Litctf2023 Re 刷题
Litctf2023 Re 刷题
世界上最棒的程序员
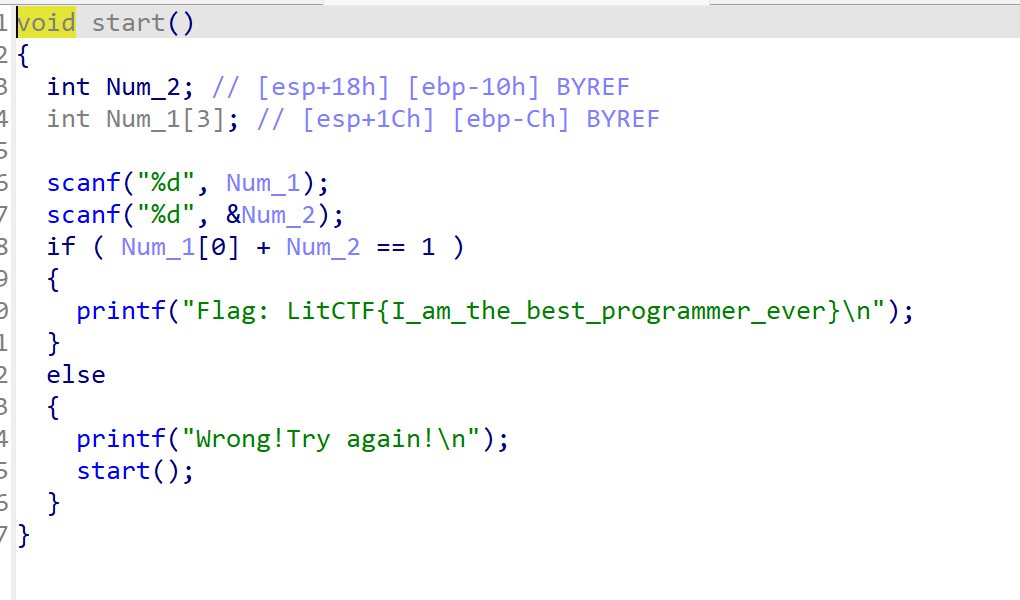
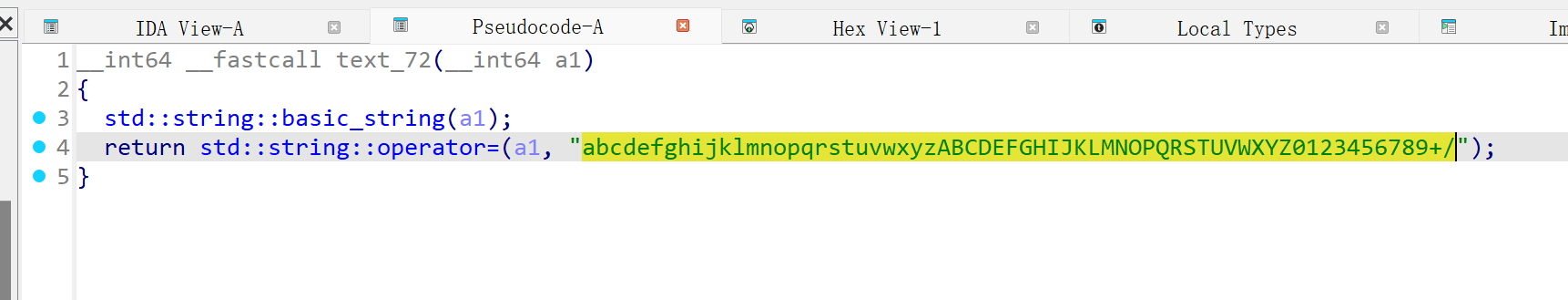
Babyx0r
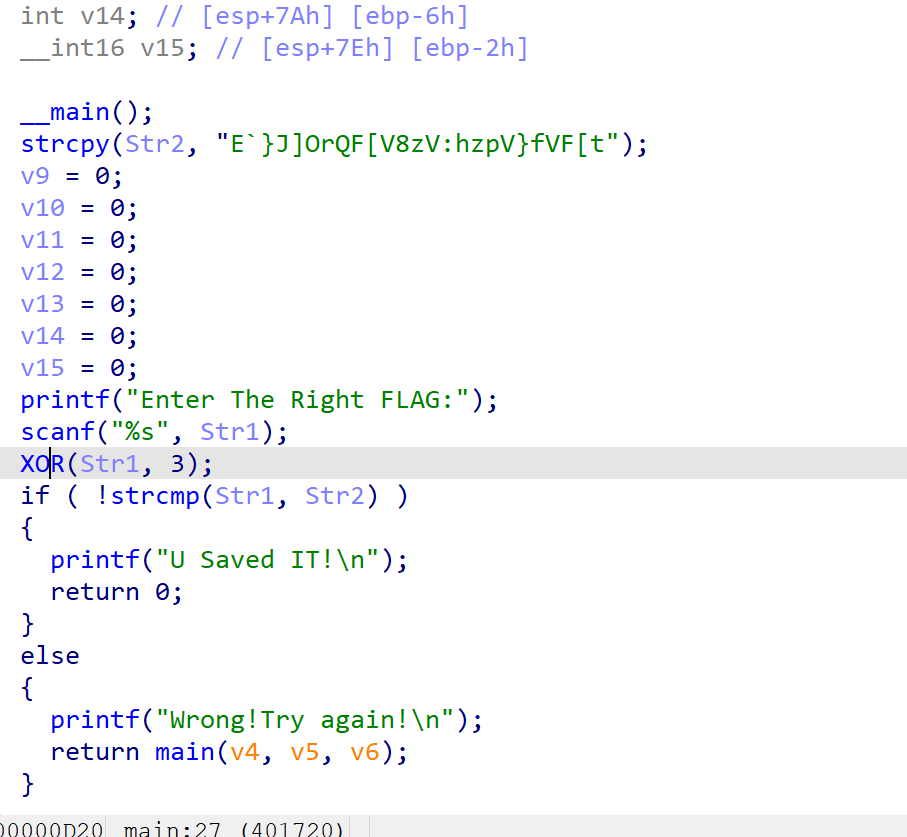
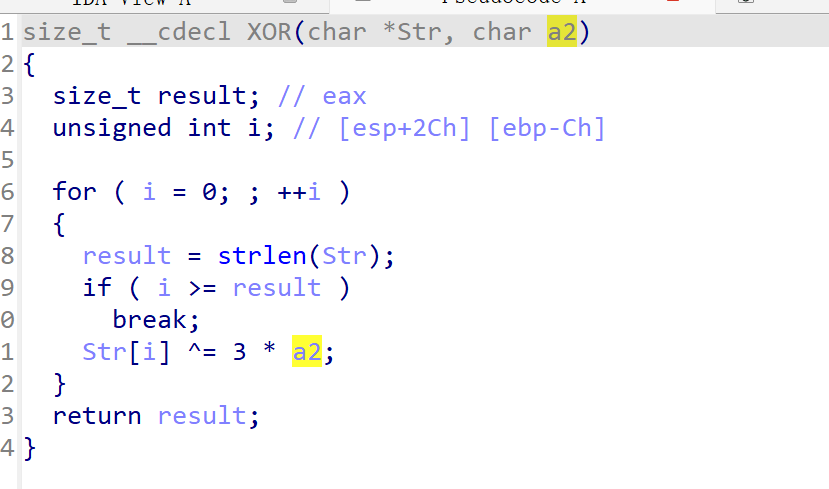
要异或3x3
s = 'E`}J]OrQF[V8zV:hzpV}fVF[t'
for i in s:
print(chr(ord(i)^9),end='')
# LitCTF{XOR_1s_3asy_to_OR}enbase64
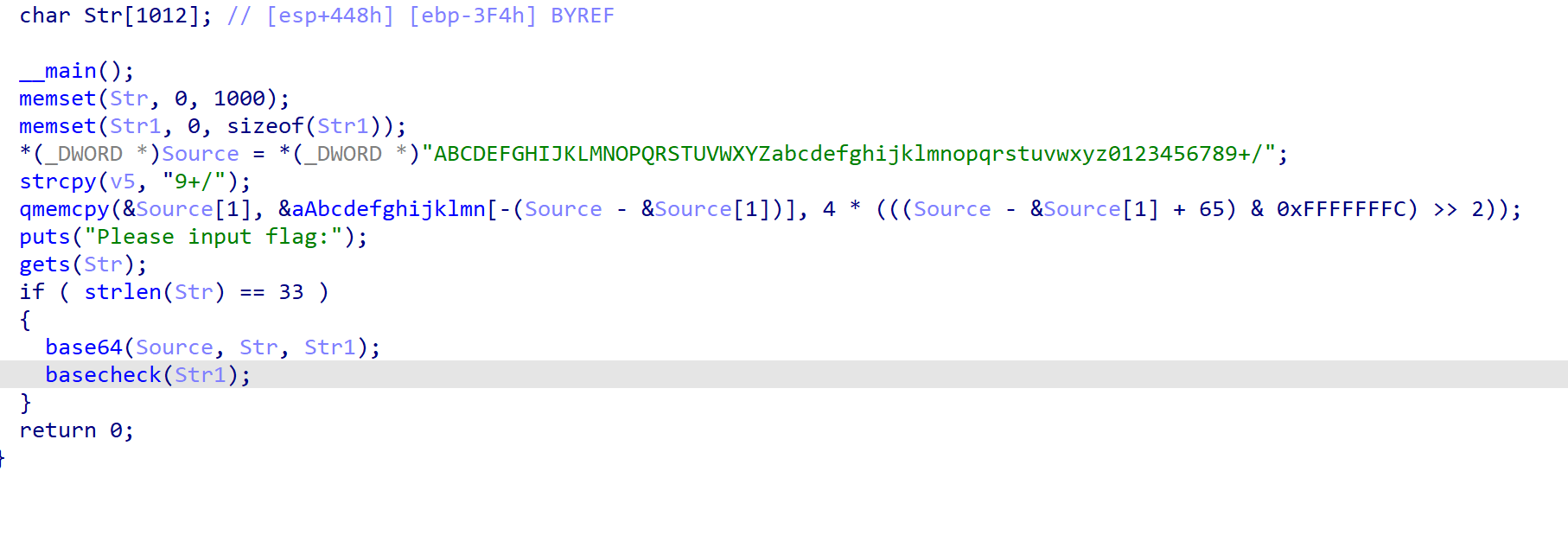
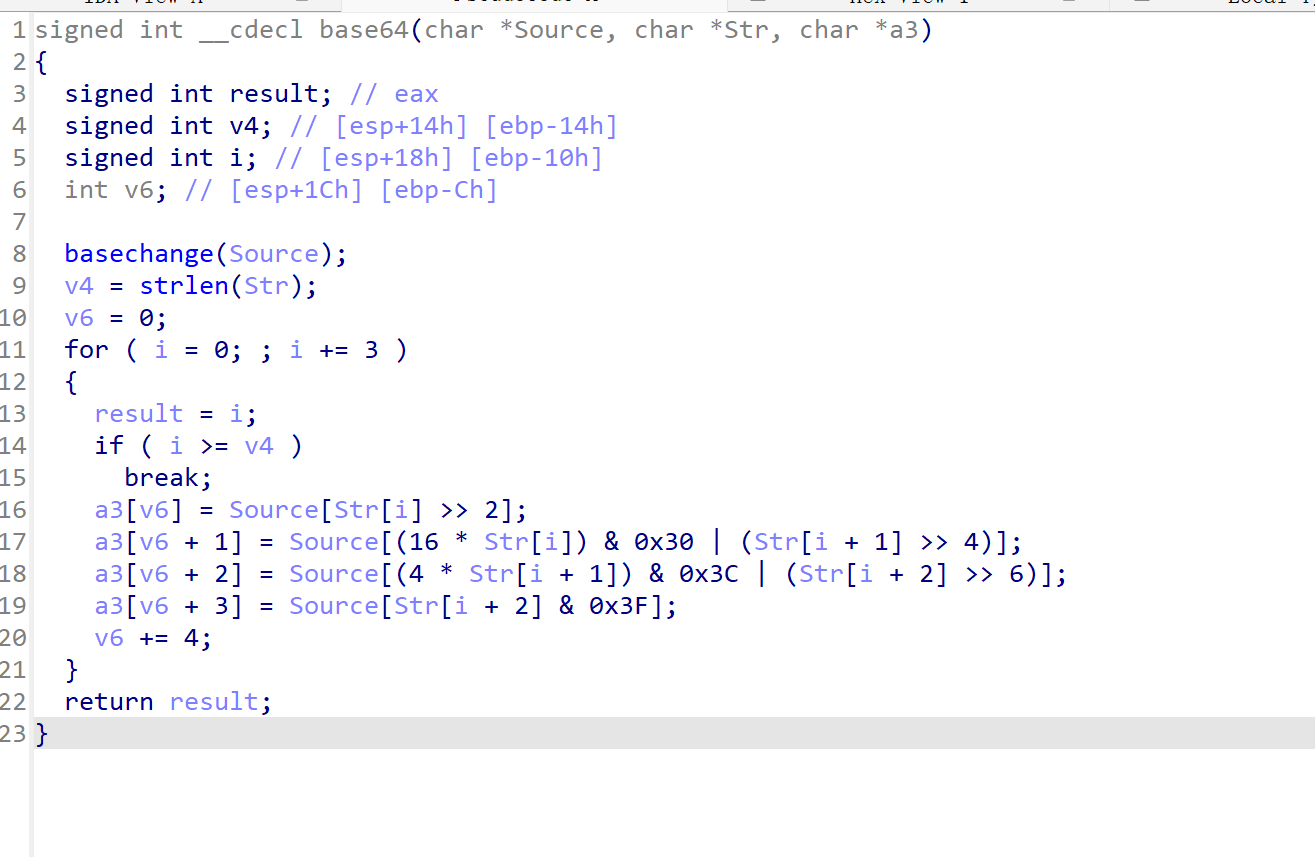
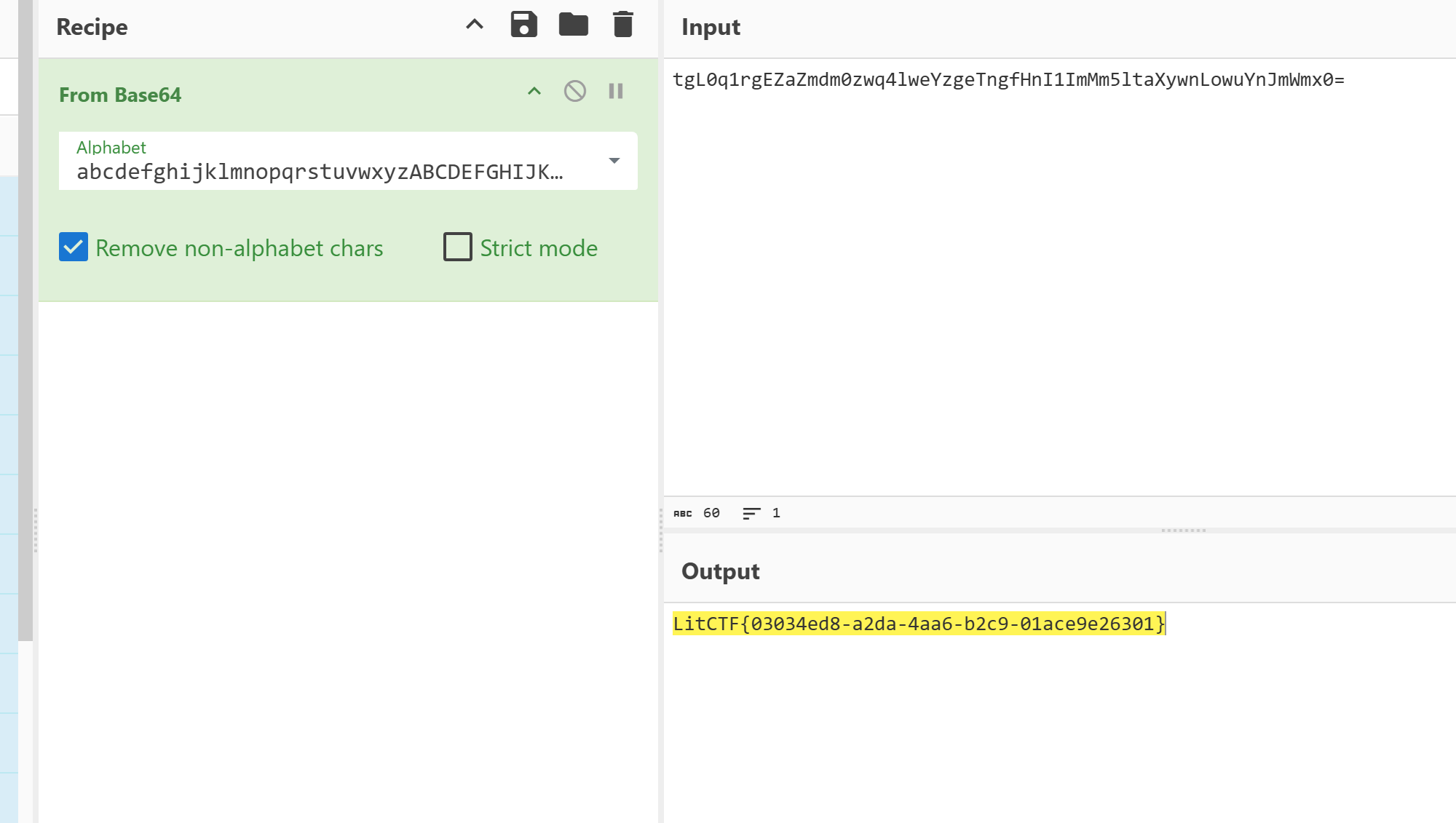
在进行base64加密前先进行basechange,可能进行换表
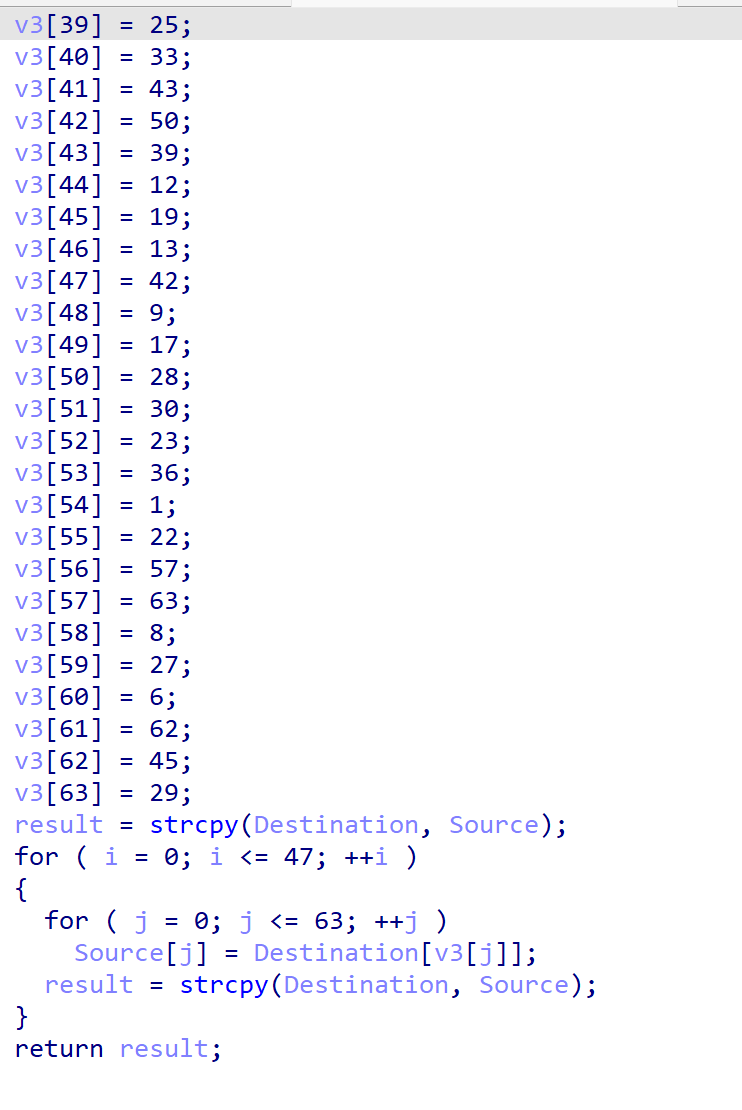
48轮置换
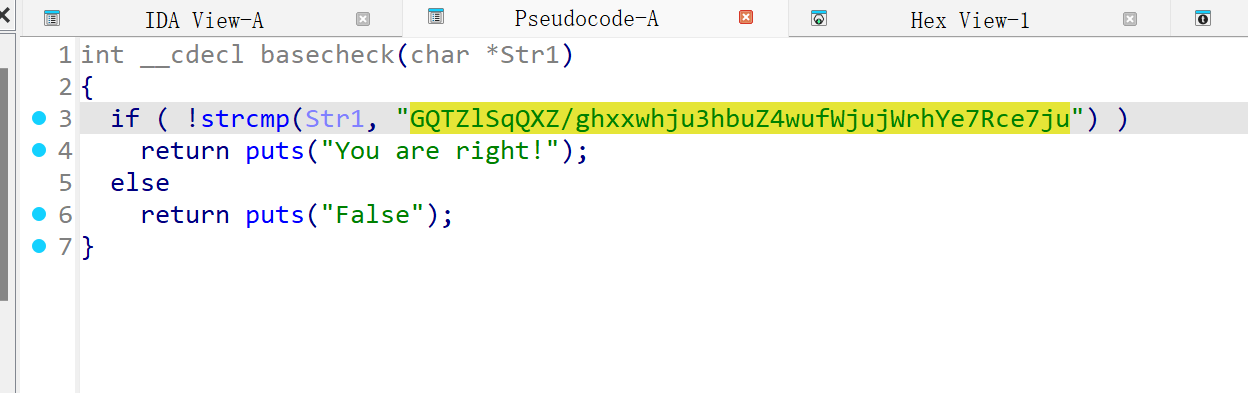
找到密文
