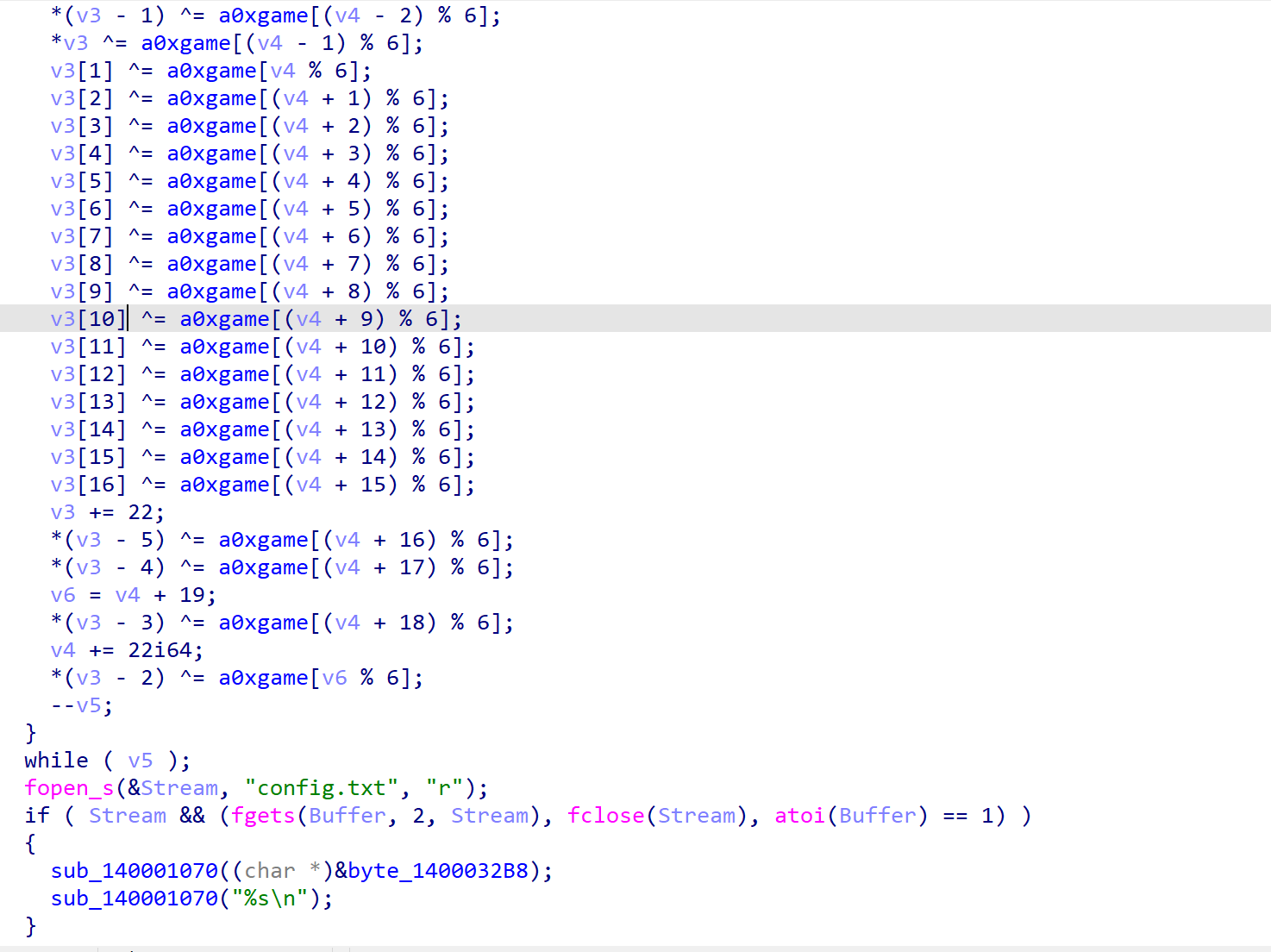
读取判断前两个字符然后转为整数与1比较
后面else的逻辑是读啥然后写入config.txt,我们手动修改生成的config.txt内容
然后再次运行即可
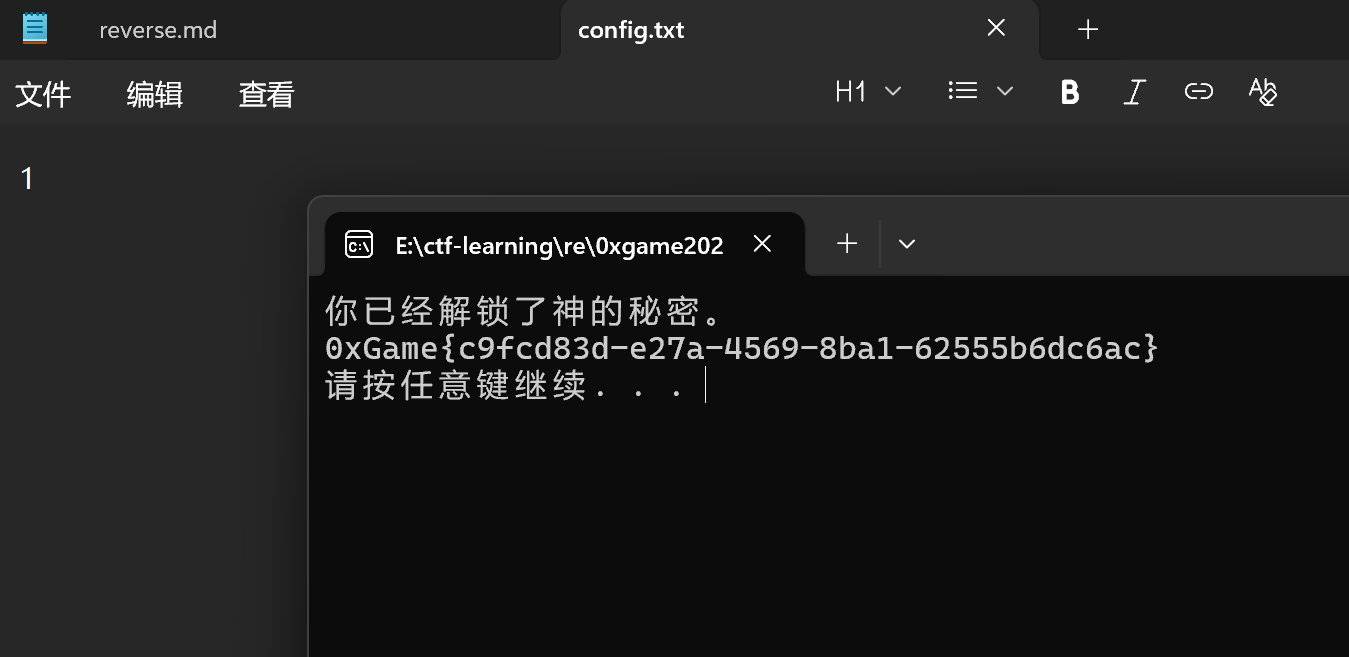
(也可以动态调试)
赛博天尊
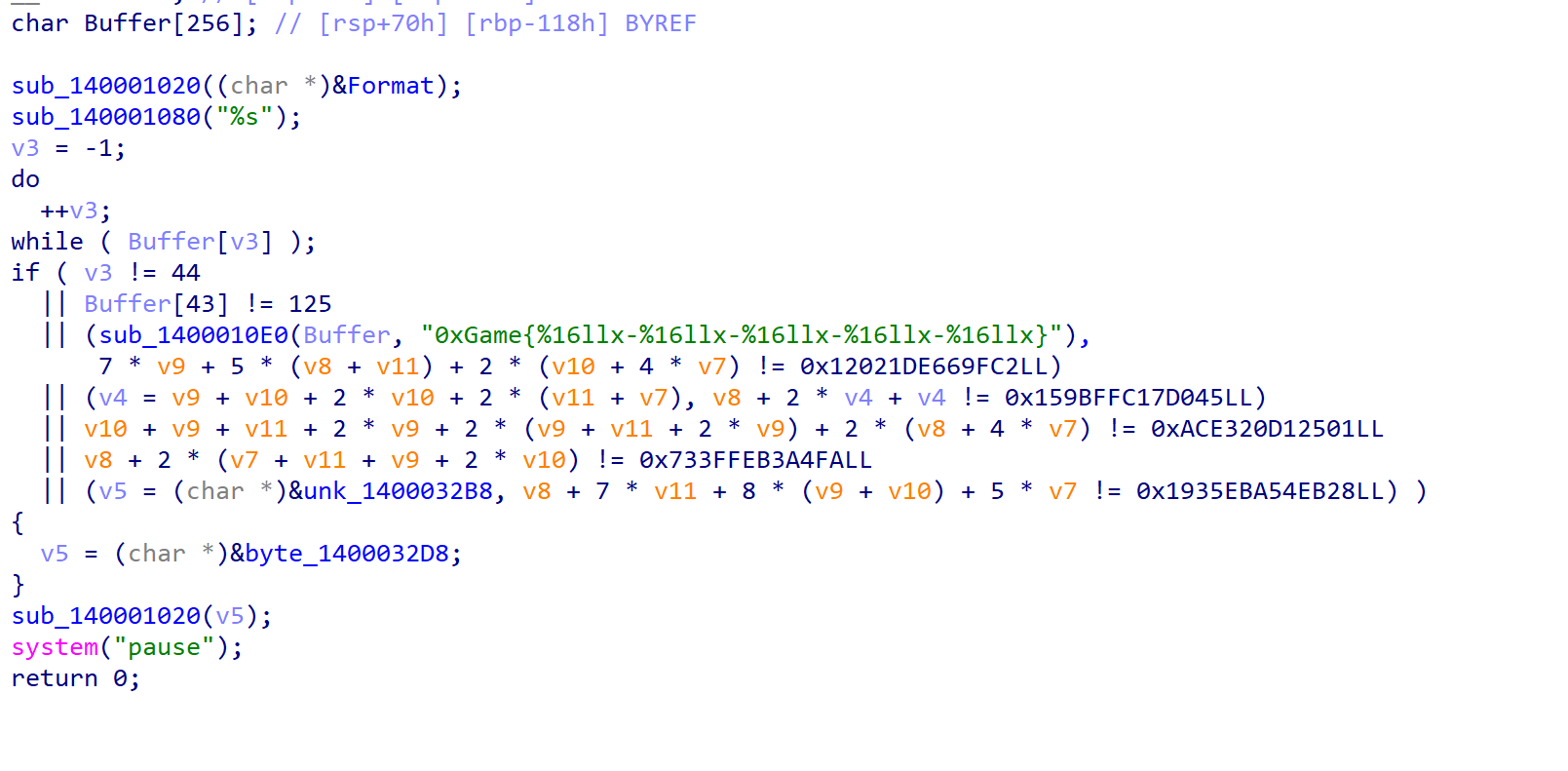
多个表达式,z3求解,然后是16进制填入
from z3 import *
v7 = Int('v7')
v8 = Int('v8')
v9 = Int('v9')
v10 = Int('v10')
v11 = Int('v11')
# 创建求解器
s = Solver()
# 约束1: 7 * v9 + 5 * (v8 + v11) + 2 * (v10 + 4 * v7) = 0x12021DE669FC2
s.add(7 * v9 + 5 * (v8 + v11) + 2 * (v10 + 4 * v7) == 0x12021DE669FC2)
# 约束2: v8 + 2 * v4 + v4 = 0x159BFFC17D045
# 其中 v4 = v9 + v10 + 2 * v10 + 2 * (v11 + v7)
v4 = v9 + v10 + 2 * v10 + 2 * (v11 + v7)
s.add(v8 + 2 * v4 + v4 == 0x159BFFC17D045)
# 约束3: v10 + v9 + v11 + 2 * v9 + 2 * (v9 + v11 + 2 * v9) + 2 * (v8 + 4 * v7) = 0xACE320D12501
# 简化:v10 + v9 + v11 + 2*v9 + 2*(v9 + v11 + 2*v9) + 2*(v8 + 4*v7)
# = v10 + v9 + v11 + 2*v9 + 2*v9 + 2*v11 + 4*v9 + 2*v8 + 8*v7
# = v10 + 9*v9 + 3*v11 + 2*v8 + 8*v7
s.add(v10 + v9 + v11 + 2 * v9 + 2 * (v9 + v11 + 2 * v9) + 2 * (v8 + 4 * v7) == 0xACE320D12501)
# 约束4: v8 + 2 * (v7 + v11 + v9 + 2 * v10) = 0x733FFEB3A4FA
s.add(v8 + 2 * (v7 + v11 + v9 + 2 * v10) == 0x733FFEB3A4FA)
# 约束5: v8 + 7 * v11 + 8 * (v9 + v10) + 5 * v7 = 0x1935EBA54EB28
s.add(v8 + 7 * v11 + 8 * (v9 + v10) + 5 * v7 == 0x1935EBA54EB28)
# 检查是否有解
if s.check() == sat:
m = s.model()
print("找到解:")
# 获取每个变量的值
v7_val = m[v7].as_long()
v8_val = m[v8].as_long()
v9_val = m[v9].as_long()
v10_val = m[v10].as_long()
v11_val = m[v11].as_long()
flag = f"0xGame{{{hex(v7_val)[2:]}-{hex(v8_val)[2:]}-{hex(v9_val)[2:]}-{hex(v10_val)[2:]}-{hex(v11_val)[2:]}}}"
print(f"\nFlag: {flag}")
else:
print("无解")Week2
编译逆旅者
pyc,在线反编译
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.11
import binascii
def main():
flag = binascii.unhexlify(hex(0x307847616D657B63646539646331372D356133312D356330612D646633342D3663373562373634366334627D)[2:].encode())
user_input = input('请输入一个秘密的数字:')
if not len(user_input) != 13 or user_input.isdigit():
print('无效输入。必须是13位数字。')
return None
if None == '1145141919810':
print(f'''真理的旗帜:{flag}''')
return None
None('秘密的数字错误!')