找gpt写代码
def simulate_basechange():
# 原始Base64字符表
original = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
# 置换表
v3 = [0] * 64
v3[0] = 16; v3[1] = 34; v3[2] = 56; v3[3] = 7; v3[4] = 46; v3[5] = 2
v3[6] = 10; v3[7] = 44; v3[8] = 20; v3[9] = 41; v3[10] = 59; v3[11] = 31
v3[12] = 51; v3[13] = 60; v3[14] = 61; v3[15] = 26; v3[16] = 5; v3[17] = 40
v3[18] = 21; v3[19] = 38; v3[20] = 4; v3[21] = 54; v3[22] = 52; v3[23] = 47
v3[24] = 3; v3[25] = 11; v3[26] = 58; v3[27] = 48; v3[28] = 32; v3[29] = 15
v3[30] = 49; v3[31] = 14; v3[32] = 37; v3[33] = 0; v3[34] = 55; v3[35] = 53
v3[36] = 24; v3[37] = 35; v3[38] = 18; v3[39] = 25; v3[40] = 33; v3[41] = 43
v3[42] = 50; v3[43] = 39; v3[44] = 12; v3[45] = 19; v3[46] = 13; v3[47] = 42
v3[48] = 9; v3[49] = 17; v3[50] = 28; v3[51] = 30; v3[52] = 23; v3[53] = 36
v3[54] = 1; v3[55] = 22; v3[56] = 57; v3[57] = 63; v3[58] = 8; v3[59] = 27
v3[60] = 6; v3[61] = 62; v3[62] = 45; v3[63] = 29
# 执行48轮置换
current = list(original)
for round in range(48):
new_table = [''] * 64
for j in range(64):
new_table[j] = current[v3[j]]
current = new_table[:]
return ''.join(current)
# 获取最终的字符表
final_table = simulate_basechange()
print(f"原始表: ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/")
print(f"最终表: {final_table}")
# 创建解码函数
def custom_base64_decode(encoded, custom_table):
"""使用自定义字符表解码base64"""
# 创建字符到索引的映射
decode_map = {c: i for i, c in enumerate(custom_table)}
result = []
for i in range(0, len(encoded), 4):
# 获取4个字符对应的6位值
b = [0] * 4
for j in range(min(4, len(encoded) - i)):
if encoded[i+j] in decode_map:
b[j] = decode_map[encoded[i+j]]
# 将4个6位值转换回3个8位字节
byte1 = (b[0] << 2) | (b[1] >> 4)
byte2 = ((b[1] & 0xF) << 4) | (b[2] >> 2)
byte3 = ((b[2] & 0x3) << 6) | b[3]
result.append(chr(byte1))
if i + 1 < len(encoded):
result.append(chr(byte2))
if i + 2 < len(encoded) and encoded[i+2] != '=':
result.append(chr(byte3))
return ''.join(result).rstrip('\x00')
# 使用示例(需要从basecheck获取编码后的字符串)
encoded_flag = "GQTZlSqQXZ/ghxxwhju3hbuZ4wufWjujWrhYe7Rce7ju" # 从basecheck函数获取
flag = custom_base64_decode(encoded_flag, final_table)
print(f"Flag: {flag}")
#原始表: ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
#最终表: gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuND
#Flag: LitCTF{B@5E64_l5_tooo0_E3sy!!!!!}debase64
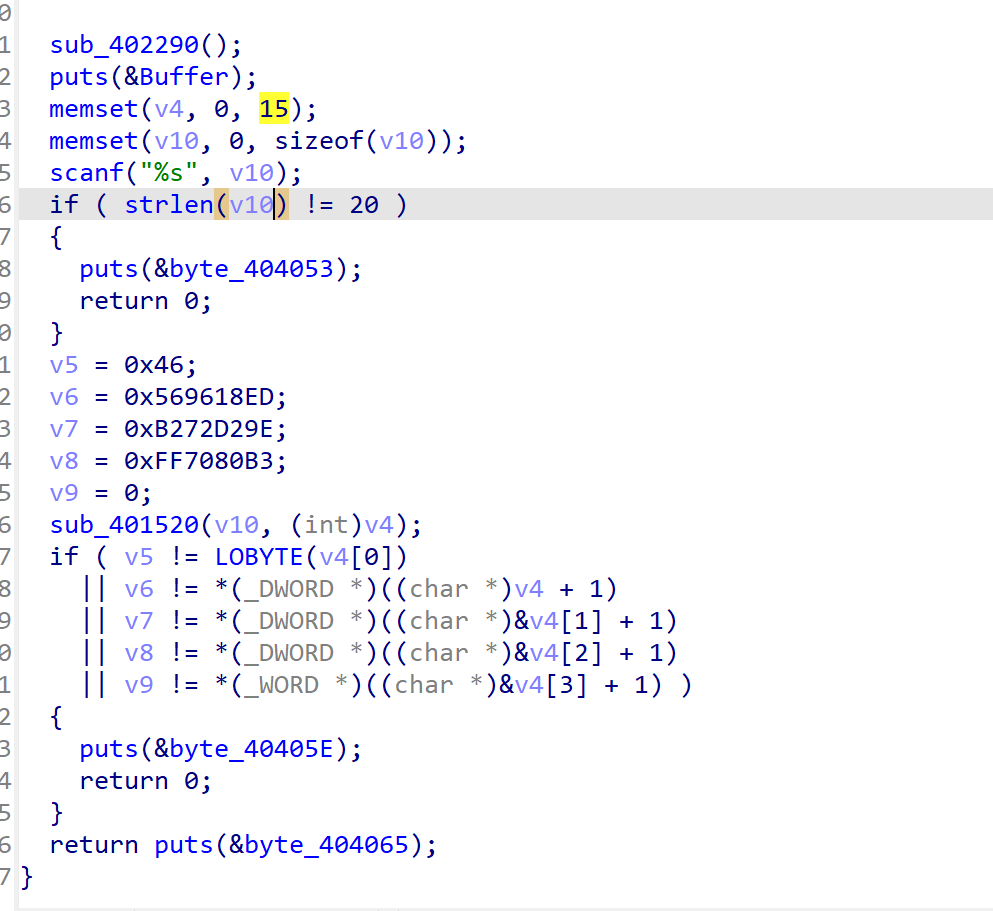