if __name__ == '__main__':
main()
return None
import binascii
flag = binascii.unhexlify(hex(0x307847616D657B63646539646331372D356133312D356330612D646633342D3663373562373634366334627D)[2:].encode())
print(flag)注册侦探
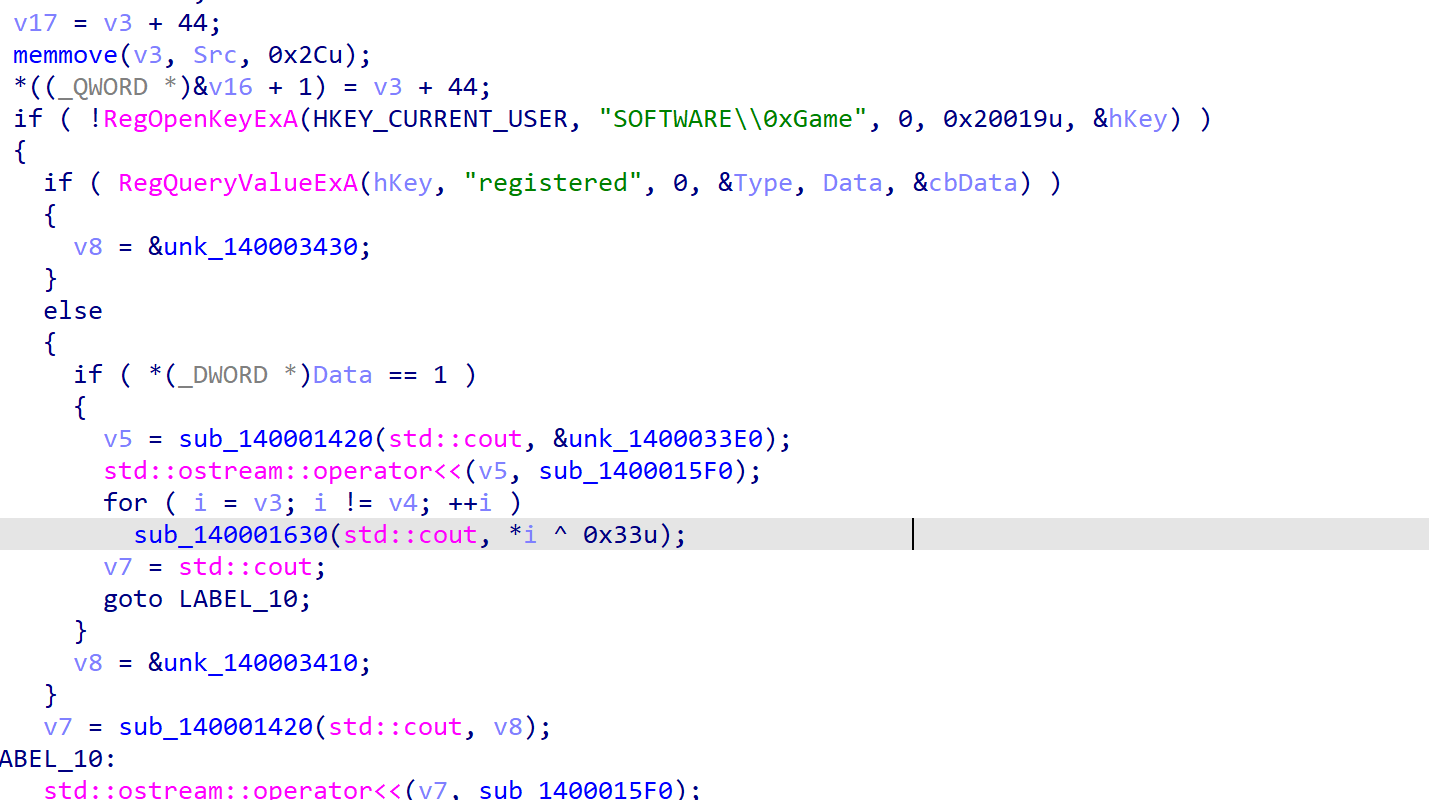
检查注册表,检查registered的值是否为1
值异或0x33
使用的上面的数据,注意这里是小端序
GPT帮写代码
import struct
src = [1383353091, 189290078, 38864395, 503515984, 1364350722,
1448105758, 89136641, 85852241, 72812293, 50464516, 1314325334]
# 将整数数组转换为字节
byte_array = b''
for val in src:
byte_array += struct.pack('<I', val) # 小端序
# 解密(异或0x33)
flag = ''
for byte in byte_array:
# print(byte)
print(chr(byte ^ 0x33),end='')
# 0xGame{885b1c80-1dab-dce2-c6b3-664d77410e0d}码海舵师
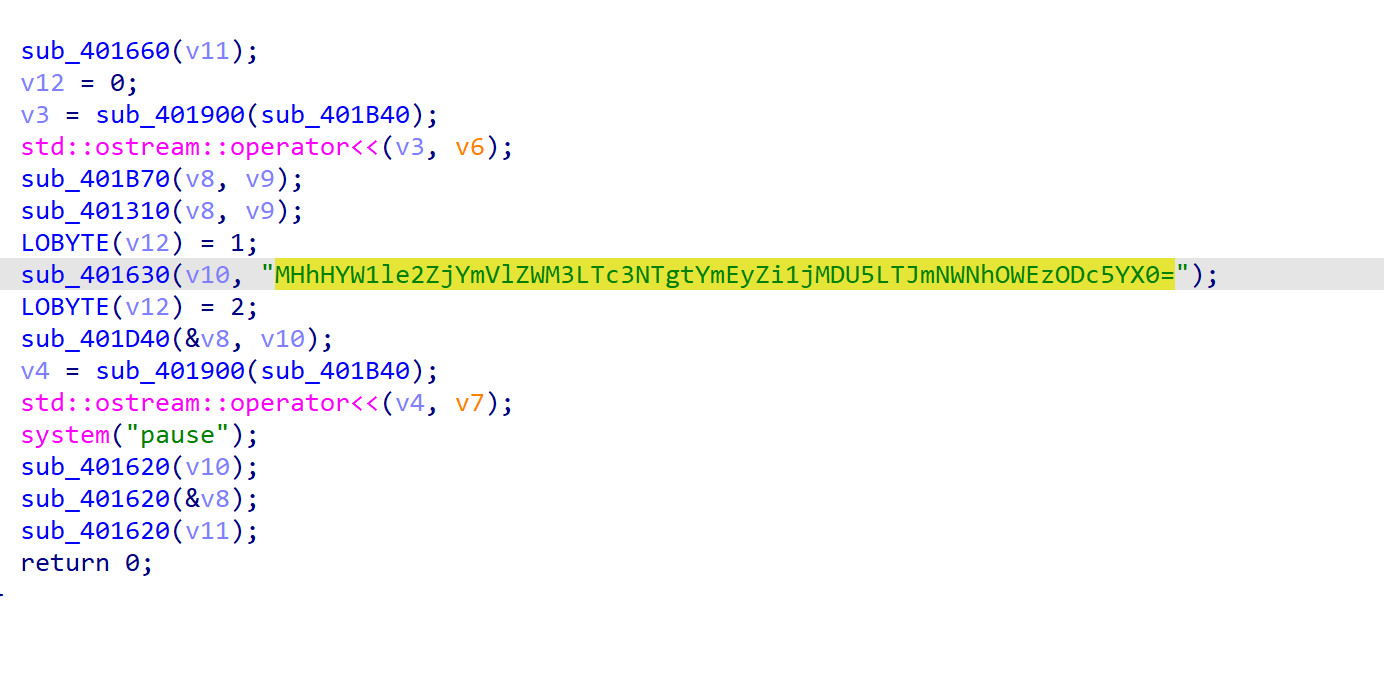
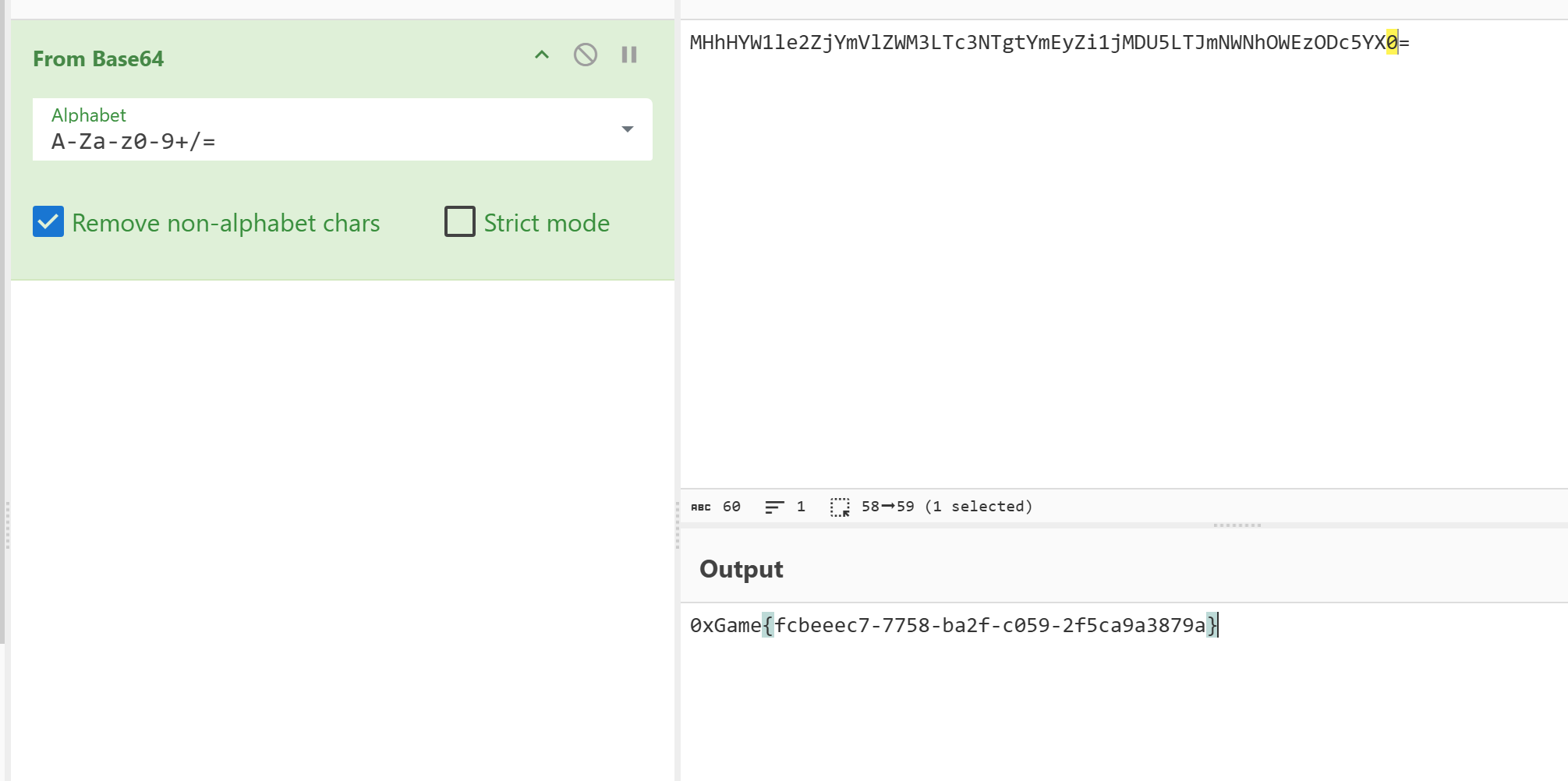
壳艺大师
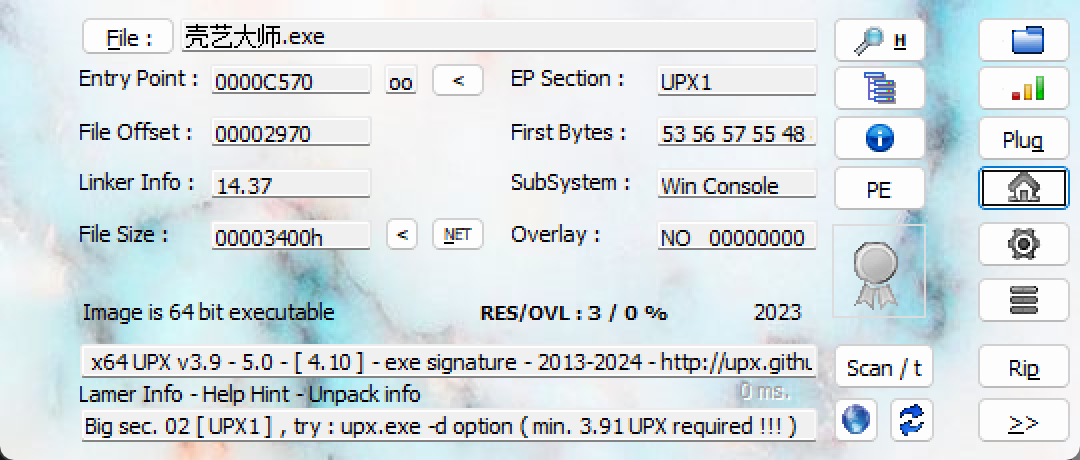
upx壳
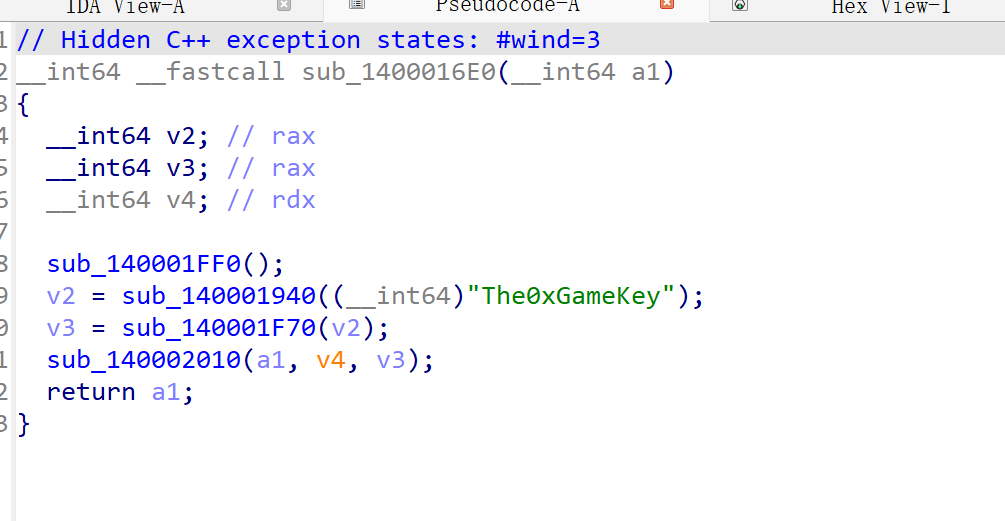