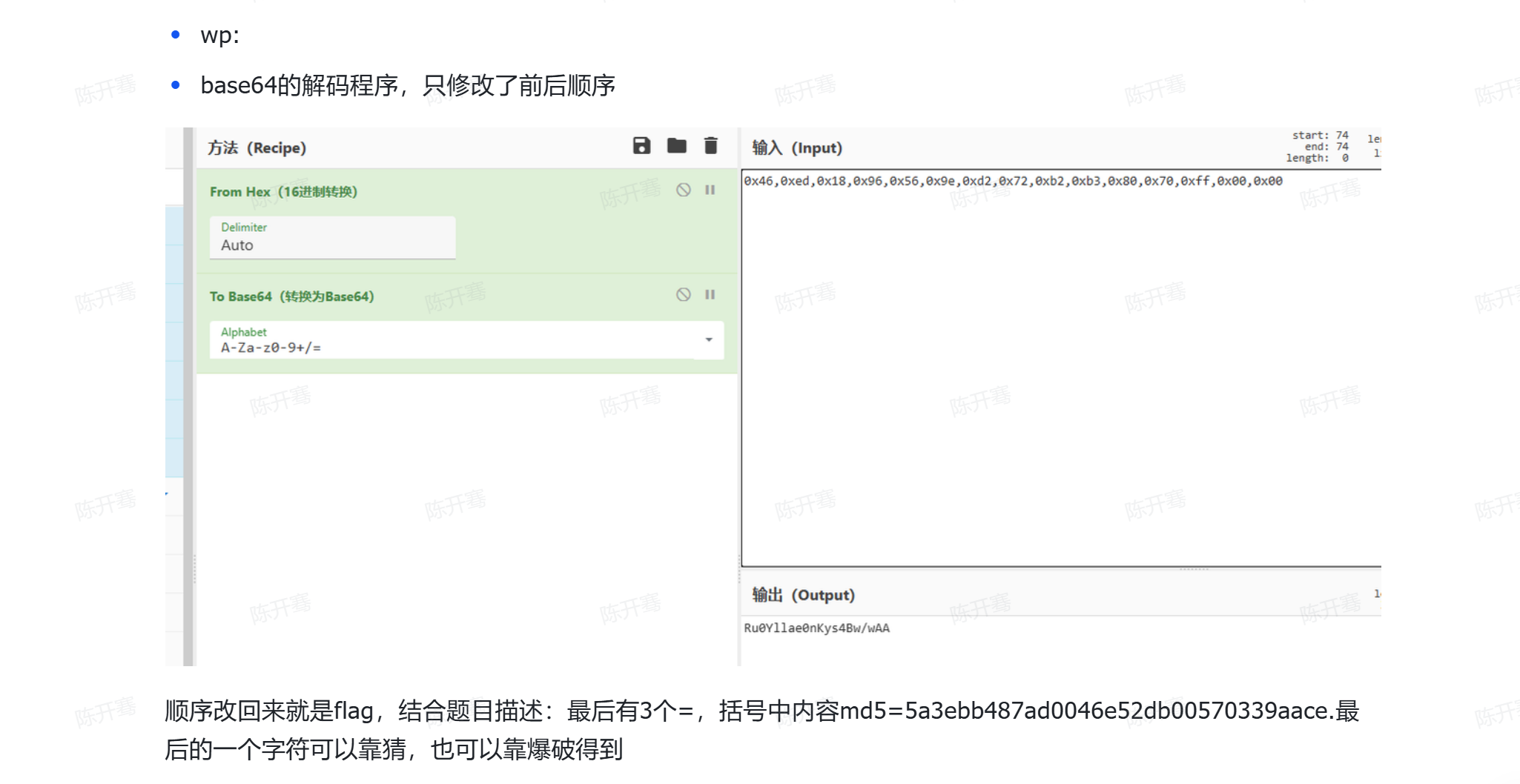
不太懂,哪里来的md5
程序和人有一个能跑就行
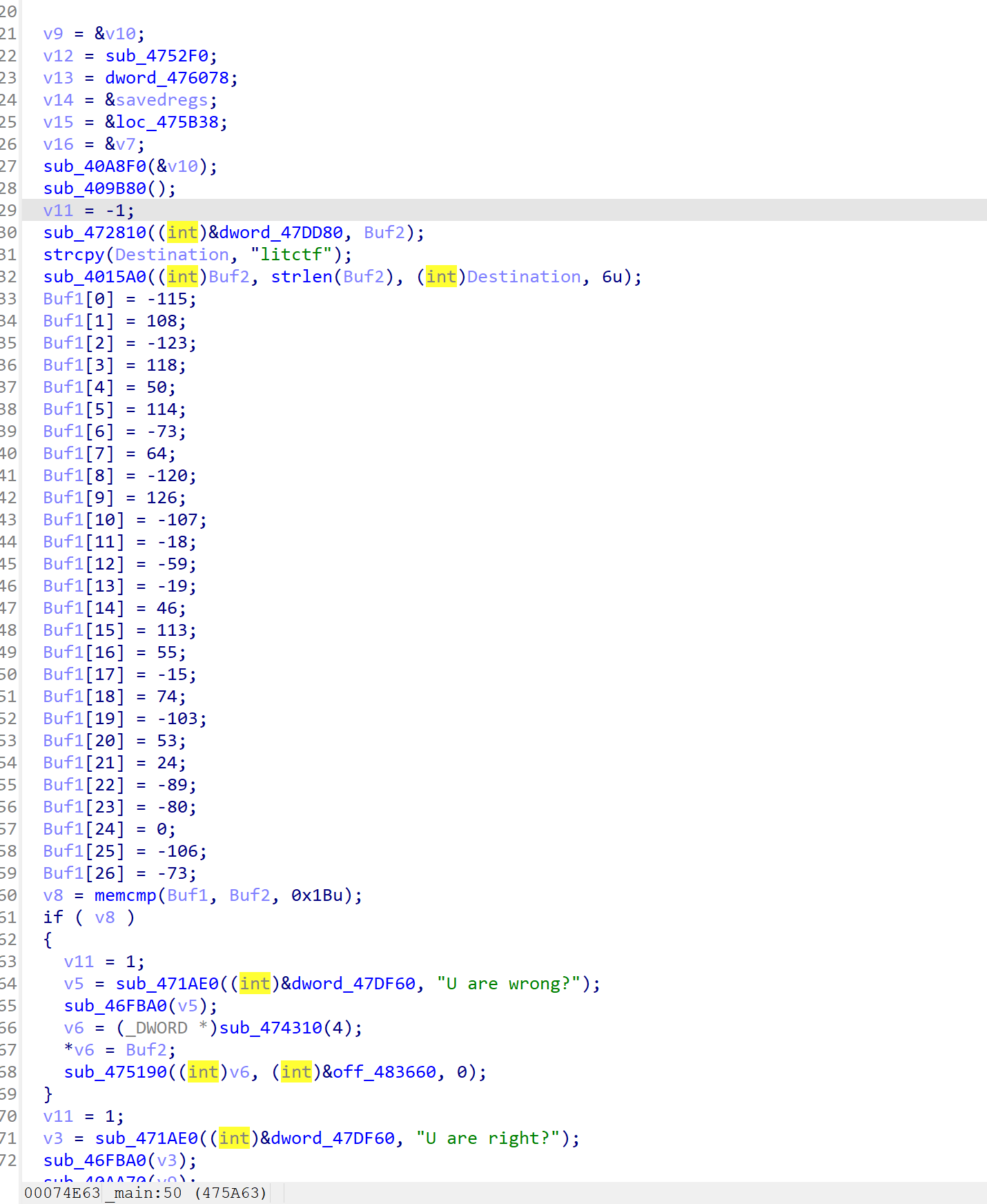
sub_4015a0为RC4,litctf为密钥
但Buf1的数据是假的
wp中写到c++的try catch异常处理,到异常处理地方将真正的enc数据拿到rc4即可
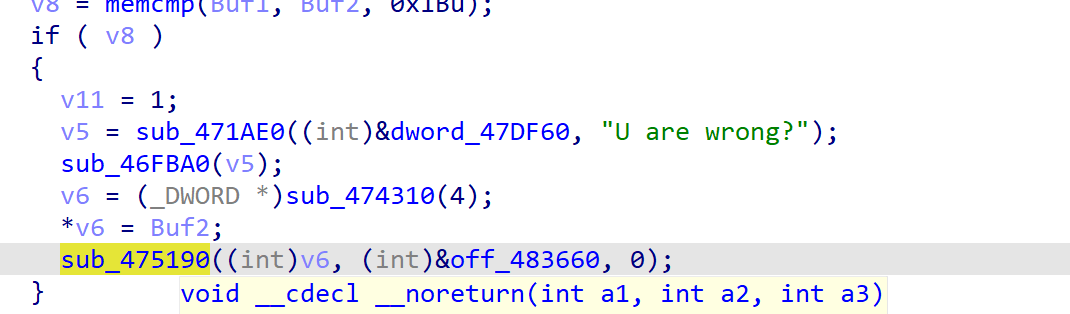
存在问题
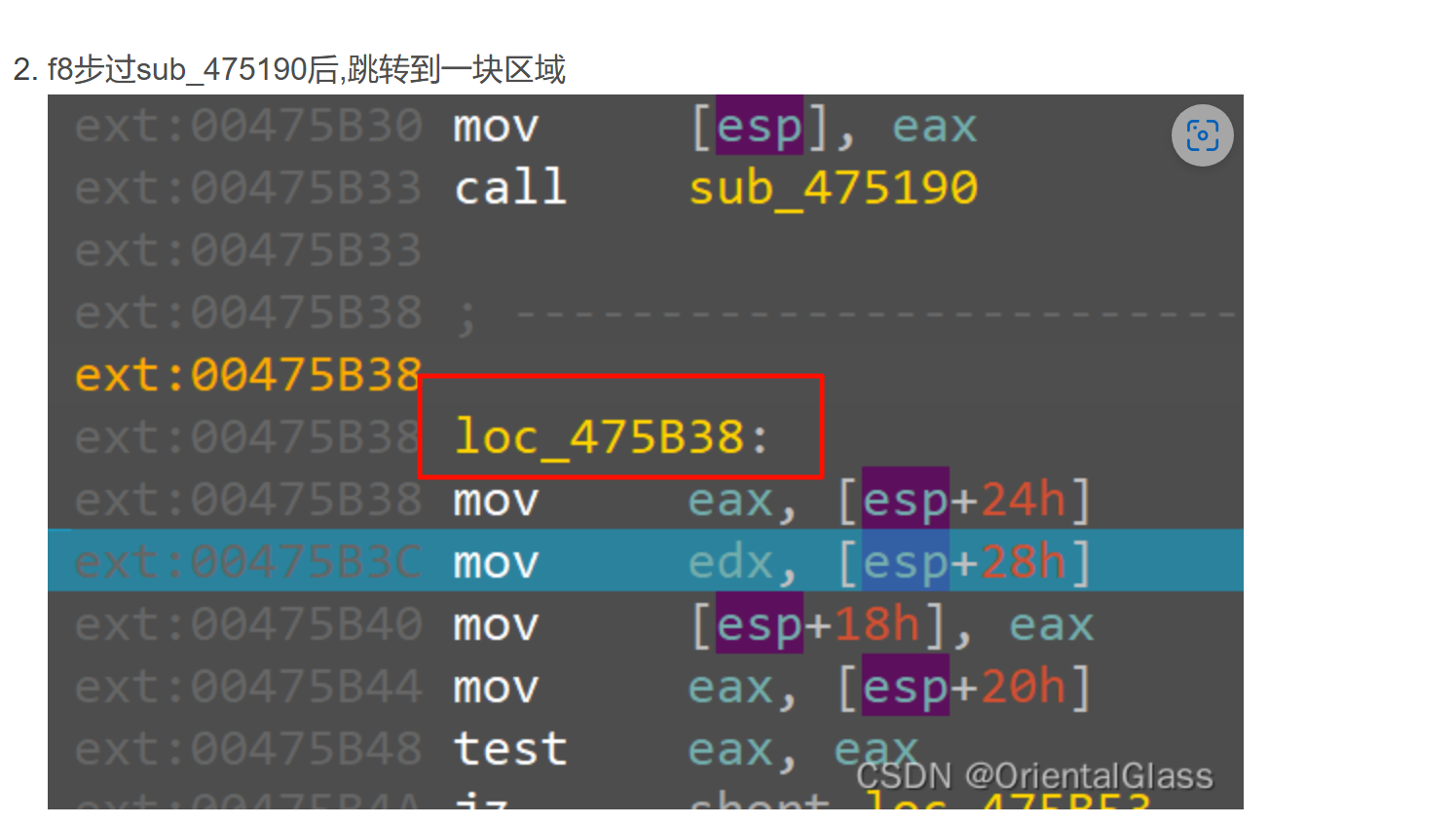
动调找到数据
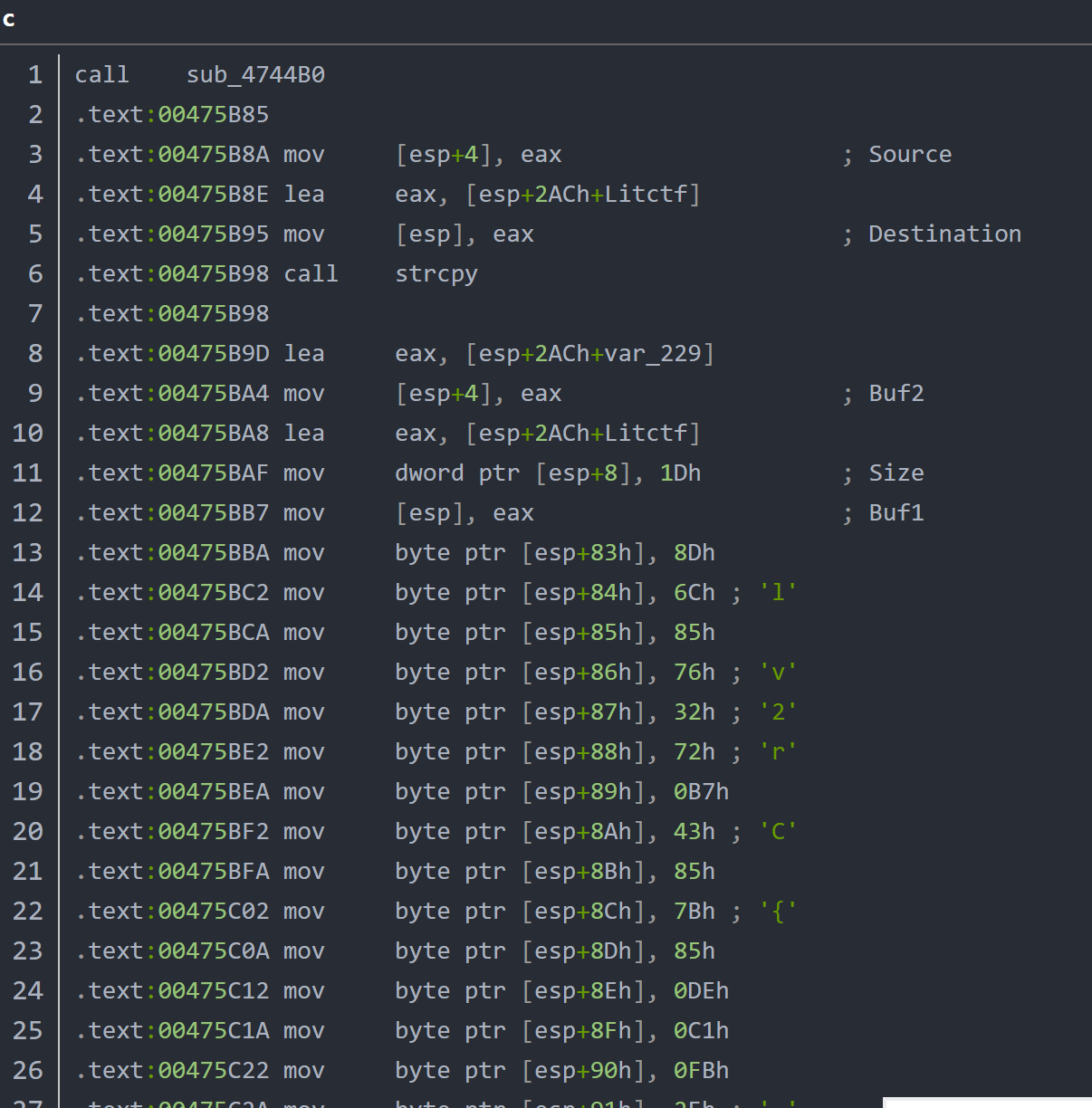
Snake
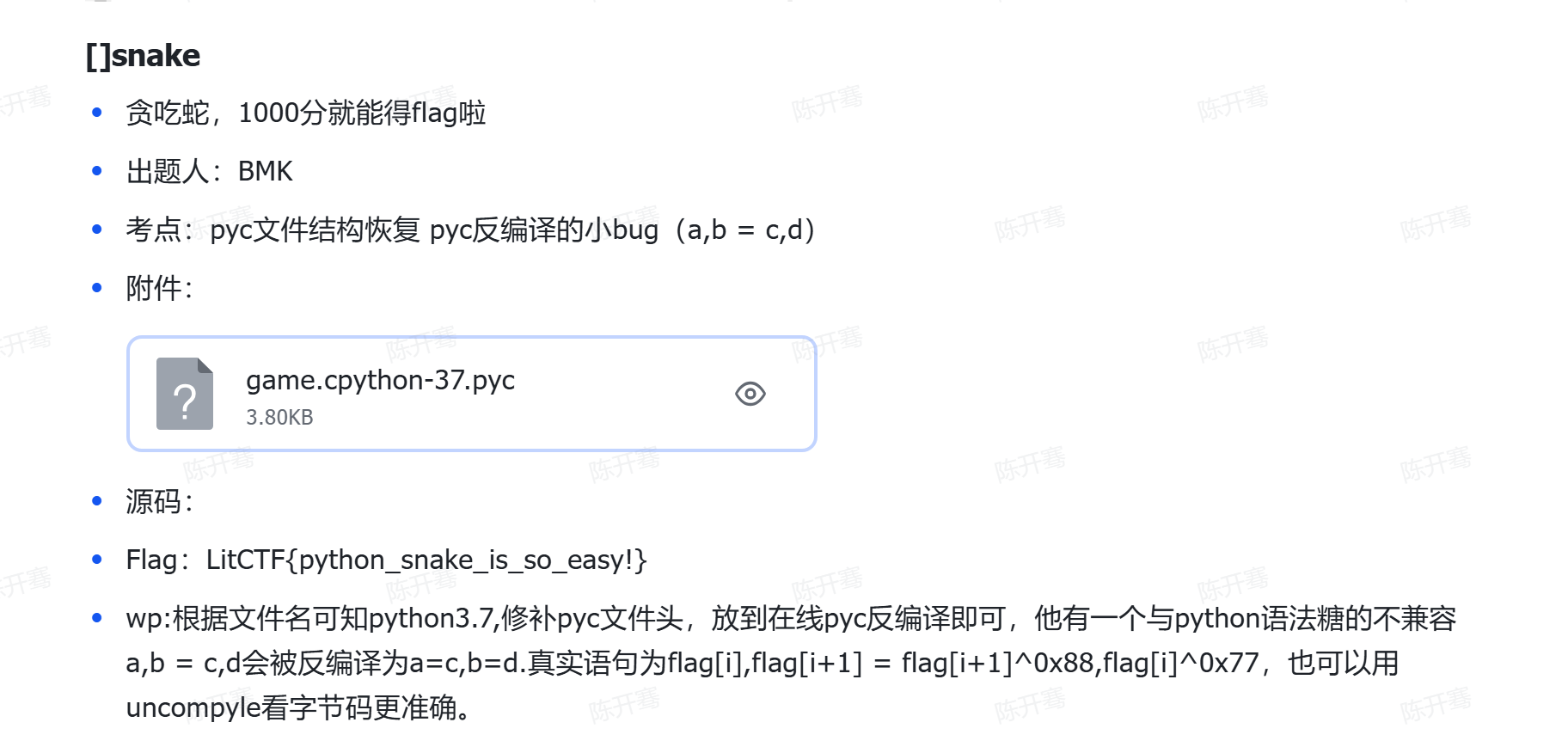
For Aiur
python解包
找到ch.pyc
pycdc反编译
找到flag逻辑
Litctf2024 Re
编码喵
hello_upx
运行使RIP走到程序入口处(detect it easy查看)
esp定律 经过压缩(pushad)和解压(popad)后,oep处的栈顶和入口处的栈顶地址相同
esp指向的内存地址处下一个硬件断点。(寄存器窗口空白处右键)
没试出来
找到个很吊的方法
010打开,把小写upx改为大写UPX
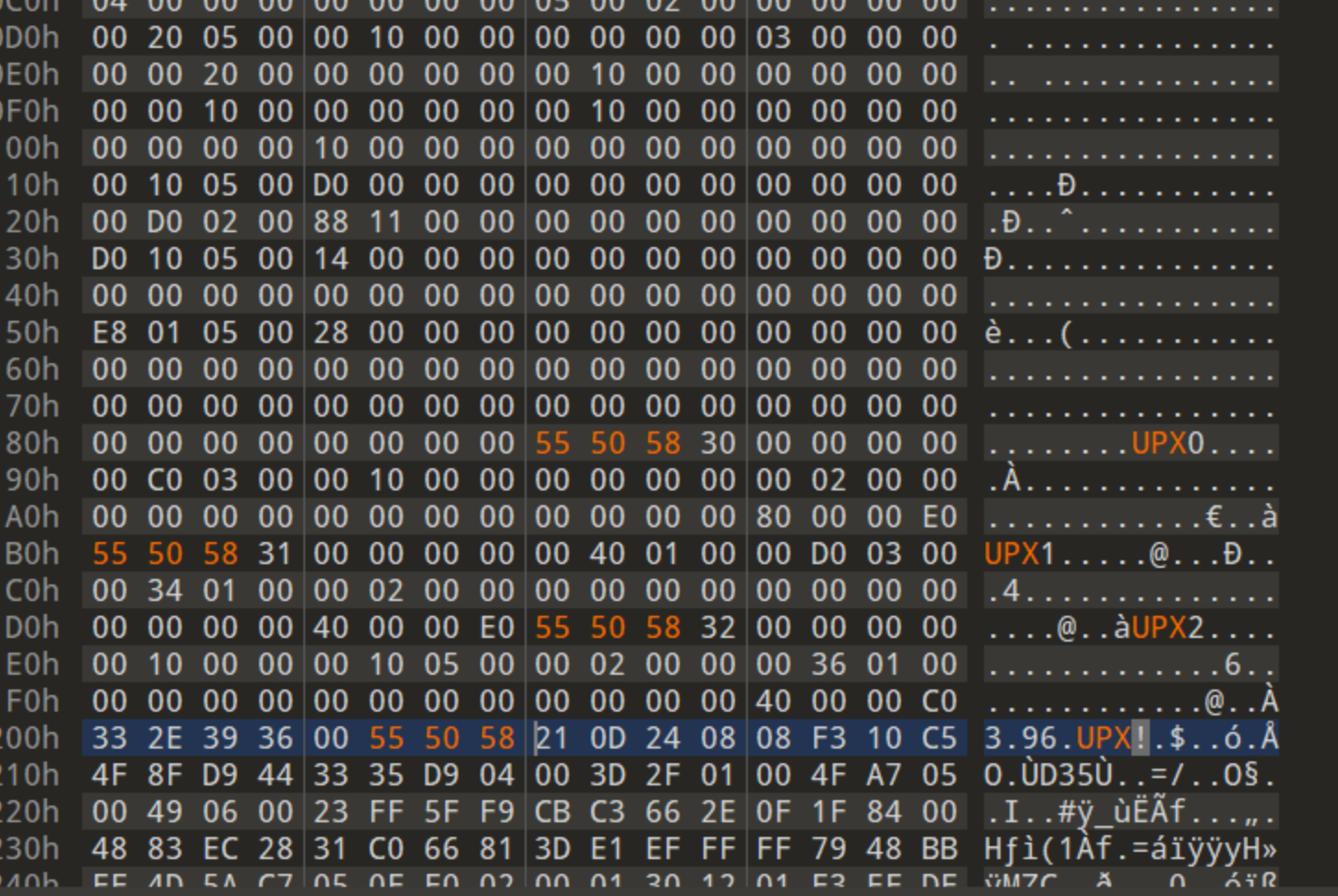
然后就可以upx解压
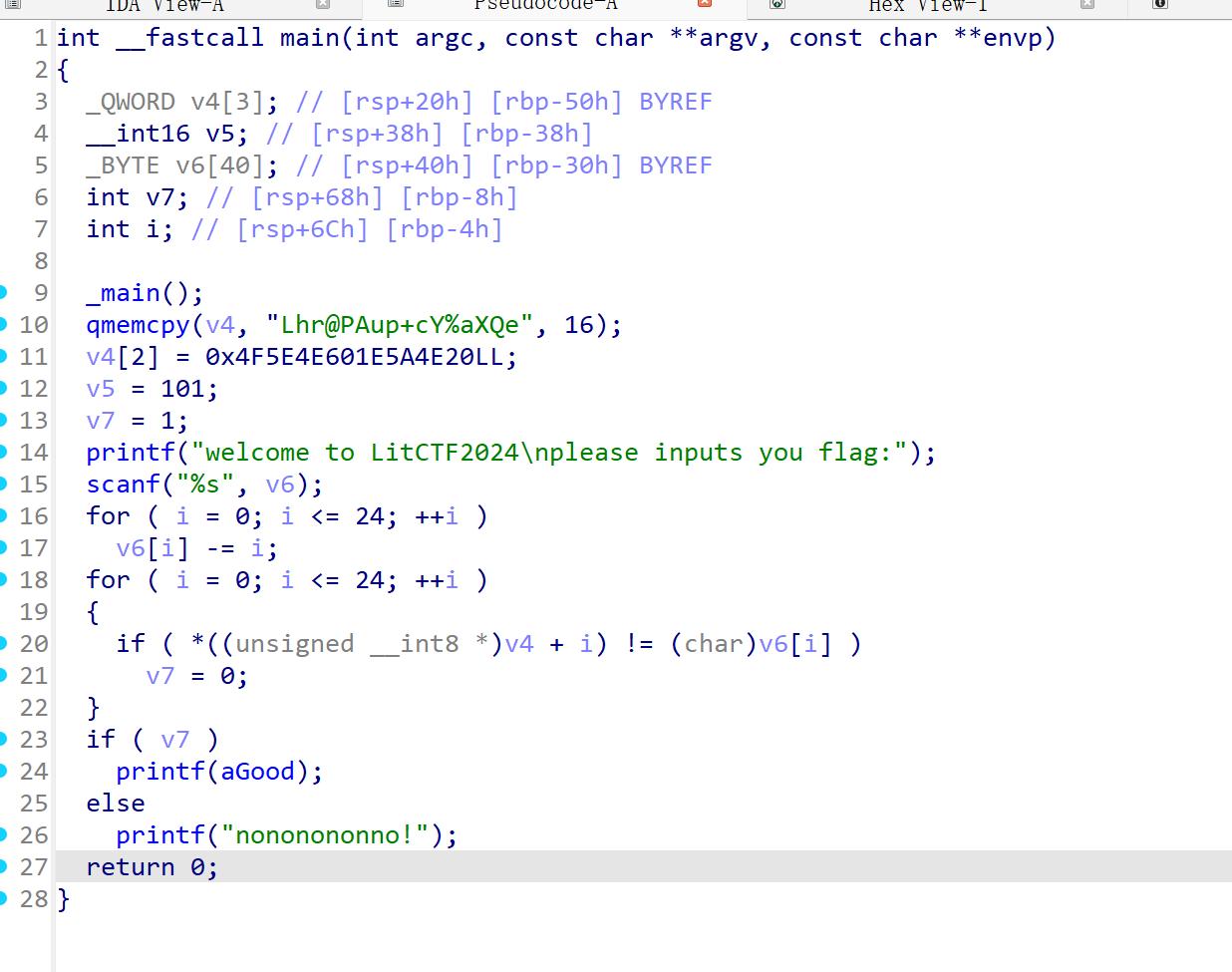
cipher_hex = [
0x4C, 0x68, 0x72, 0x40, 0x50, 0x41, 0x75, 0x70, # "Lhr@PAup"
0x2B, 0x63, 0x59, 0x25, 0x61, 0x58, 0x51, 0x65, # "+cY%aXQe"
0x20, 0x4E, 0x5A, 0x1E, 0x60, 0x4E, 0x5E, 0x4F, # v4[2]的8字节
0x65 # v5 = 101
]
flag = ""
for i in range(25):
flag += chr(cipher_hex[i] + i)
print(f"Flag: {flag}")
# LitCTF{w3lc0me_t0_l1tctf}ezrc4
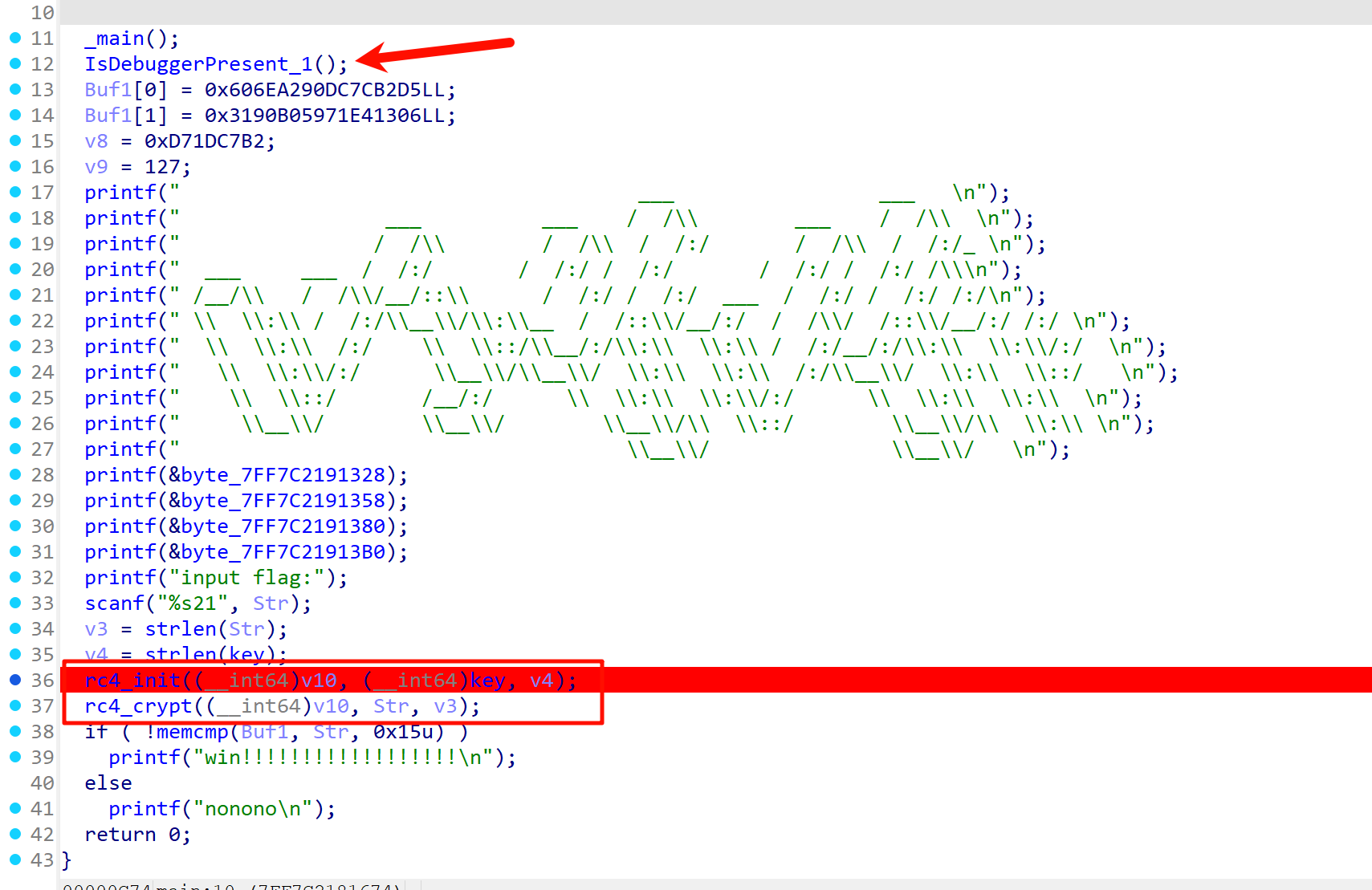
有反调试,看起来是正常的rc4,但实际上有调用X_X函数对key再次加密
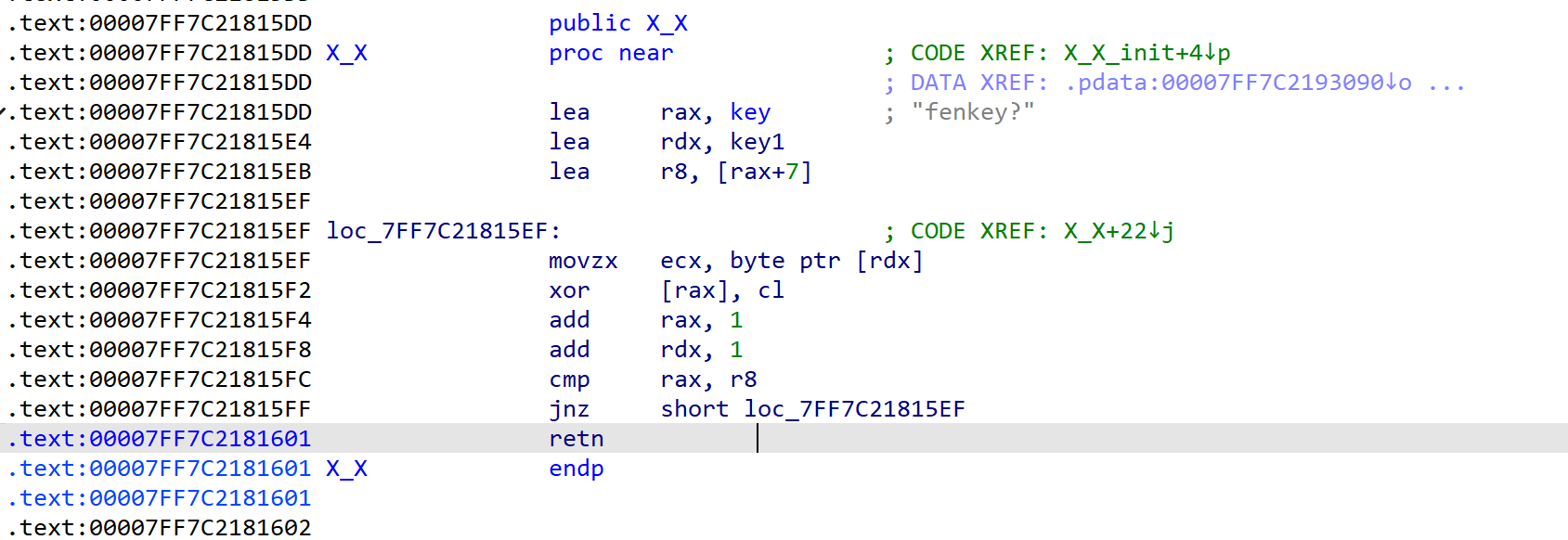
是个异或
key = 'fenkey?'