找到个key
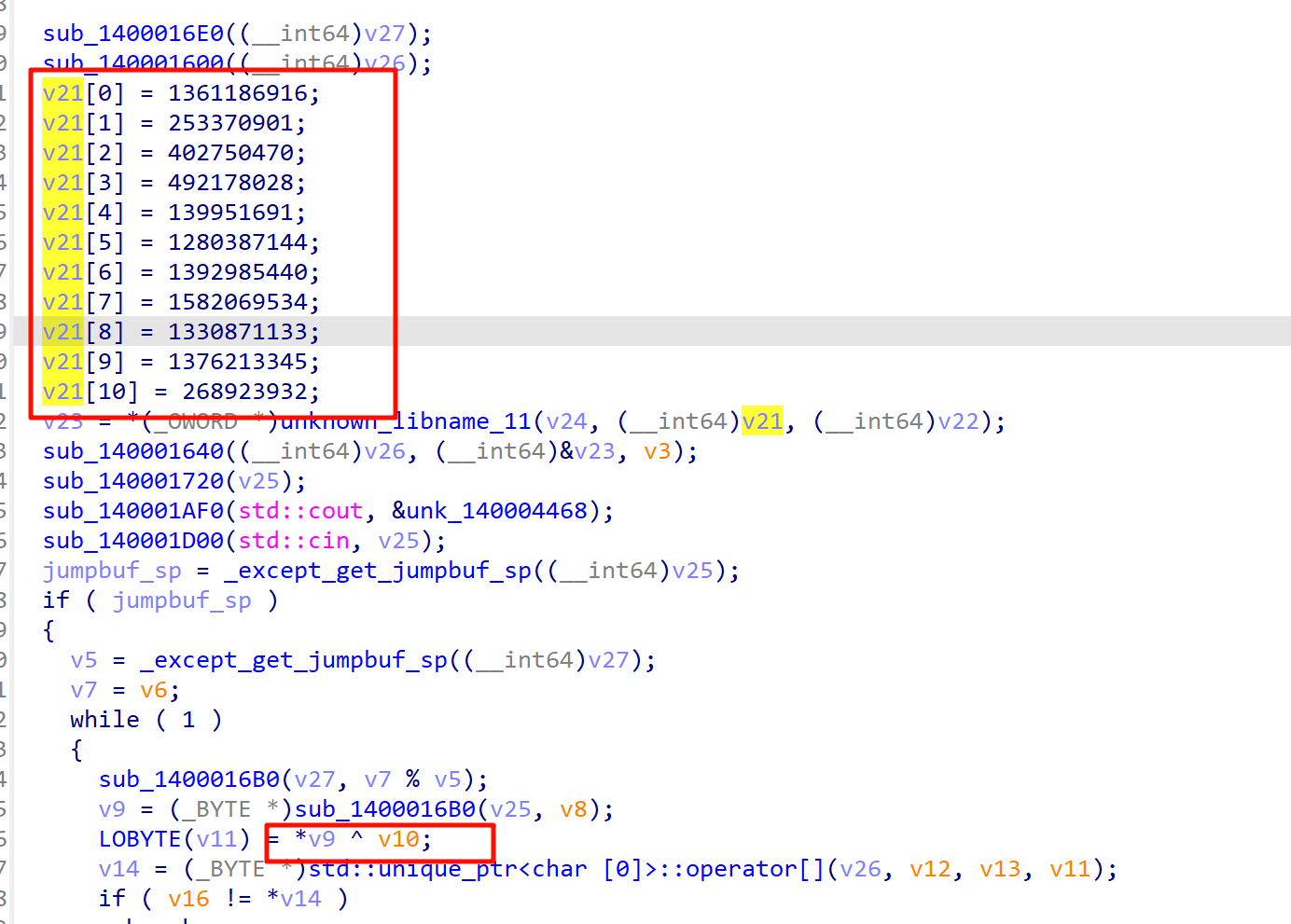
跟上面一样注意小端序提取出来
from pwn import *
v21 = [0]*11
v21[0] = 1361186916
v21[1] = 253370901
v21[2] = 402750470
v21[3] = 492178028
v21[4] = 139951691
v21[5] = 1280387144
v21[6] = 1392985440
v21[7] = 1582069534
v21[8] = 1330871133
v21[9] = 1376213345
v21[10] = 268923932
# # 将整数数组转换为字节
byte_array = b''
for val in v21:
byte_array += struct.pack('<I', val) # 小端序
flag=xor(byte_array,b'The0xGameKey')
print(flag)
# 0xGame{bc7da8b3-396e-c454-bcf0-3806651bbd3f}符文解密师
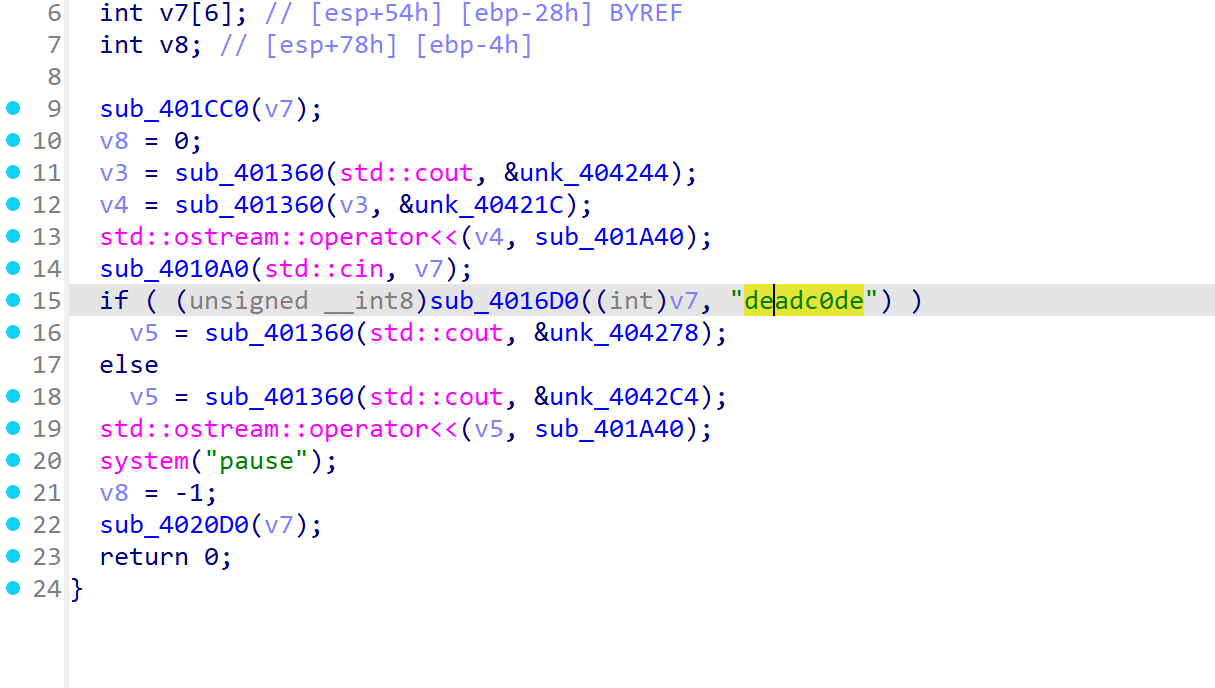
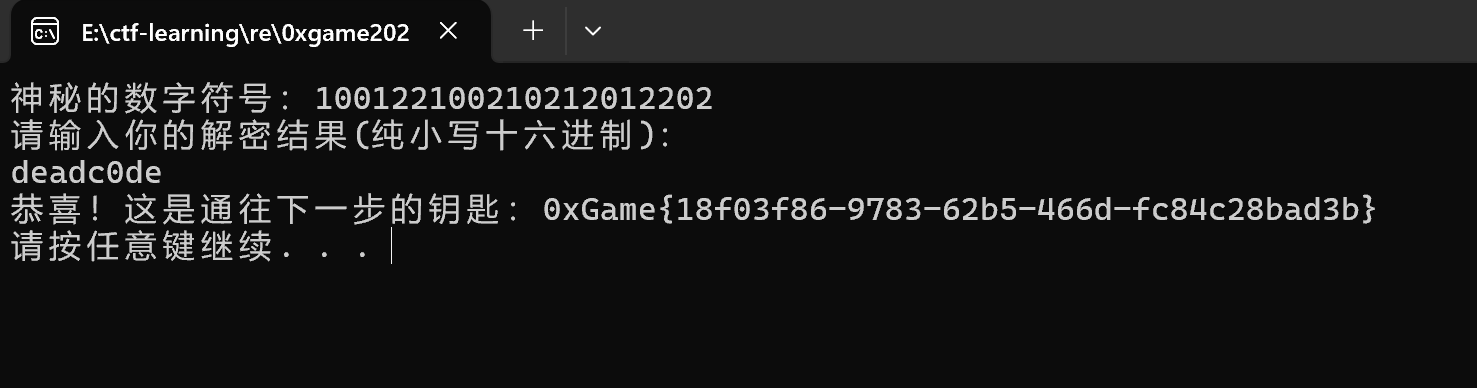
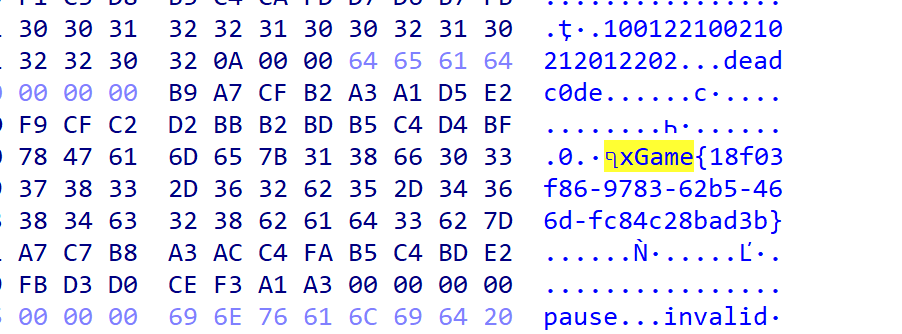
或者直接看hex
Week3
变量迷城
计算表达式,算出来就行
from z3 import *
# 步骤1:解方程
x = Int('x')
y = Int('y')
s = Solver()
# 添加方程
s.add(x*x + 2*y*y + 3*x + 4*y == 7384462351178)
s.add(5*x*x + 6*y*y + 7*x + 8*y == 22179606057658)
print("求解方程组...")