enc = [0x0A, 0x0C, 0x1A, 0x08, 0x11, 0x1F, 0x1E]
for i in range(len(key)):
print(chr(ord(key[i])^enc[i]),end='')
# litctf!拿到真正密钥
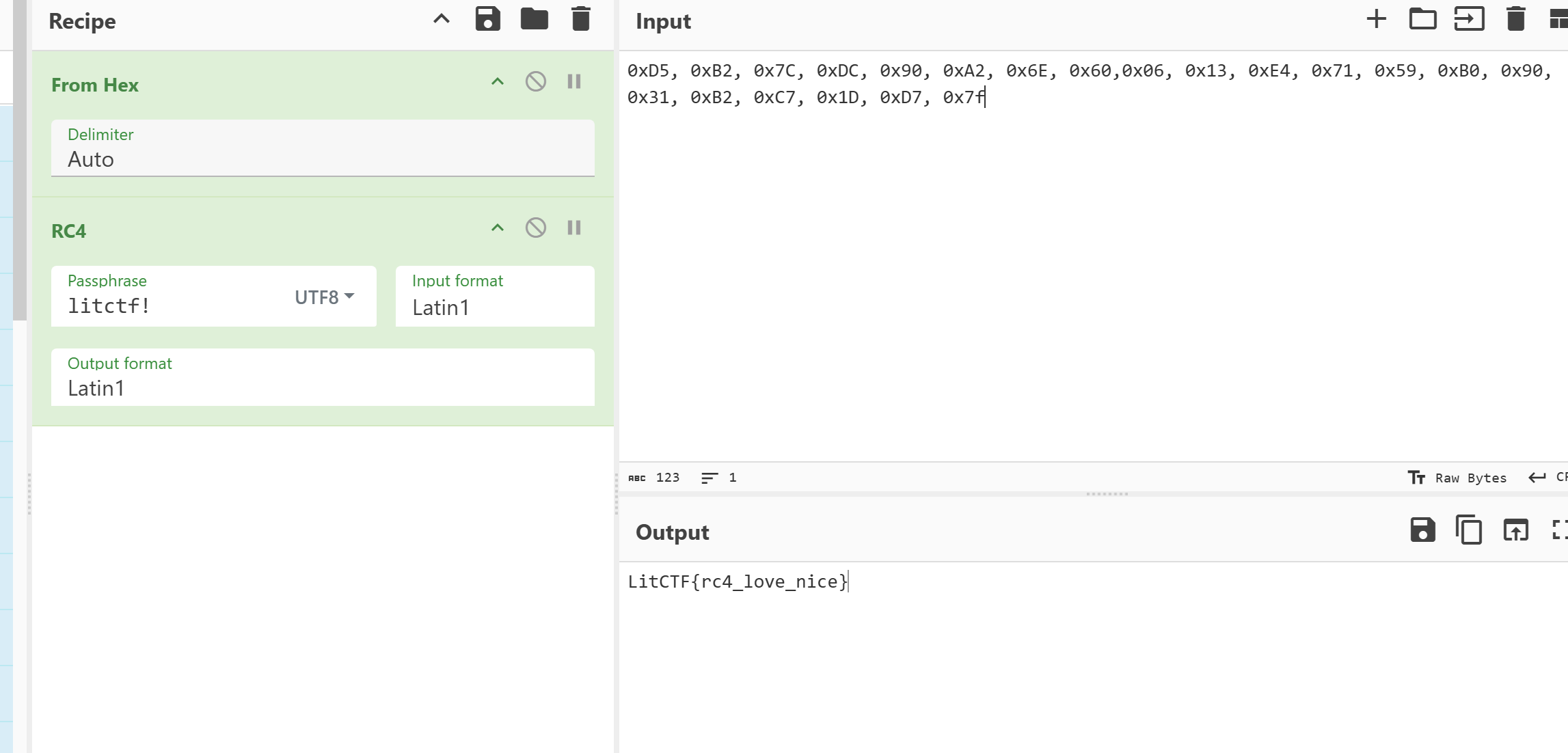
Ezpython
pyinstxtractor解包
把ezpy.pyc反编译
import Litctfbase64
flag = input('flag:')
flag = Litctfbase64.b64decode(flag)
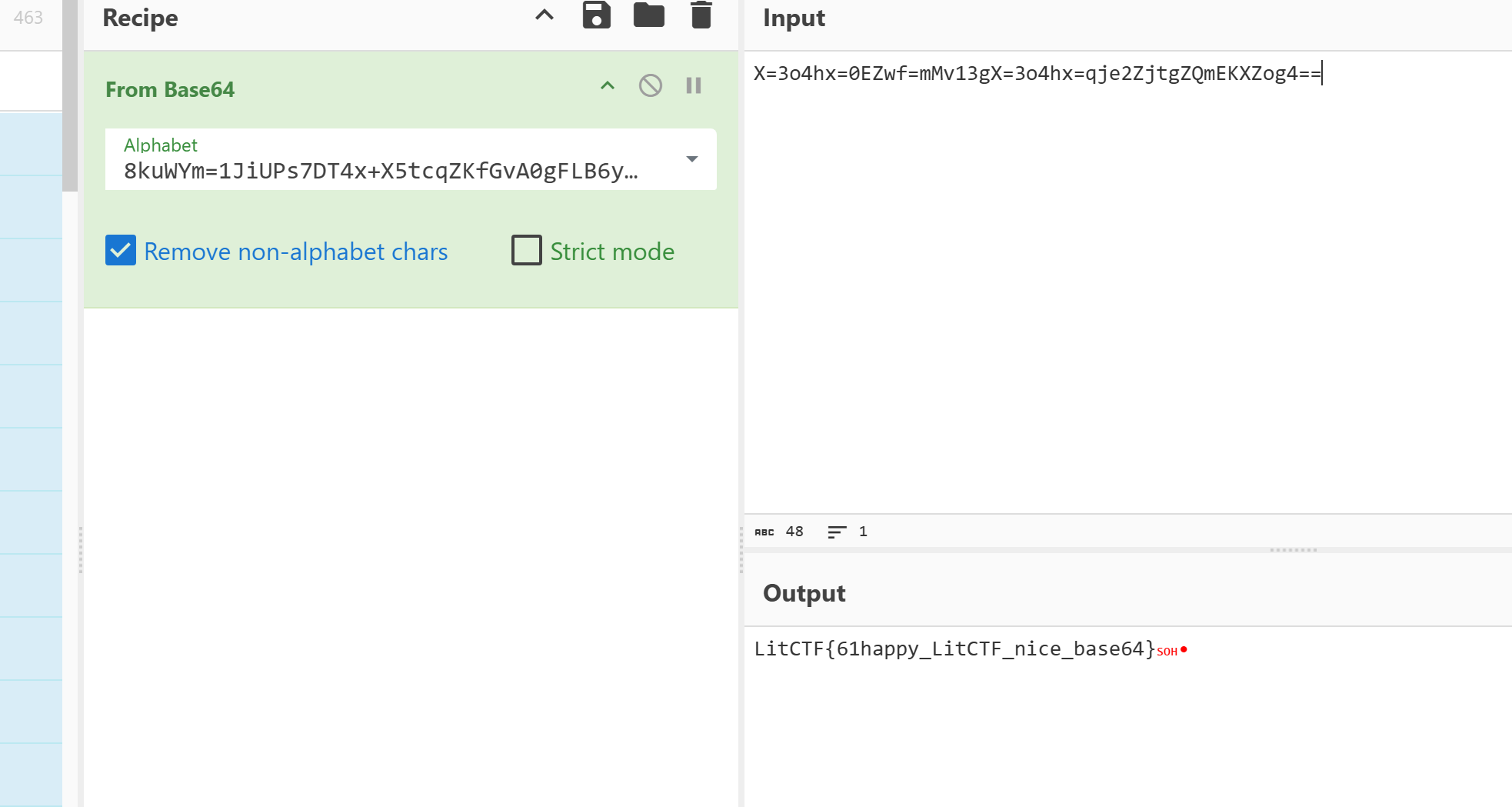
if flag == 'X=3o4hx=0EZwf=mMv13gX=3o4hx=qje2ZjtgZQmEKXZog4==':
print('win')
return None
print('no')继续找到Litctfbase64.pyc
Litctf2023 Re 刷题
https://zer0peach.github.io/2025/08/11/Litctf2023-Re-刷题/