if s.check() == sat:
m = s.model()
x_val = m[x].as_long()
y_val = m[y].as_long()
print(f"找到解: x = {x_val}, y = {y_val}")
encrypted_flag = [1, 73, 115, 84, 92, 81, 75, 65, 116, 84, 90, 93, 7, 2, 87, 24,
83, 87, 84, 64, 106, 4, 9, 86, 84, 28, 4, 5, 9, 82, 29, 74,
119, 85, 93, 1, 3, 84, 0, 0, 1, 0, 3, 5]
brand = "0xGame"
key = str(x_val) + brand
print(f"\n解密密钥: {key}")
print(f"密钥长度: {len(key)}")
# 解密
flag = ""
for i in range(len(encrypted_flag)):
decrypted_char = encrypted_flag[i] ^ ord(key[i % len(key)])
flag += chr(decrypted_char)
print(f"\nFlag: {flag}")
else:
print("方程组无解")代码启示录
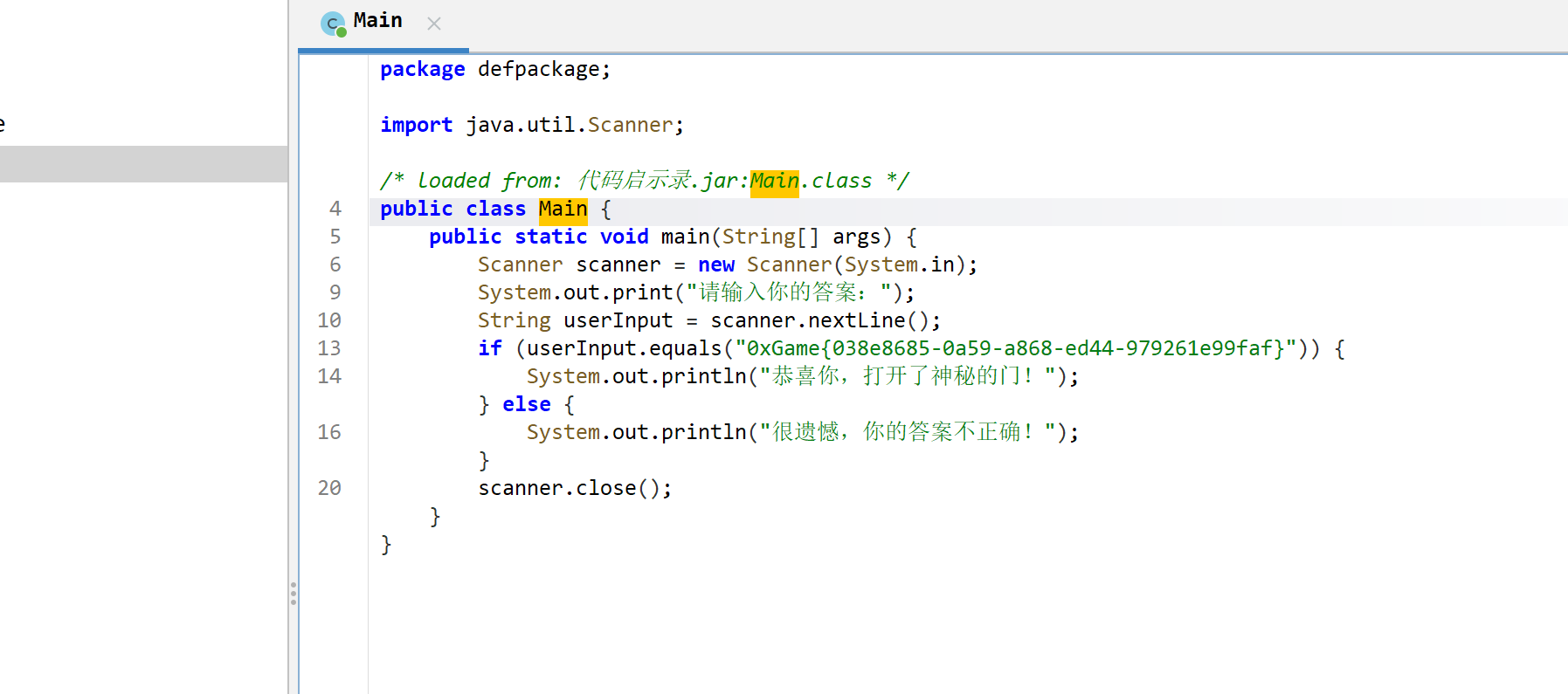
数字幽灵城
主要考察对android的了解
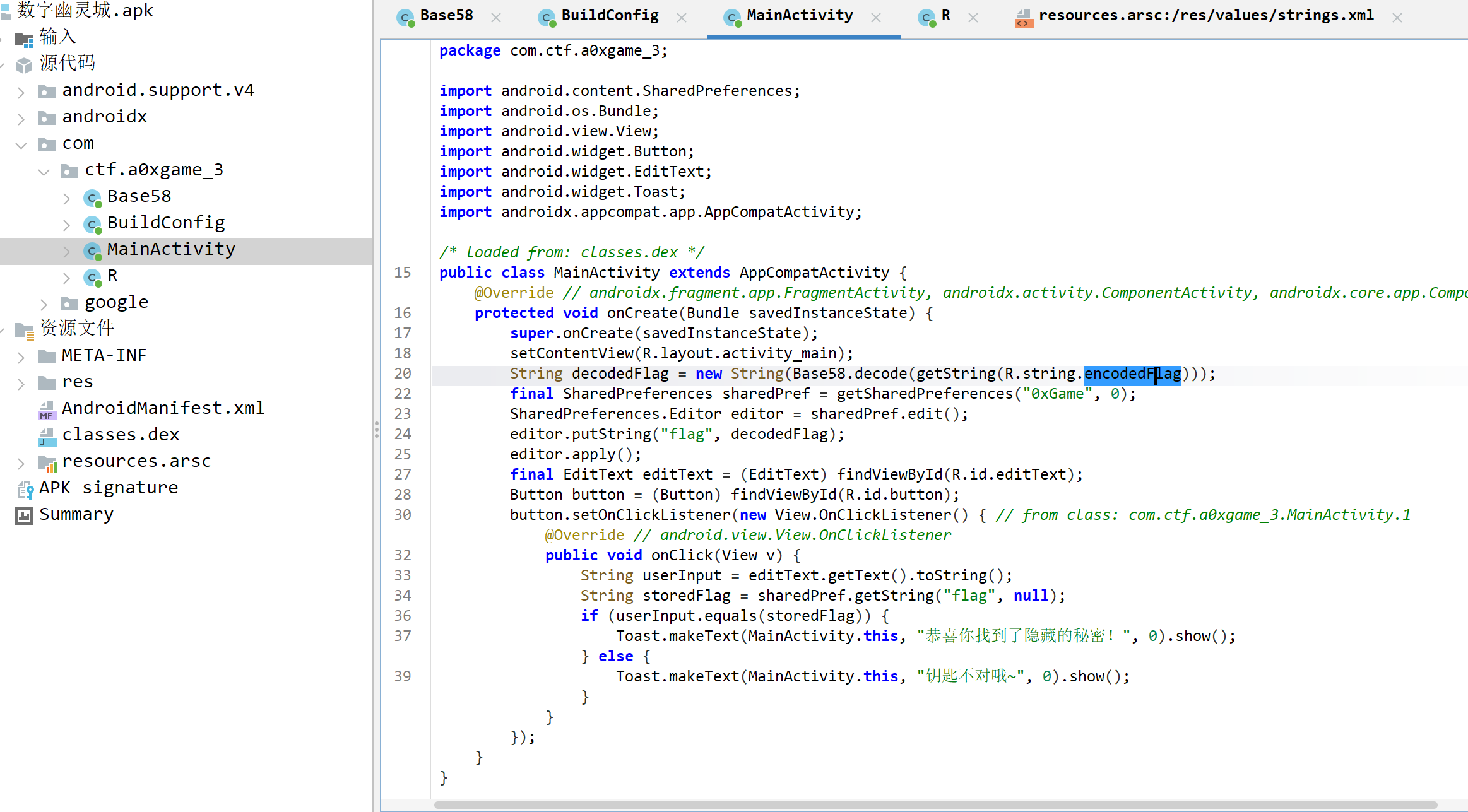
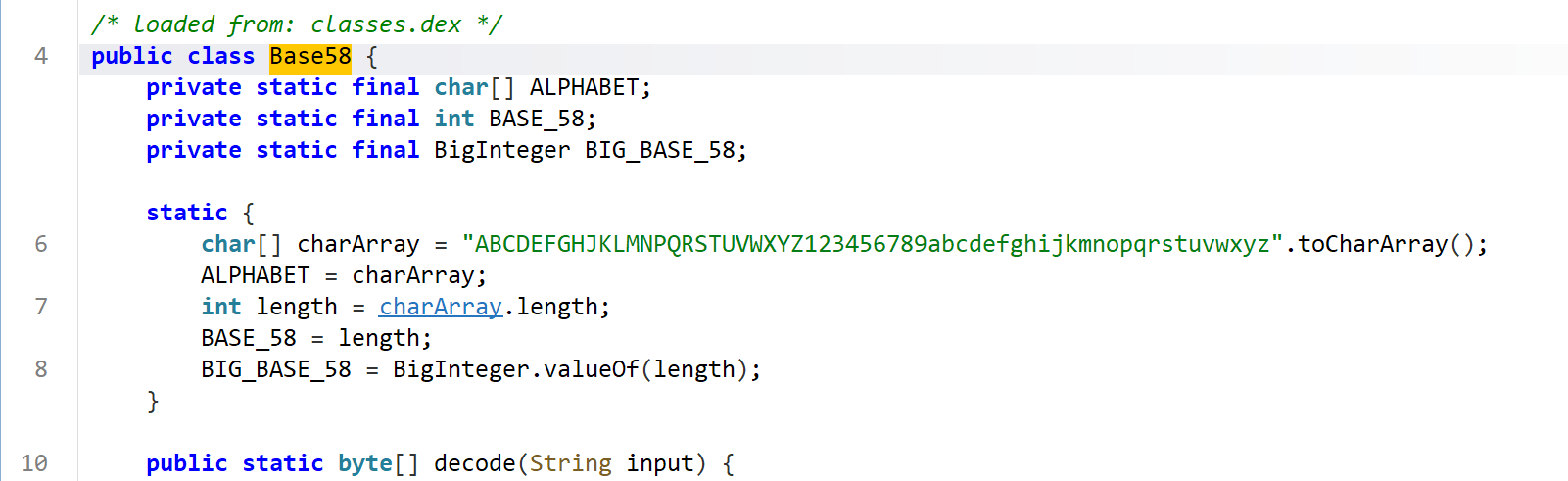
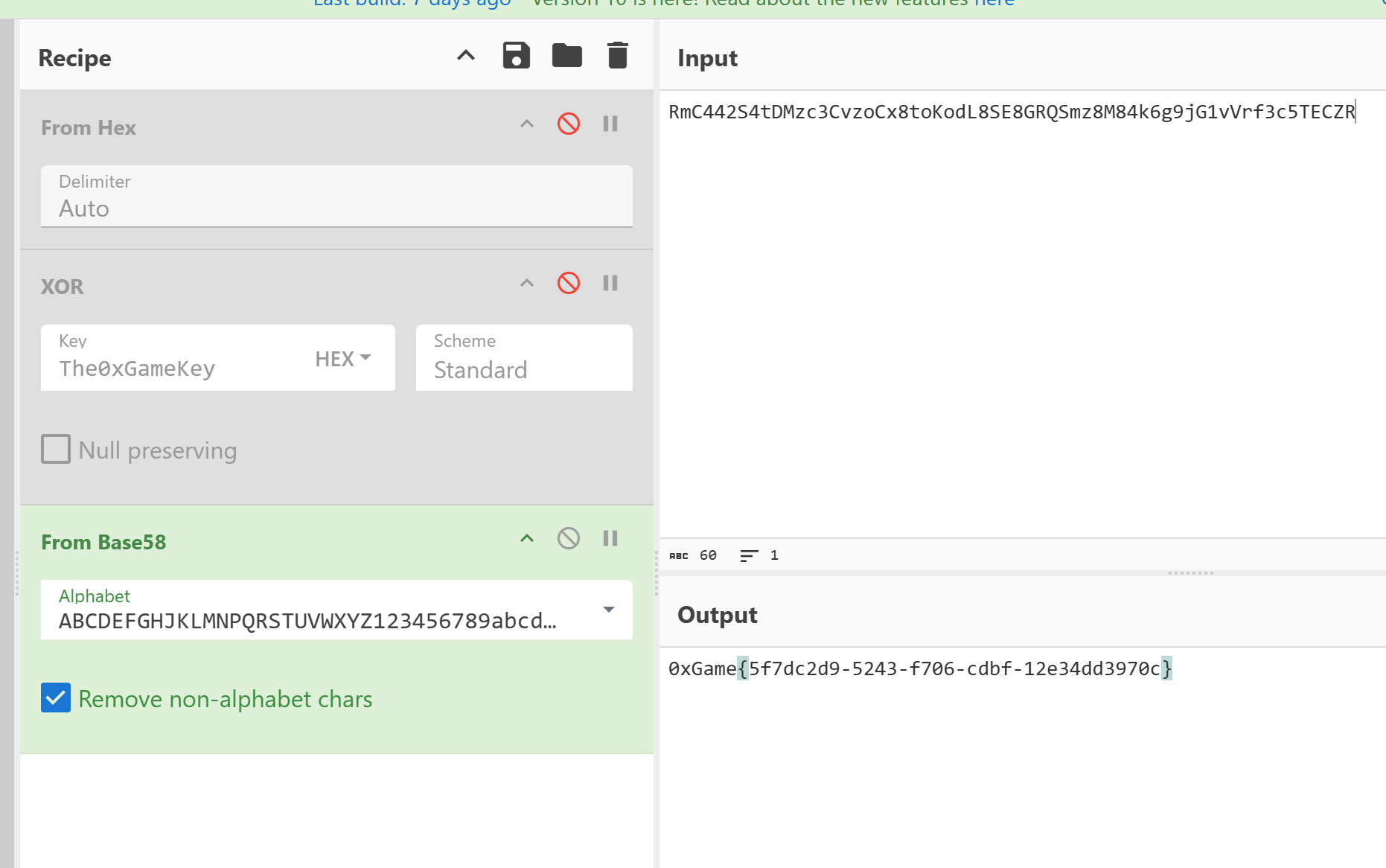
找到encodedFlag的值,然后换表base58
旋转密码城
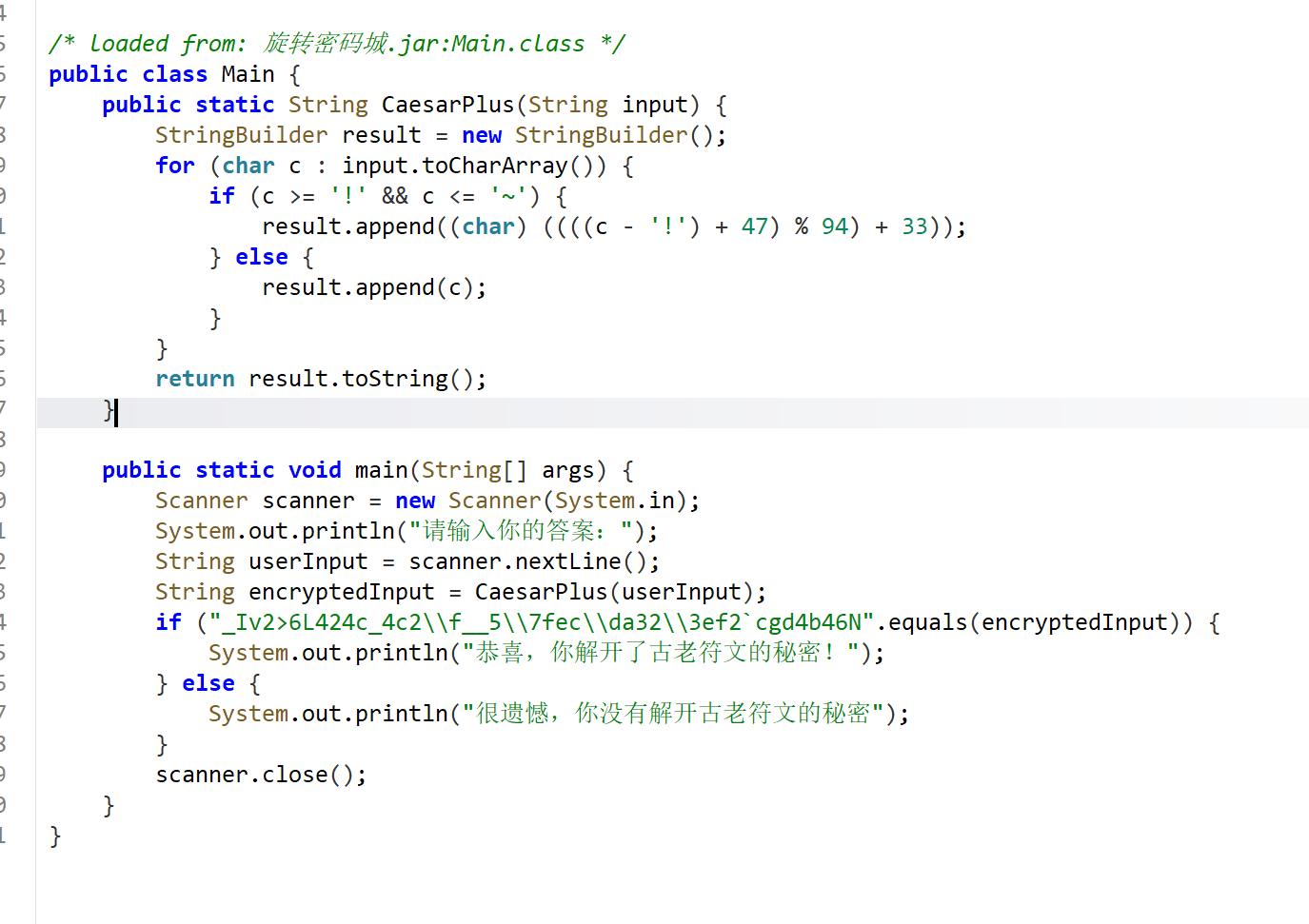
要识别出算法,是类似与凯撒密码,可以看出偏移量为47,rot47
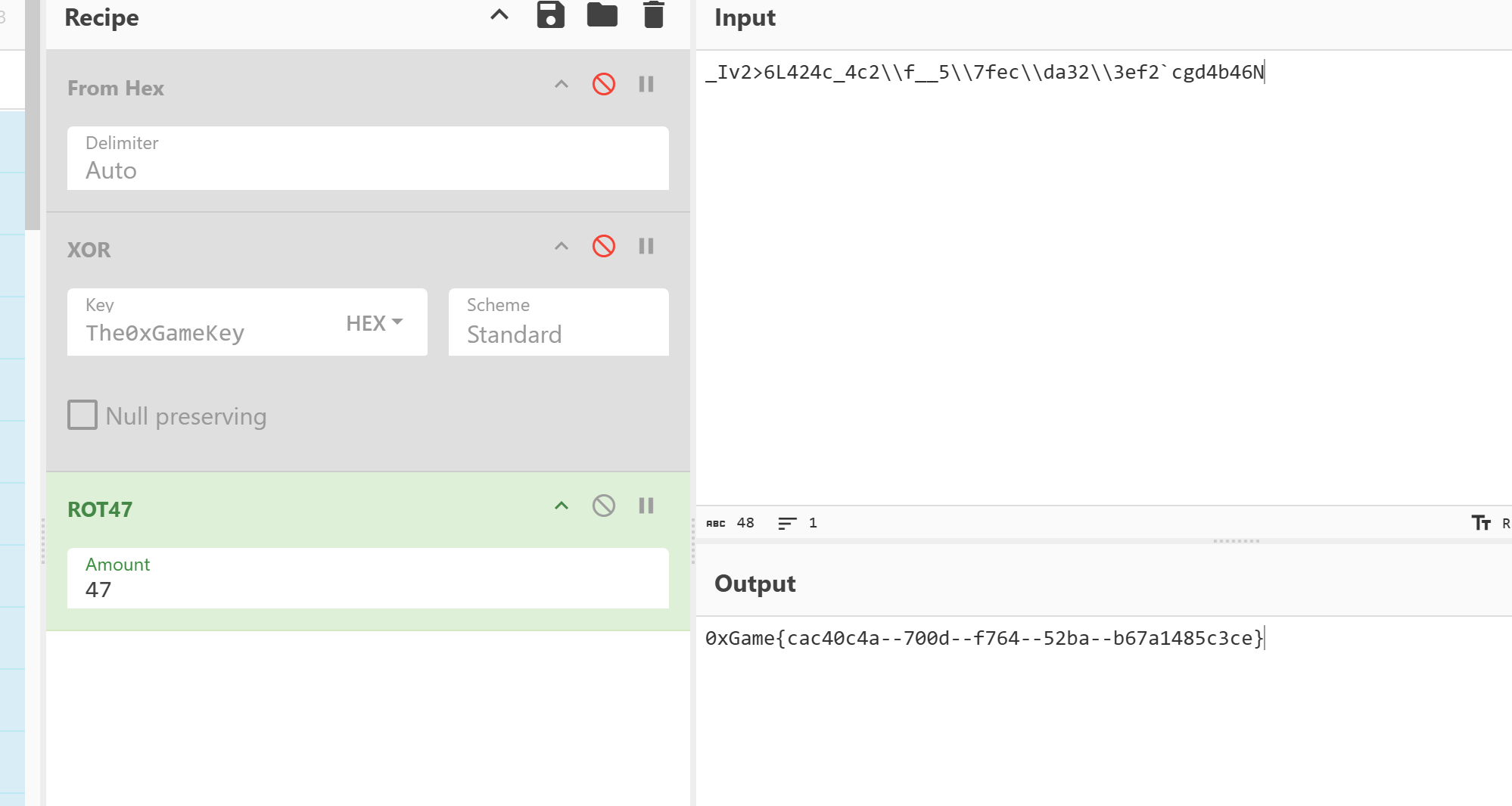
虚拟核心
根据代码得到解密的dex
package org.example;
import java.io.*;
public class Test {
public static void main(String[] args) {
try {
// 定义文件和密钥
File encryptedFile = new File("encrypted.dex");
File decryptedFile = new File("decrypted.dex");
byte[] key = "The0xGameKey".getBytes();
// 执行解密
decrypt(encryptedFile, decryptedFile, key);
System.out.println("解密完成!输出文件:decrypted.dex");
} catch (IOException e) {
e.printStackTrace();
}
}
public static void decrypt(File encryptedFile, File decryptedFile, byte[] key) throws IOException {
FileInputStream fis = new FileInputStream(encryptedFile);
FileOutputStream fos = new FileOutputStream(decryptedFile);
byte[] buffer = new byte[key.length * 64];
while (true) {
int bytesRead = fis.read(buffer);
if (bytesRead != -1) {
for (int i = 0; i < bytesRead; i++) {
buffer[i] = (byte) (buffer[i] ^ key[i % key.length]);
}
fos.write(buffer, 0, bytesRead);
} else {
fis.close();
fos.close();
return;
}
}
}
}查看逻辑
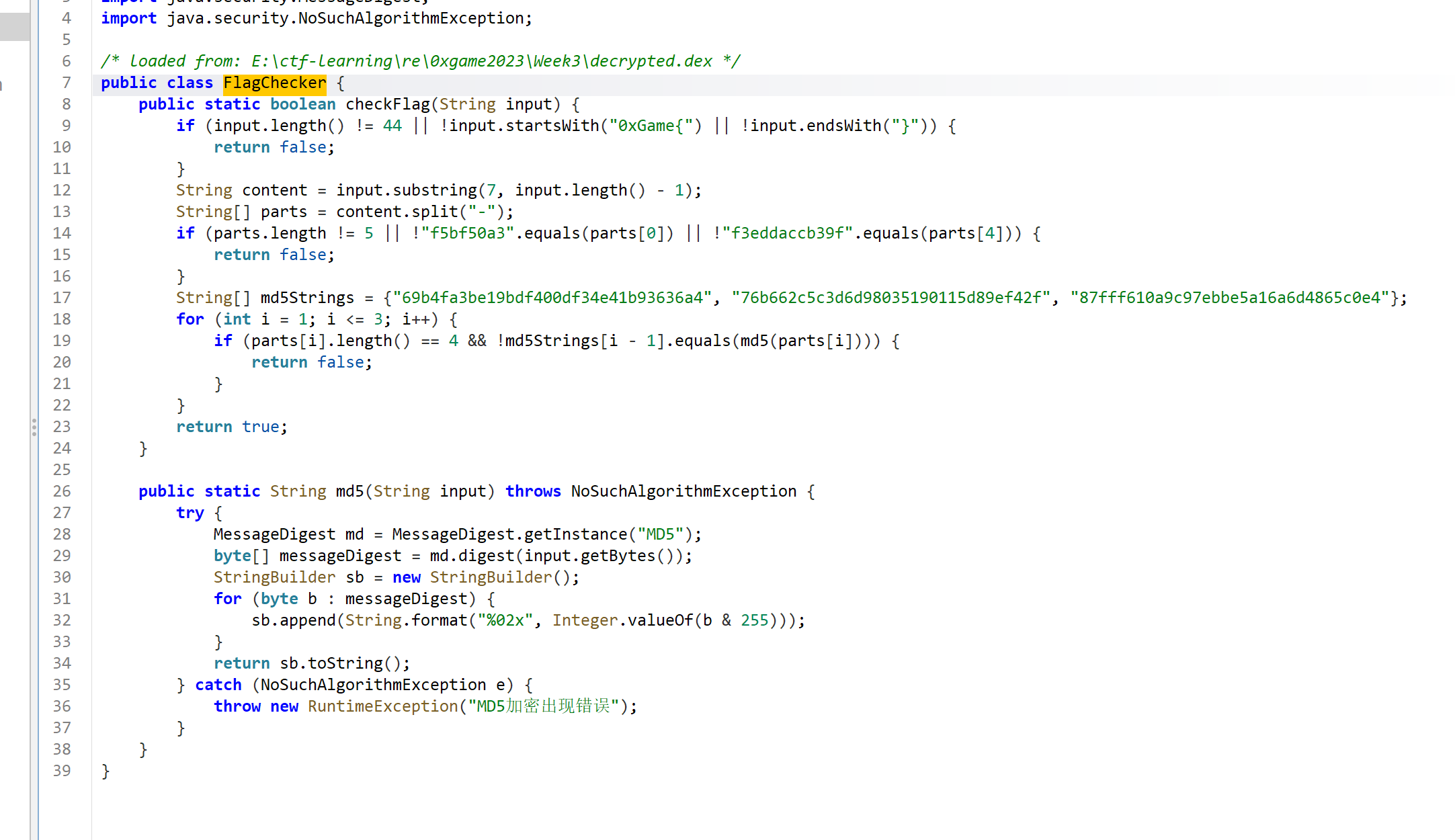
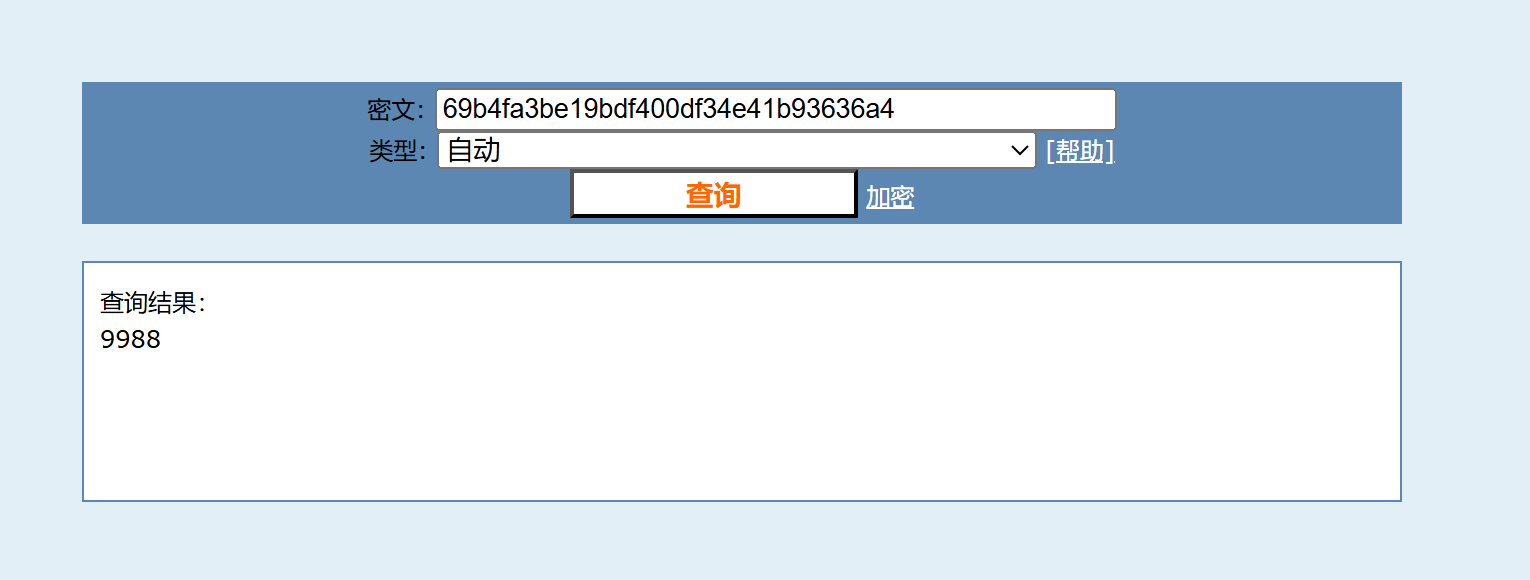
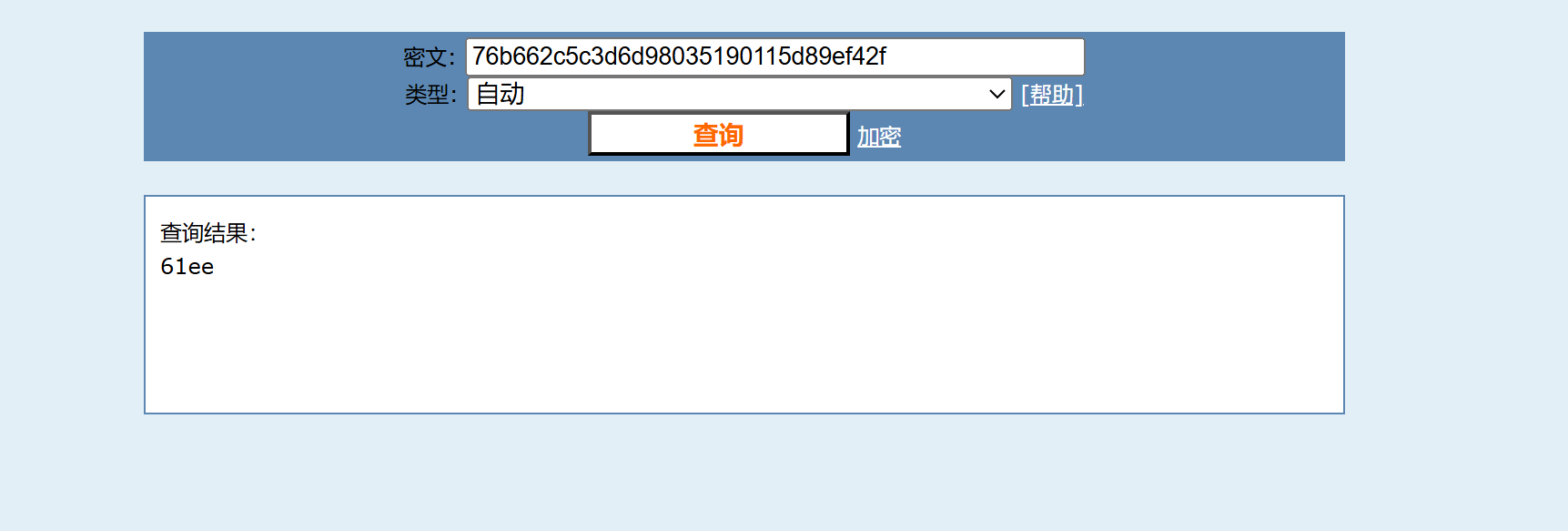
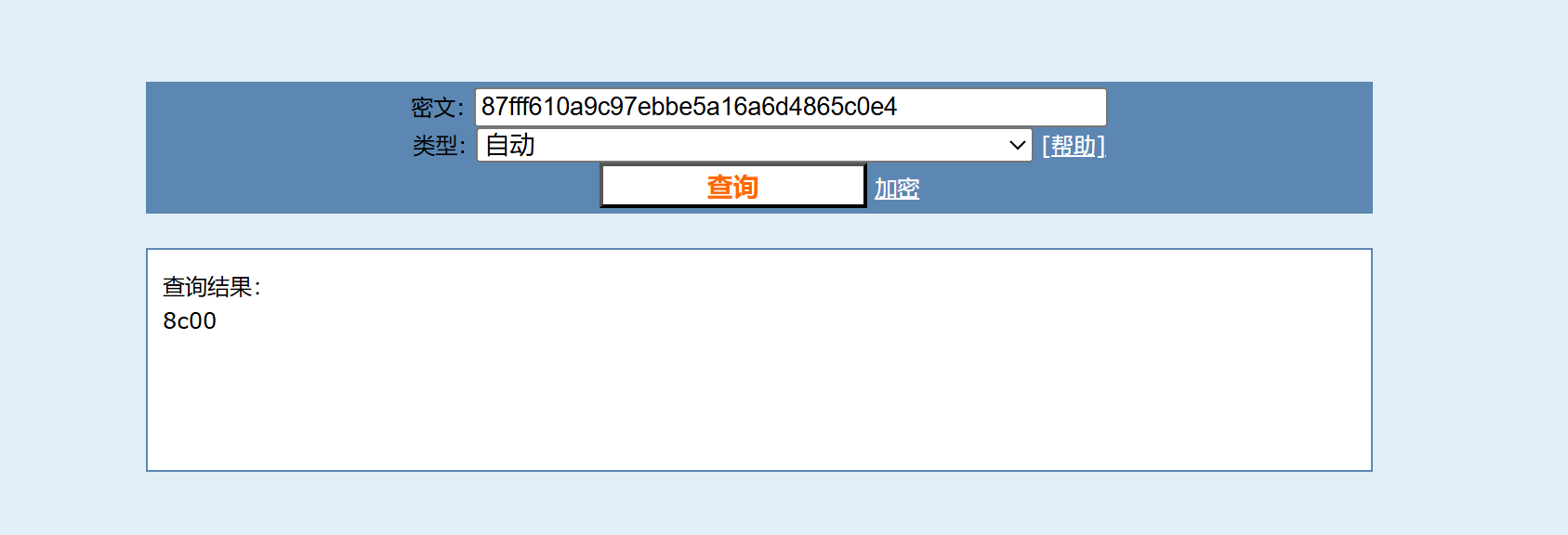
然后拼接即可
Week4
二进制学徒
指令神使
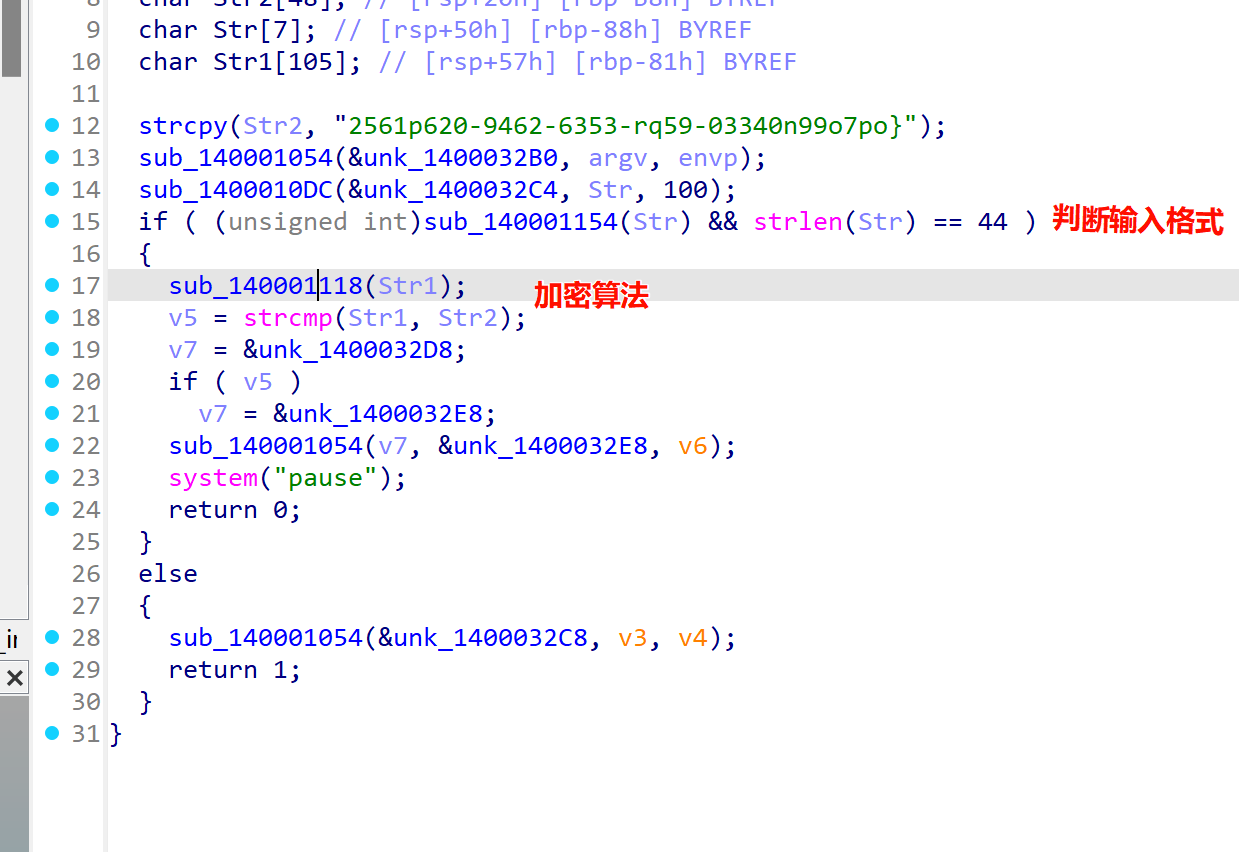
交给gpt判断出rot13
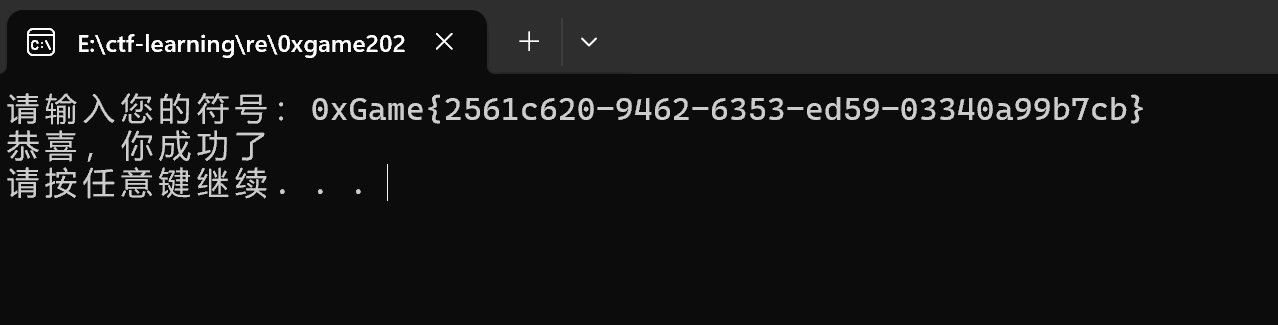
代码悟道者
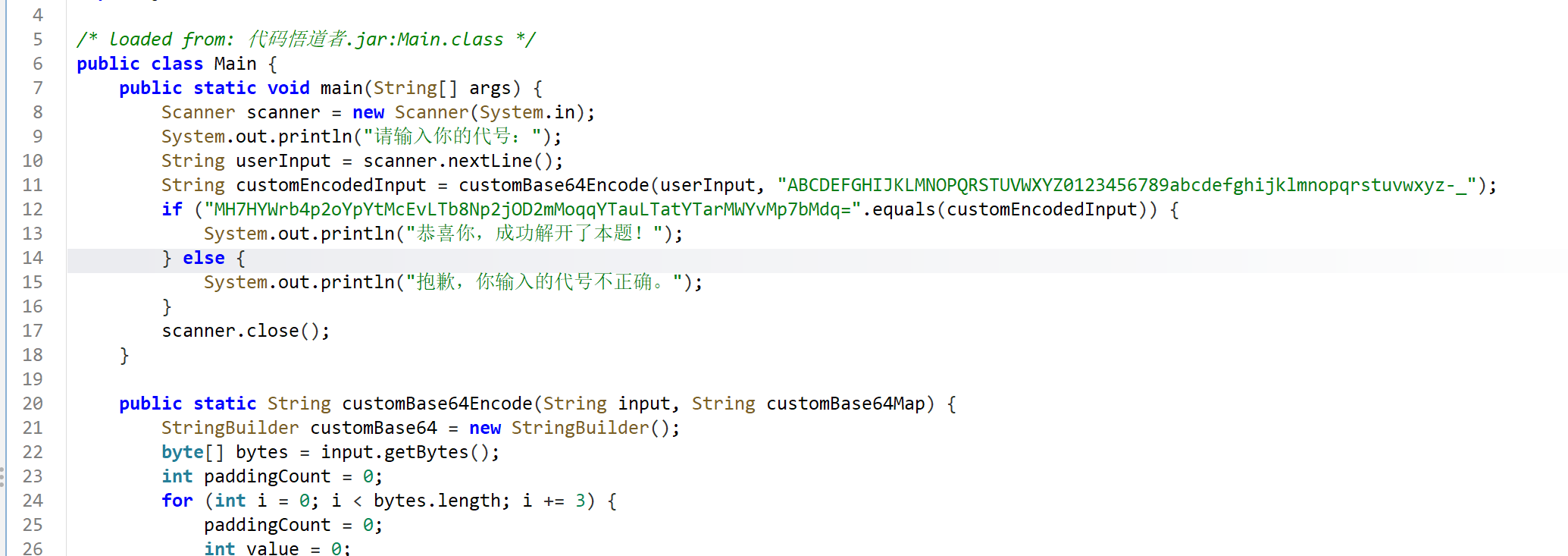
把-_换为+/即可
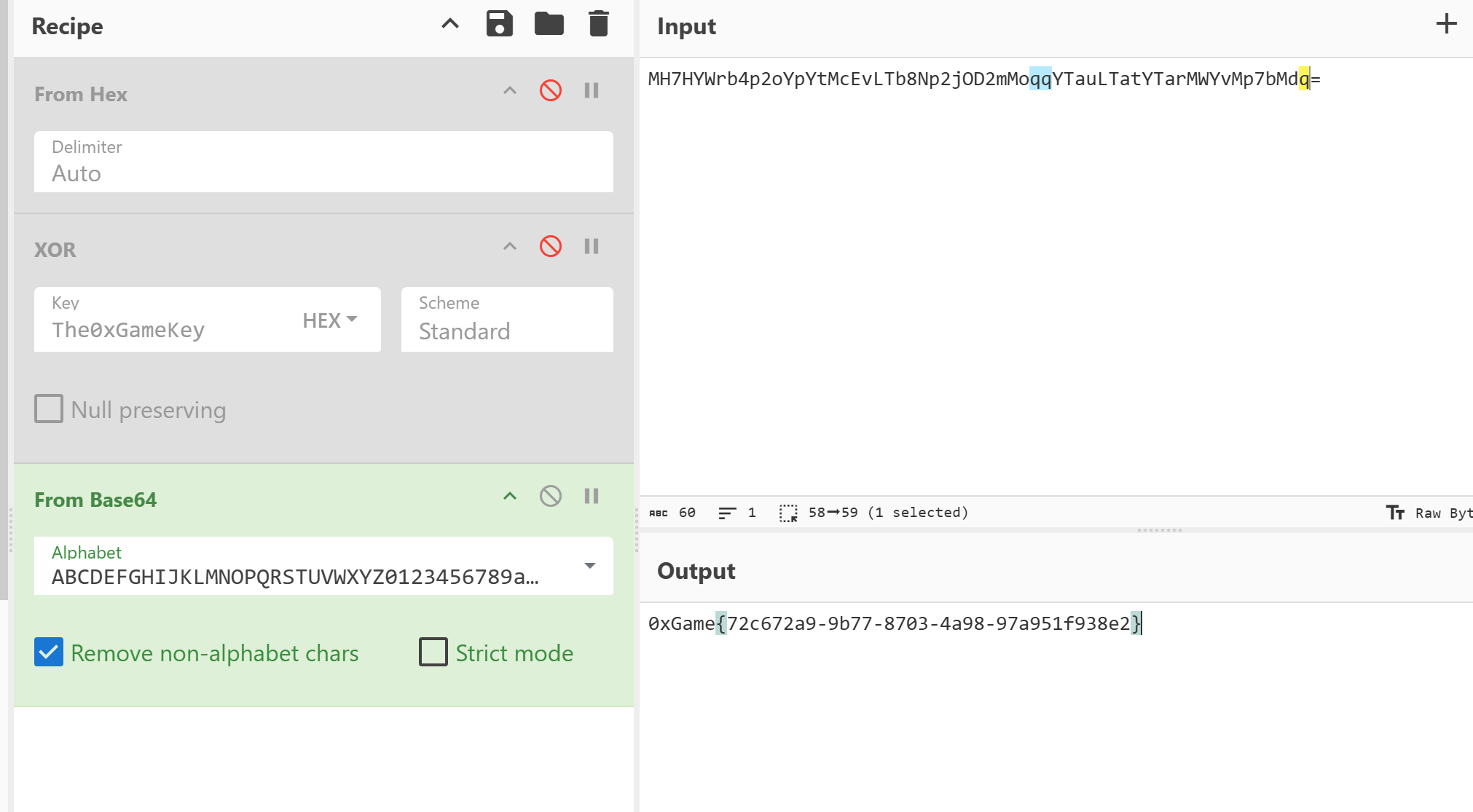
算法祭司
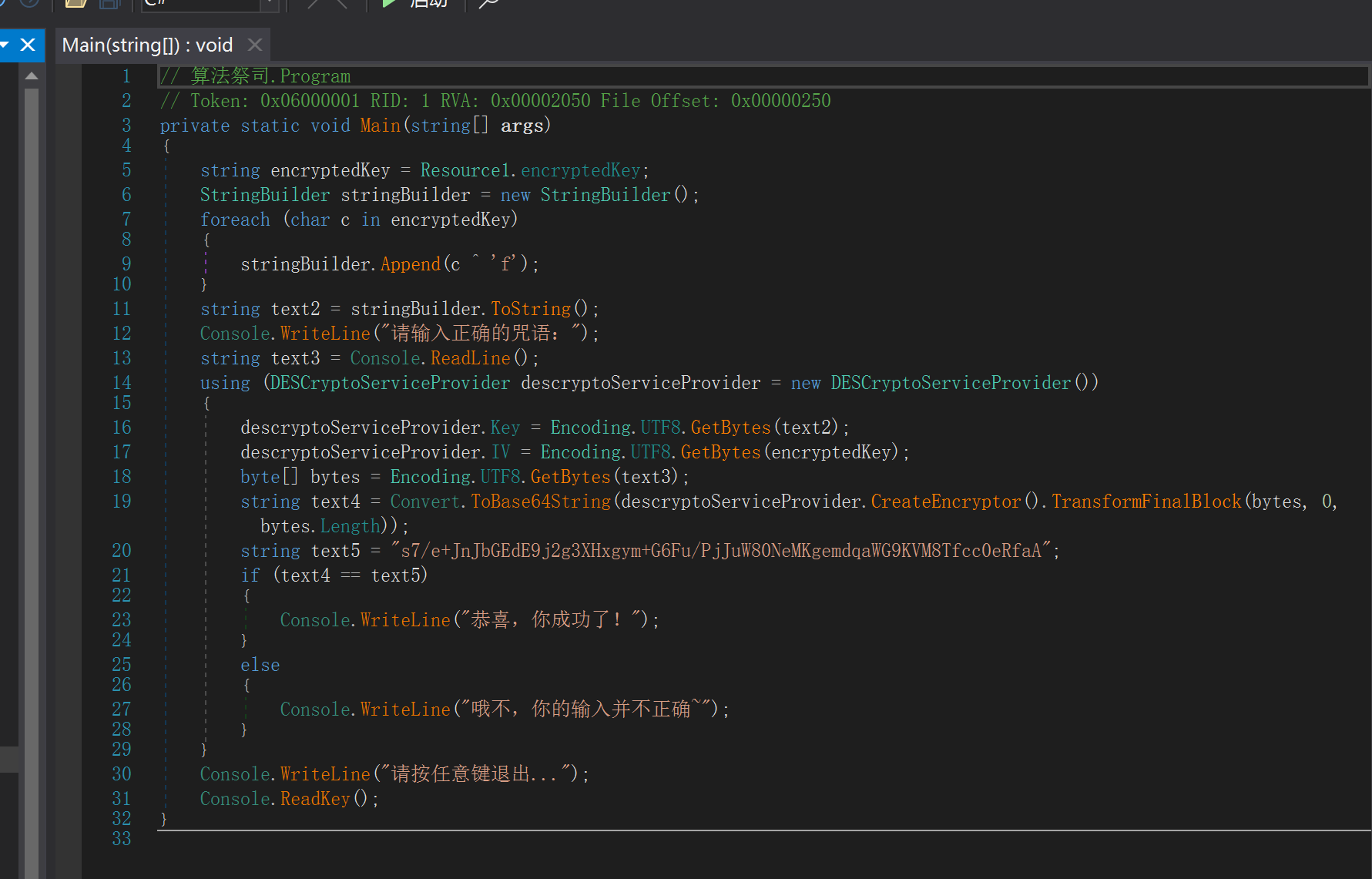
des解密,找到他的key和iv即可
找到encryptedKey
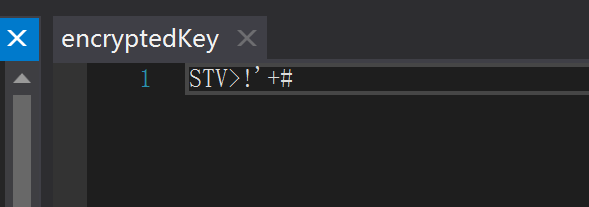
import base64
from Crypto.Cipher import DES
from Crypto.Util.Padding import unpad
def decrypt_des():
# 已知数据
encryptedKey = "STV>!'+#"
target_base64 = "s7/e+JnJbGEdE9j2g3XHxgym+G6Fu/PjJuW80NeMKgemdqaWG9KVM8Tfcc0eRfaA"
# 步骤1:计算密钥
key = ""
for c in encryptedKey:
key += chr(ord(c) ^ ord('f'))
print(f"加密密钥 (encryptedKey): {encryptedKey}")
print(f"解密密钥 (key): {key}")
# 步骤2:准备DES参数
key_bytes = key.encode('utf-8')
iv_bytes = encryptedKey.encode('utf-8')
ciphertext = base64.b64decode(target_base64)
print(f"\nDES参数:")
print(f"Key: {key_bytes.hex()}")
print(f"IV: {iv_bytes.hex()}")
print(f"密文长度: {len(ciphertext)} bytes")
# 步骤3:DES解密
cipher = DES.new(key_bytes, DES.MODE_CBC, iv_bytes)
plaintext = cipher.decrypt(ciphertext)
# 步骤4:去除PKCS7填充
try:
plaintext = unpad(plaintext, DES.block_size)
except:
# 手动去除填充
padding_length = plaintext[-1]
if padding_length <= 8:
plaintext = plaintext[:-padding_length]
flag = plaintext.decode('utf-8')
print(f"\nFlag: {flag}")
return flag
# 运行解密
decrypt_des()
# 0xGame{8edf2e65-1cb3-2e1a-b2d1-b54d3d4bddc5}内存星旅者
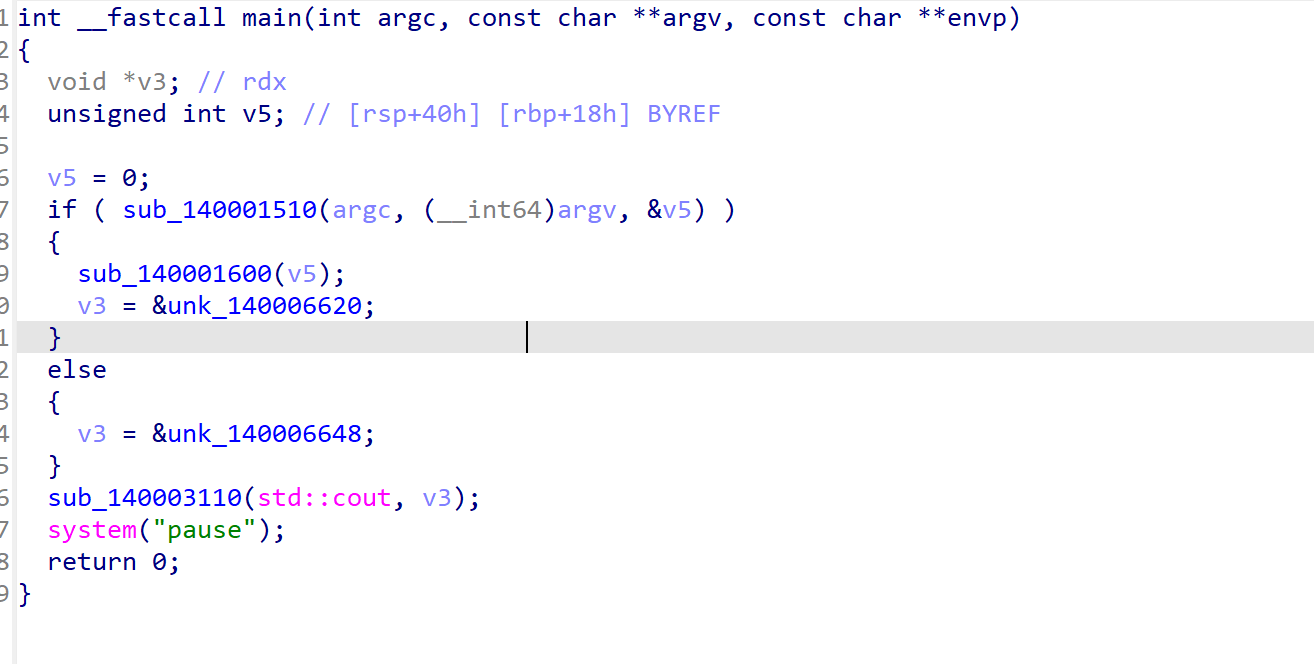
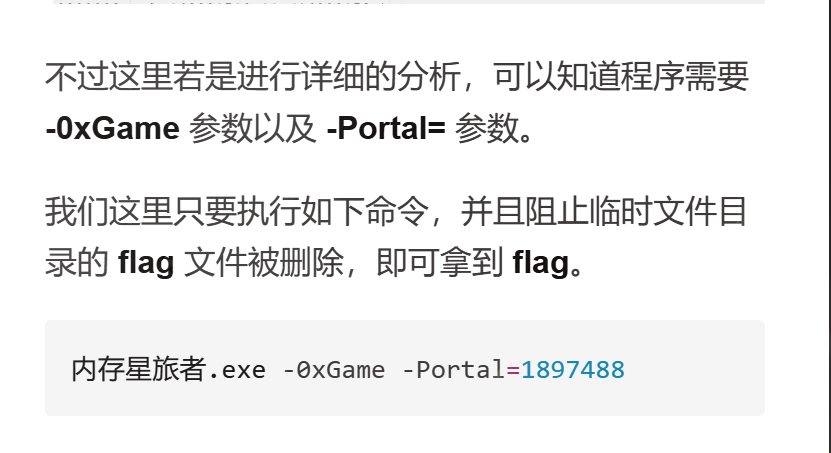
问ai
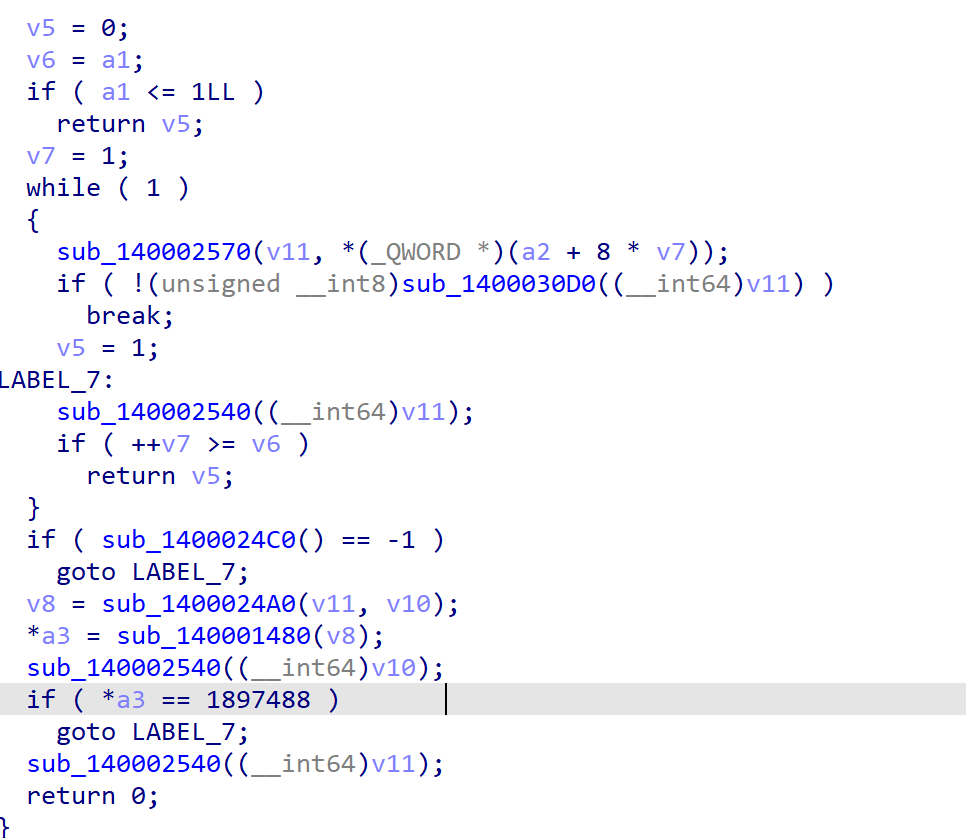
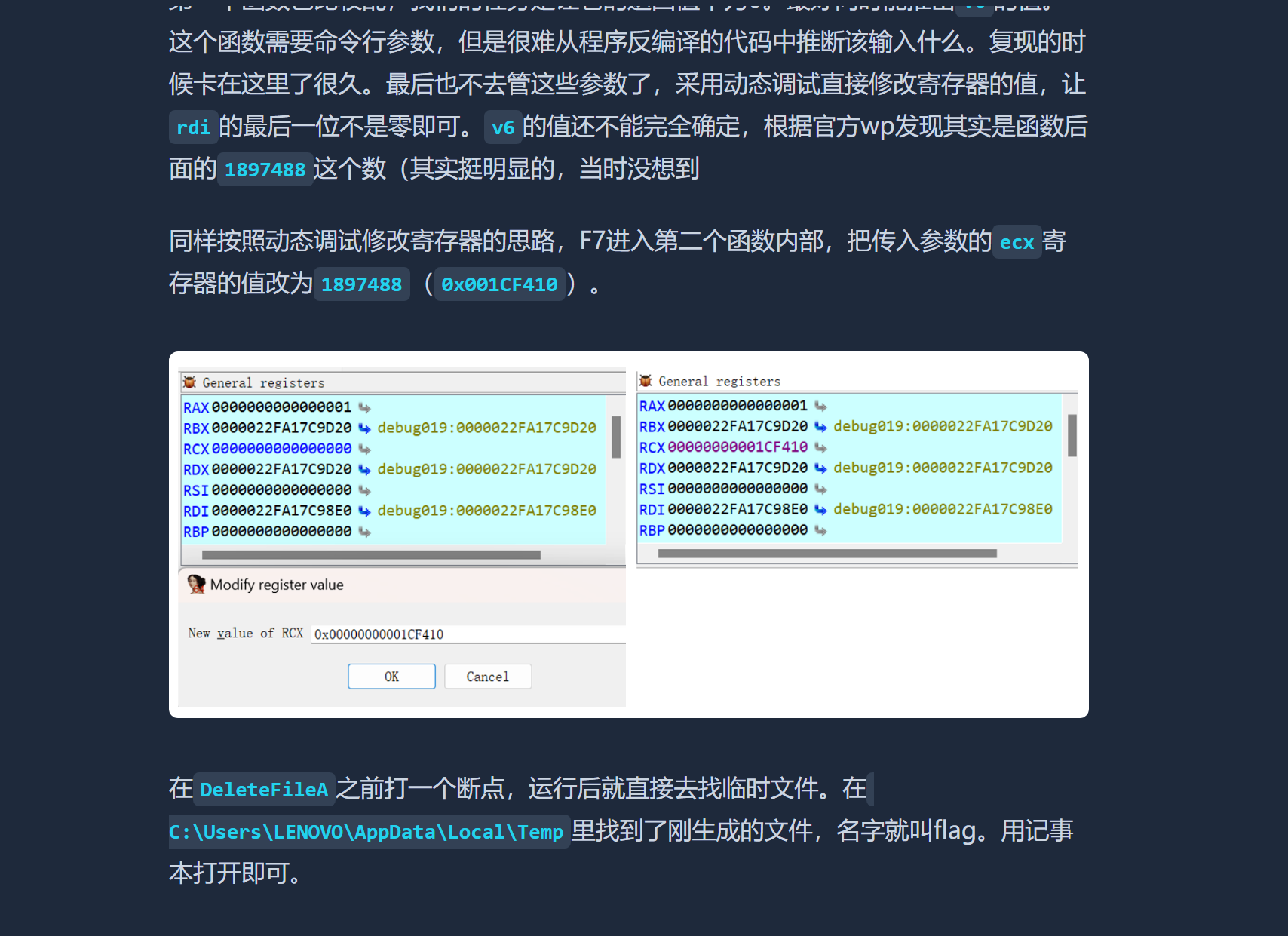
if中的函数是获取命令行参数,注意到这个1897488
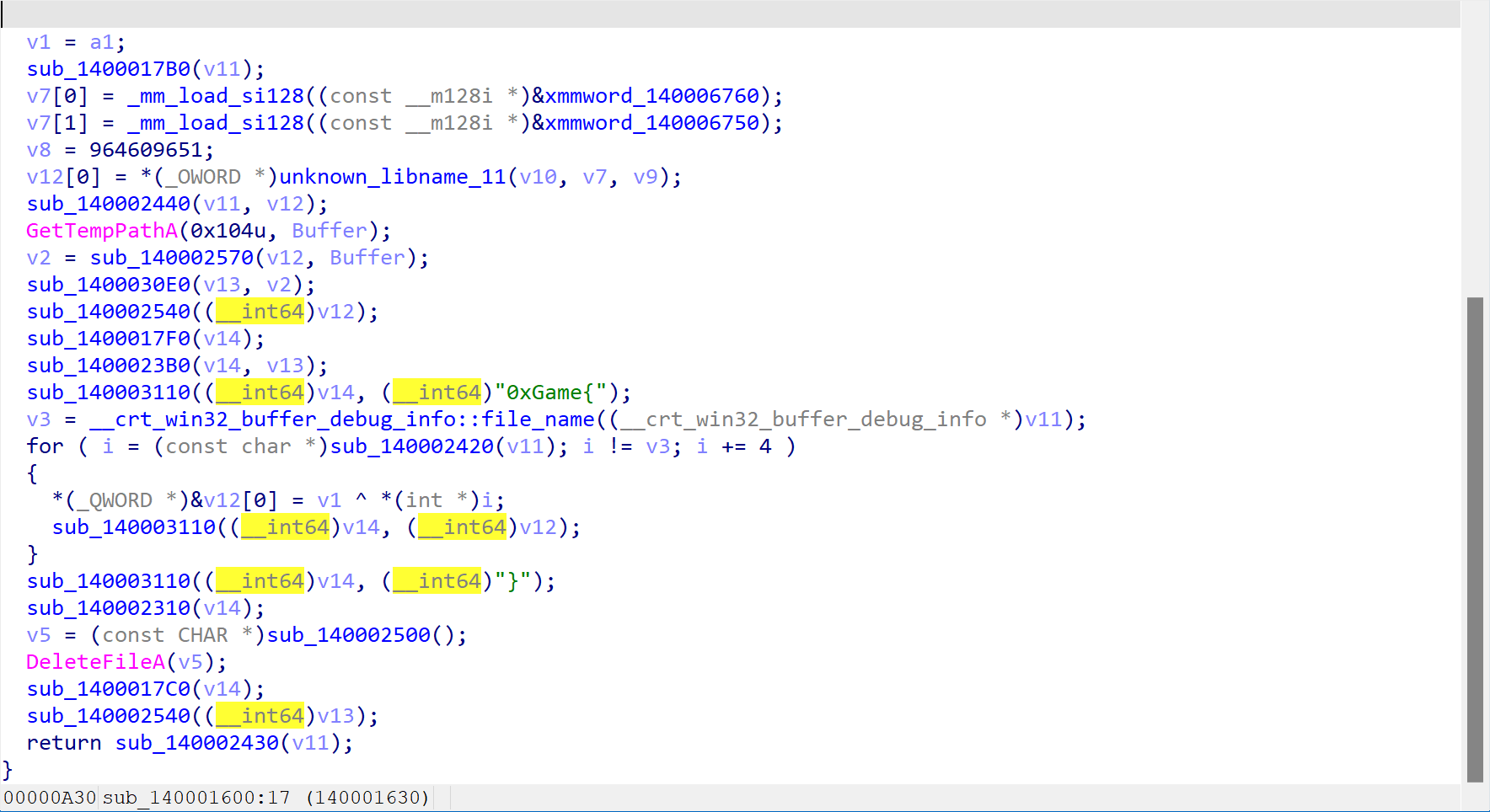
获取临时文件路径,生成flag,删除文件
经过分析,传入的参数就是要拿去异或的v1,应该为1897488
0xGame2023 Re 刷题
https://zer0peach.github.io/2025/08/11/0xGame2023-Re-刷题/